Akira ransomware decryption: Learn the steps to recover your files safely and quickly. Discover the prevention and recovery measures.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
What is Akira ransomware?
Akira ransomware has been an emerging threat in the cybersecurity world since April 2023.
This type of ransomware takes its name from the Japanese animated film of the same name, which tells the story of a futuristic city in the grip of chaos.
Similarly, Akira ransomware wreaks havoc and massive damage on the Linux networks and computer systems of affected organizations.
As reported by The Record Media, there have been 43 exemplary Akira ransomware attacks to date, the most significant of which targeted the South African National Bank.

The ransomware authors then demand a ransom in exchange for the decryption key needed to recover the files.
The Akira ransomware in particular is very sophisticated and aggressive.
This malware spreads through phishing emails, compromised websites, and system vulnerabilities.
What is an Akira file?
When Akira ransomware infects a system, it encrypts files, making them inaccessible to the user.
During the encryption process, files are modified using an algorithm that renders their contents unintelligible without the correct decryption key.
Once the files are encrypted, Akira ransomware generates a ransom message demanding payment in cryptocurrency to obtain the decryption key.
It is important to note that unlike other types of ransomware, files encrypted by Akira malware can become completely unusable without the correct decryption key.
What is the Akira ransomware group?
Akira Ransomware Group is known for creating this highly destructive and aggressive ransomware variant, which is capable of committing multiple cybercrimes by stealing the victim’s data.
Akira has gone so far as to encrypt files on Linux systems as well as the more vulnerable Microsoft systems.
With these strategies, ransomware can cause significant financial damage and operational disruption to affected organizations.
According to SecurityOpenLab, an estimated $30 billion in economic damage will be caused by ransomware attacks in 2023.
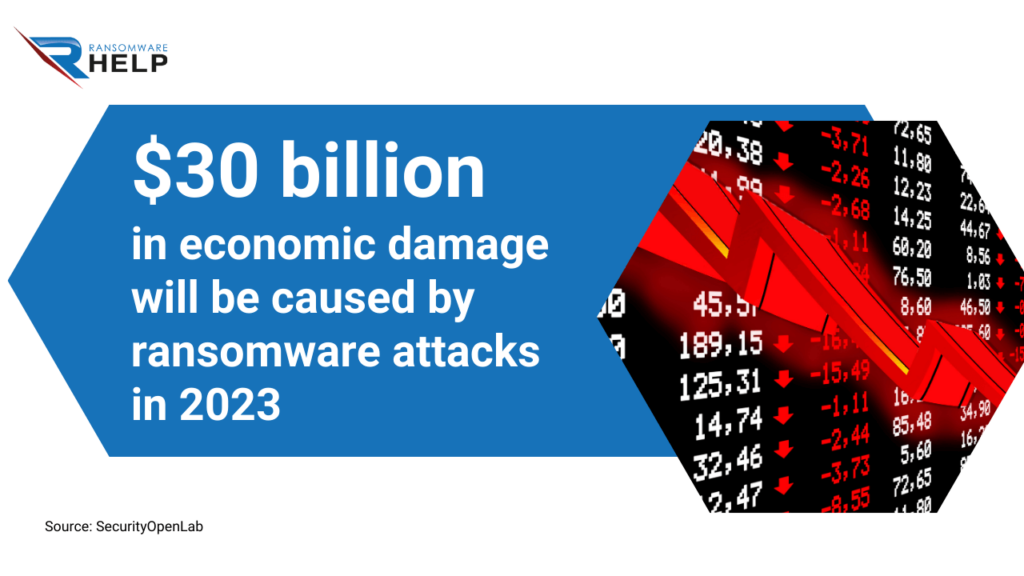
In addition, Akira uses the double extortion technique.
In this strategy, hackers encrypt files by demanding a ransom, and once the ransom is paid, they threaten to post the data online.
Typically, the ransom is demanded in bitcoin or other cryptocurrencies to make it more difficult to detect and track.
How does the Akira ransomware infect your files?
To carry out successful attacks, Akira ransomware uses distribution methods such as phishing emails, software vulnerability exploits, and websites.
This type of malware is designed to encrypt files and block access to your sensitive data, then demand a ransom to restore it.
Again, as in the case of doxing, the threat may spread after the ransom is paid.
Here’s how Akira ransomware can affect your archives:
- Block access to data;
- Loss of sensitive data;
- Disruption of business operations;
- Possible spread of ransomware.
