In questo articolo di HelpRansomware, scoprirai tutto sugli attacchi ransomware, le sue varianti e come eliminarlo.

Esperti nella Rimozione di Ransomware
Affidati ai nostri professionisti certificati: oltre 25 anni di esperienza nel campo della rimozione di ransomware, recupero dati e sicurezza informatica.
Nel 2017, l’Internet Crime Complaint Center (IC3) dell’FBI ha ricevuto 1.783 denunce di ransomware che sono costate alle vittime oltre 2,3 milioni di dollari.
Queste denunce, tuttavia, rappresentano solo gli attacchi segnalati a IC3.
Il numero effettivo di attacchi ransomware e i costi sono molto più alti: solo lo scorso anno si sono verificati circa 184 milioni di attacchi ransomware.

Il ransomware era originariamente destinato a prendere di mira gli individui, che ancora oggi costituiscono la maggior parte degli attacchi.
In questo articolo, esamineremo la storia del ransomware dal suo primo attacco documentato nel 1989, sino ai giorni nostri.
Ti mostreremo nel dettaglio alcuni degli attacchi e delle varianti ransomware più significative.
Infine, daremo uno sguardo all’evoluzione futura e alle soluzioni ransomware.
Cos’è il ransomware?
Capire cos’è il ransomware è molto semplice: parliamo di un malware o software dannoso che si impossessa di file o sistemi e ne blocca l’accesso agli utenti.
Quindi, tutti i file, o anche interi dispositivi, vengono tenuti in ostaggio utilizzando la crittografia finché la vittima non paga un riscatto in cambio della chiave di decrittazione.
Da decenni oramai si sono sviluppati diversi tipi di ransomware, e le sue varianti sono diventate sempre più avanzate nelle loro capacità di diffondere, eludere il rilevamento, crittografare i file e costringere gli utenti a pagare il riscatto.

Questo significa, in estrema sintesi, che gli attacchi ransomware sono diventati più pericolosi e dannosi per le vittime.
Come funzionano gli attacchi ransomware
Ora che abbiamo una definizione di ransomware, procediamo con un resoconto più dettagliato di come questi programmi dannosi ottengono l’accesso ai file e ai sistemi di un’azienda.
Il termine “ransomware” descrive la funzione del software, che è quella di estorcere utenti o aziende a scopo di lucro.
Tuttavia, il programma deve ottenere l’accesso ai file o al sistema che terrà in ostaggio e questo accesso avviene tramite infezioni o vettori di attacco.
Tecnicamente, un vettore di attacco o infezione è il mezzo con cui il ransomware ottiene l’accesso.

Esempi di tipi di vettore includono:
- Allegati e-mail: un metodo comunemente utilizzato per ingannare gli utenti è quello che prevede l’inserimento, all’interno di una mail camuffata come urgente, di un allegato dannoso.
- Messaggi: qui si includono sia i sistemi di messaggistica istantanea che le chat legate ai social network. Uno dei canali più importanti utilizzati in questo approccio è, infatti, Facebook Messenger.
- Pop-up: i pop-up sono creati per imitare il software attualmente in uso sul dispositivo della vittima, in modo che questa si senta a proprio agio seguendo le istruzioni che, alla fine, procureranno un danno all’utente.