To recover encrypted files as a result of these attacks is a delicate operation that should be carried out by experts in the field.
Who are the Akira ransomware victims?
Akira ransomware can affect a wide range of victims, including individuals and organizations of different sizes and industries.
No one is safe from this increasingly prevalent cyber threat.
According to Cyble‘s analysis:
“Since its appearance in April 2023, Akira ransomware has already compromised 46 publicly disclosed victims, with an additional 30 victims identified in our previous blog post. The majority of these victims are located in the United States.”
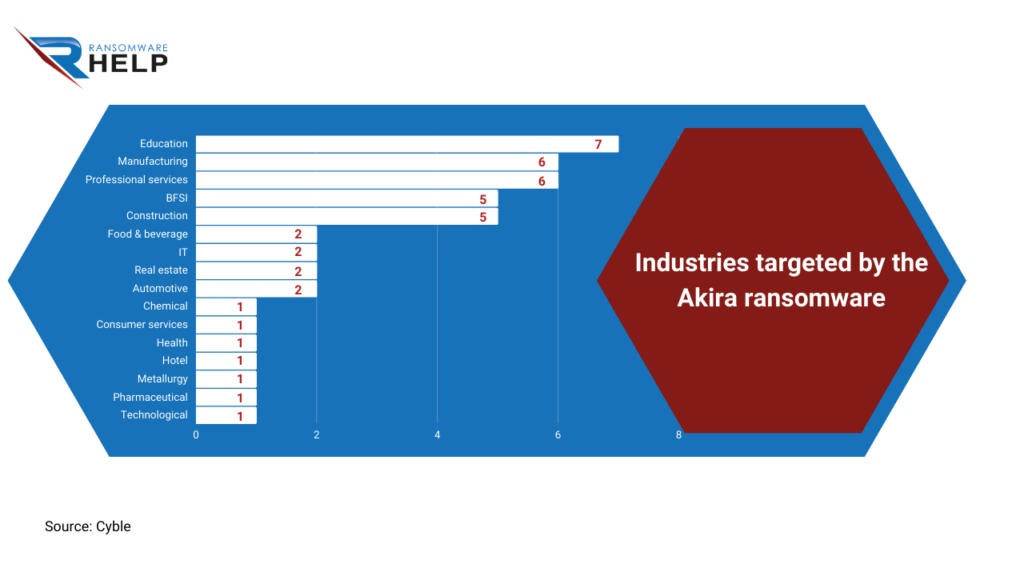
The organizations that have been hit by Akira in these first few months are in the following sectors:
- Education (7);
- Manufacturing; Professional Services (6);
- Banking, Financial Services, Insurance; Construction (5);
- Restaurants; IT; Real Estate; Trucking (2);
- Chemical; Consumer Services; Health; Hotel; Metallurgy, Pharmaceutical; Technological (1).
It seems that no organization is safe from attacks by this new group of ransomware.
All the more reason to have robust ransomware protection on all corporate devices today.
Steps to decrypt your files affected by Akira ransomware
If your archives have been infected with Akira ransomware and your files have been encrypted, it is important to follow a few steps to try to decrypt files without paying the ransom.
According to the Acronis 2022 report, it takes 2-3 days to secure the affected system.

First of all, it is important to isolate the infected archive from the rest of the network to prevent the ransomware from spreading to other connected devices or archives.
Immediately disconnect the infected device or server from the network and, if necessary, shut it down.
Do not attempt to open encrypted files without the assistance of a specialist firm.
Identify the type of ransomware: try to identify the specific type of ransomware that infected your archives.
This information can help determine if there are publicly available decryption solutions or if professional help is needed.
Contact an expert: seek help from a cybersecurity expert or contact a company that specializes in dealing with attacks, such as HelpRansomware.
Check for availability of decryption tools – Some cybersecurity groups and security vendors may have developed free decryption tools.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
Identify the Akira ransomware variant that infected you
If you are an organization that has been attacked by Akira, it is important to try to identify the specific variant of the ransomware that has infected your systems.
If you have received a ransom message from cybercriminals, carefully examine its contents.
Ransom messages usually contain information about the specific name of the Akira ransomware and may include details such as the attackers’ email address or contact websites.
If you have difficulty identifying the Akira ransomware variant, please contact HelpRansomware – by submitting a sample encrypted file, we will be able to determine which ransomware attacked you.
Identifying the Akira ransomware variant that infected you is an important step in understanding the characteristics of the malware and finding the right solutions to mitigate the effects of the attack.
Create an encrypted backup of your Akira ransomware files
If your files have been encrypted by Akira ransomware, it is important that you take the right steps to deal with the situation and protect your data.
One of the most important steps to take, even before data recovery, is to have a proper backup of your encrypted files.
Here are some things to keep in mind when backing up:
- Isolate encrypted files: the first step is to isolate encrypted files from the rest of the system;
- Check availability of decryption services: before proceeding to restore files from backup.
IT security experts advise not to take the initiative, but to contact specialized companies and authorities.
Contact a specialized company
If you have been the victim of an Akira ransomware attack and need professional assistance in dealing with the situation, it is recommended that you contact a company that specializes in dealing with ransomware attacks.
These companies have the experience and expertise to handle ransomware threats and assist with data recovery and damage mitigation.
HelpRansomware is the number one company in the world dedicated to providing support and consulting services to victims of ransomware attacks.
Here are some of the benefits of choosing HelpRansomware:
- Situation assessment;
- Personalized advice;
- Data recovery;
- Future prevention.
Our team of cybersecurity experts includes highly trained professionals with specific experience in fighting all variants of ransomware, including Akira.
Preventive measures to protect against Akira ransomware
To protect yourself from ransomware like Akira, you need to take solid preventive measures to mitigate the risk of an attack and minimize the impact on your data and operations.
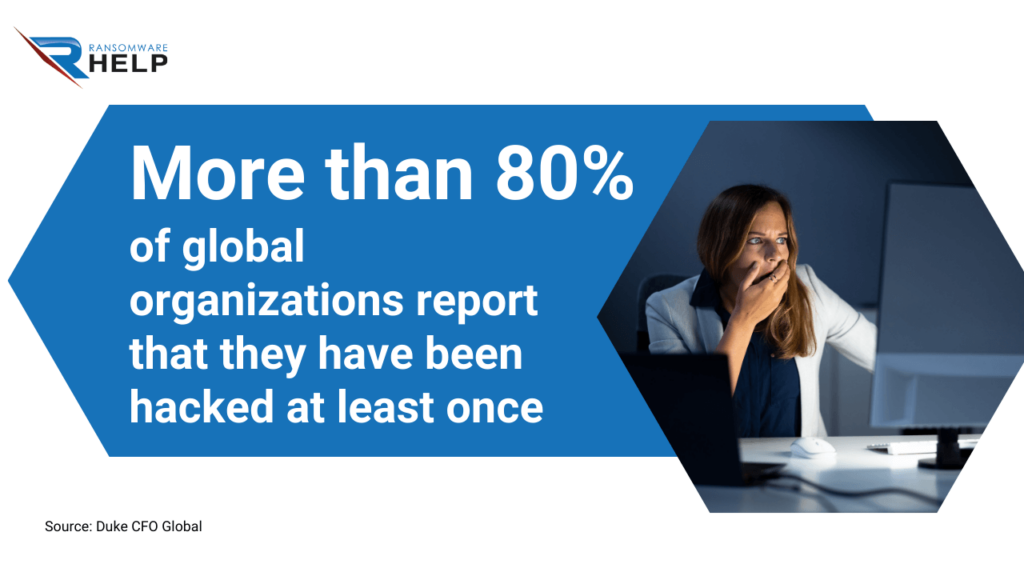
According to a Duke CFO Global survey, more than 80% of global organizations report that they have been hacked at least once.
Here are some easy-to-follow tips:
- Awareness and training: train employees regularly on cybersecurity practices, including ransomware awareness;
- Regular Updates: always keep the operating system, software, and applications in use up to date;
- Regular Data Backups: make regular backups of your data to a separate and offline location, such as an external storage device or cloud storage service;
- Firewalls and antivirus: these tools can detect and block suspicious activity, preventing access to viruses;
- Email and Web filtering: use email and Web filtering solutions to block suspicious traffic and phishing messages.
Statistics on computer attacks show that companies are highly exposed to this phenomenon and must take preventive measures.
Keep software and operating systems up to date
One of the cornerstones of effective protection against Akira ransomware and other cyber threats is keeping your software and operating systems up to date.
Regular updates ensure that your devices are protected against known vulnerabilities and that any necessary fixes have been applied.
One solution is to set authoritative security patches.
Software developers and operating system vendors regularly release security patches to address known vulnerabilities.
This was the case with the Wannacry ransomware, which infected Microsoft Windows computers on a massive scale in 2017.
In fact, vulnerabilities in software and operating systems can be exploited by attackers to infiltrate devices and launch ransomware attacks.
In some high-risk industries, such as healthcare, organizations must comply with specific data security regulations.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
Avoid clicking suspicious links or attachments
One of the most common tactics used by Akira ransomware and other malware is to send suspicious links or attachments via email or SMS.
These are social engineering techniques known as phishing and doxing and their variants, which vary depending on the means of communication.
Avoiding clicking on such links or opening suspicious attachments is an important measure to prevent ransomware infection.
Before opening any link or attachment, double-check the source of the email or message.
According to the Acronis report, there were 21 million malicious URLs in the first half of 2022: 58% were sent via email.

Check if you know the sender or if the message seems legitimate.
Phishing emails are a common method used by cybercriminals to trick victims into revealing sensitive information or installing malware.
Make sure you have adequate protection on your device and keep your virus definitions up to date to ensure maximum effectiveness in detecting and preventing threats.
The only way to protect yourself from ransomware is to adopt good cyber defense practices.
Use a trusted security solution to protect against Akira ransomware
To effectively protect yourself from Akira ransomware and other cyber threats, it is essential to use a reliable security solution.
Advanced antivirus and antimalware software can play a crucial role in detecting and preventing ransomware.
As reported by VPN Alert, 8.9% of users who installed free antivirus software were still hit by ransomware last year.
The percentage drops to 7.4% when looking at users with paid plans.

Make sure your security solution provides real-time protection against all types of ransomware, including the latest variants such as Akira.
The ability to detect and block attacks in real time is critical to preventing infection and mitigating the impact of ransomware.
The threat is more real than ever and needs to be properly addressed.
If you have a variety of devices, such as desktops, laptops, tablets, and smartphones, choose a security solution that offers multi-device protection.
Effective tools and methods for decrypting Akira ransomware
To restore encrypted files by Akira ransomware can be a complex task, but there are some tools and methods that can be effective.
Basically, you have two options.
If you are a person with a technical knowledge base in information technology and cybersecurity, you might choose to use decryption tools.
However, this is a risky attempt because you might be able to eliminate the ransomware but not recover the files.
The other option, on the other hand, is much safer and has obvious long-term benefits.
It involves contacting a company that specializes in ransomware recovery.
HelpRansomware, with its decades of experience against ransomware, is the only company in the world capable of decrypting files encrypted by any type of ransomware.
Paying the ransom is never an option.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
Use the free decryption tools for Akira ransomware
If you are a victim of Akira ransomware and are looking for ways to decrypt your encrypted files without paying the ransom, it can be useful to explore the available free decryption tools.
There are websites and online forums that focus mainly on developing ransomware decryption tools.
The No more ransom platform is one of the most comprehensive for identifying ransomware and providing free decryption tools.
Some of these tools may include decryption capabilities for some variants of ransomware, including Akira ransomware.
Keep in mind that using the free decryption tools does not always guarantee complete recovery of encrypted files.
Hire decryption experts to recover your files encrypted by Akira ransomware
The priority in this case is to find reputable decryption experts with specific experience in remove ransomware.
Choose a company like HelpRansomware, which has years of experience in IT security and can therefore offer you a guaranteed service.
If you think such a service is expensive, you are not considering what a ransomware attack really costs your business or in terms of damage to your online reputation.
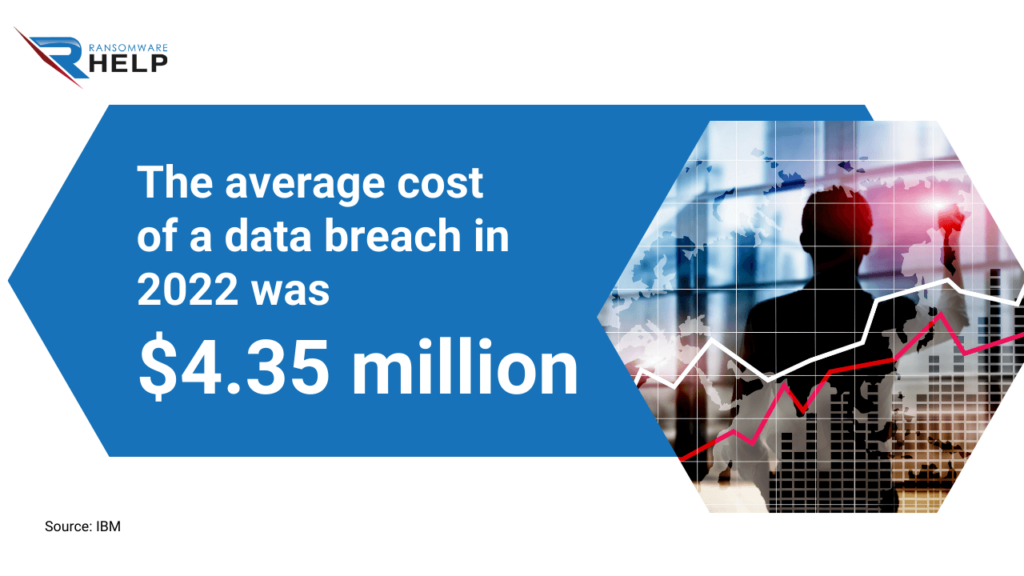
According to the IBM report, the average cost of a data breach in 2022 was $4.35 million.
So in other cases, on top of the huge economic damage, there is also reputational damage.
This is what happened to Whitworth University when its systems were disrupted for over a month following a ransomware attack.
Expert intervention is therefore essential not only for recovering a company’s or organization’s data, but also for managing its future security.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
Additional recommendations for Akira ransomware attack recovery
In addition to taking steps to decrypt ransomware files and hiring decryption experts, there are other recommendations to follow when recovering from an Akira ransomware attack:
- Isolate and disconnect the infected system;
- Restore the system from backup;
- Improve security and implement preventive measures;
- Monitor for suspicious activity;
- Seek legal advice.
By following the best practices listed above, you can avoid encountering the less aggressive versions of ransomware attacks, if at all.
The most important weapon at your disposal remains knowledge and good cybersecurity awareness.
Educate your employees and stay up to date on the latest ransomware releases, and don’t underestimate this threat.
Change all passwords after decrypting files
After successfully completing the decryption process of files encrypted by Akira ransomware, it is imperative to change all passwords immediately.
This extra precaution is essential to ensure the security of your data and prevent any unauthorized access or future cyber attacks.
According to a survey by PCloud, 90% of internet users worry that their passwords could be hacked.

Choose strong, complex passwords that include upper and lower case letters, numbers, and symbols, and avoid dates such as your birthday.
Also, try to use a different password for each account you use.
Start by changing the passwords for accounts that contain sensitive information or have privileged access.
Implement additional security measures to help prevent future ransomware attacks
Here are some strategies that may be useful for implementing other defenses:
- Update software regularly: keep all software, including the operating system, antivirus programs, web browsers, and applications, up-to-date with the latest security patches;
- Use reputable security solutions: install and use reputable antivirus and anti-malware software on all devices;
- Enforce execution restrictions: set restrictions on user accounts to limit the execution of unauthorized software;
- Filter network traffic: implement security filters to block suspicious or malicious network traffic, including websites known to distribute malware;
- Incident response planning and testing: develop an incident response plan that outlines actions to take in the event of a potential ransomware attack.
The best way to combat ransomware is to be proactive.
By doing so, you can protect yourself before and after an attack and avoid serious losses if your systems are affected.
Conclusions
Akira ransomware is an emerging threat in the cybersecurity world, attacking Linux systems since April 2023.
In this article, we have explained all the strategies to defend yourself against the Akira virus and decrypt the affected files.
Here are the conclusions you can draw from reading this text:
- To date, there have been 43 exemplary Akira ransomware attacks, the most notable of which was on the South African National Bank;
- An estimated $30 billion in economic damage from ransomware attacks in 2023;
- The majority of Akira ransomware attacks have targeted the education sector;
- It takes 2 to 3 days to secure an affected system;
- More than 80% of global organizations report having been attacked by hackers at least once;
- 8.9% of users who have installed a free antivirus have still been attacked by ransomware; the percentage drops to 7.4% if we consider users who have paid plans;
- In the first half of 2022, there were 21 million malicious URLs: 58% were sent via email.
If you have problems with Akira ransomware, contact HelpRansomware, the world leader in decrypting and recovering data damaged by ransomware.
Hiring professionals is always the best idea if you want to be sure that the ransomware will be deleted and all files will be recovered.