Soccorso Immediato per Ransomware
Il ransomware non deve paralizzare la tua attività. I nostri specialisti sono pronti a recuperare i tuoi dati e proteggere i tuoi sistemi.
Il primo attacco ransomware
Sebbene il ransomware abbia mantenuto la preminenza come una delle maggiori minacce dal 2005, i primi attacchi si sono verificati molto prima.
Secondo Becker’s Hospital Review, il primo attacco ransomware noto si è verificato nel 1989 e ha preso di mira il settore sanitario.
Trent’anni dopo, il settore sanitario rimane uno dei principali obiettivi degli attacchi ransomware.
Il primo attacco è stato sferrato nel 1989 da Joseph Popp, un ricercatore sull’AIDS, che ha avviato l’attacco distribuendo 20.000 floppy disk ad altri ricercatori che lavoravano sull’AIDS in più di 90 paesi, sostenendo che i dischi contenevano un programma che analizzava, tramite questionario, il rischio per un individuo di contrarre l’AIDS.
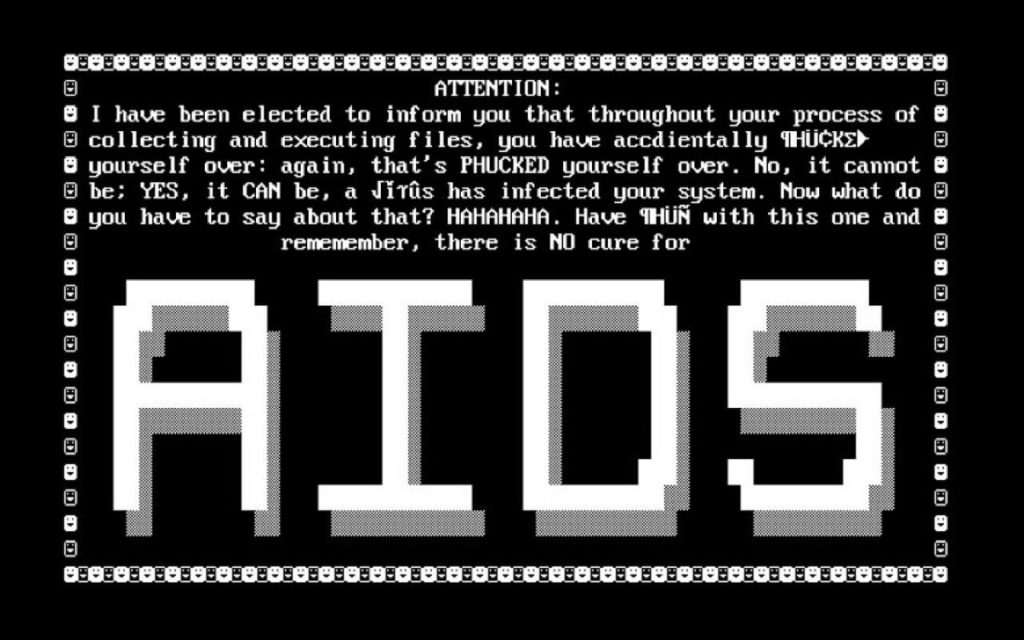
In realtà, invece, il disco conteneva anche un programma malware che andava ad attivarsi solo dopo che il computer era stato acceso 90 volte.
Dopo aver raggiunto la soglia dei 90, il malware faceva visualizzare un messaggio che richiedeva un pagamento di 189$ e altri 378$ per il noleggio del software.
Questo attacco ransomware è diventato noto come AIDS Trojan o PC Cyborg.
L’evoluzione del ransomware
Ovviamente, questo primo attacco ransomware è stato, a voler essere gentili, rudimentale e i rapporti indicano che avesse dei difetti.
Ciononostante, ha posto le basi per l’evoluzione del ransomware nei sofisticati attacchi che si effettuano oggi.
Secondo Fast Company, i primi sviluppatori di ransomware erano soliti scrivere da sé il proprio codice di crittografia.
Gli aggressori di oggi, invece, fanno sempre più affidamento su “librerie pronte all’uso che sono significativamente più difficili da decifrare” e stanno sfruttando metodi di consegna più sofisticati come le campagne di spear-phishing piuttosto che le tradizionali e-mail di phishing, che vengono spesso filtrate da filtri anti-spam odierni.
Mentre alcuni dei criminali informatici più avanzati stanno monetizzando il ransomware offrendo programmi ransomware-as-a-service, il che ha portato alla crescita di noti ransomware come CryptoLocker, CryptoWall, Locky e TeslaCrypt.
CryptoWall da solo ha generato entrate per oltre 320 milioni di dollari.
Dopo il primo attacco ransomware documentato nel 1989, questo tipo di crimine informatico è rimasto raro fino alla metà degli anni 2000, quando gli attacchi hanno iniziato a utilizzare algoritmi di crittografia più sofisticati e più difficili da violare come la crittografia RSA.

Esperti nella Rimozione di Ransomware
Affidati ai nostri professionisti certificati: oltre 25 anni di esperienza nel campo della rimozione di ransomware, recupero dati e sicurezza informatica.
Popolari in questo periodo erano Gpcode, TROJ.RANSOM.A, Archiveus, Krotten, Cryzip e MayArchive.
SecureList di Kaspersky riporta che da aprile 2014 a marzo 2015, le minacce ransomware più importanti sono state CryptoWall, Cryakl, Scatter, Mor, CTB-Locker, TorrentLocker, Fury, Lortok, Aura e Shade.
“Insieme sono stati in grado di attaccare 101.568 utenti in tutto il mondo, rappresentando il 77,48% di tutti gli utenti attaccati con cripto-ransomware durante il periodo in esame”, afferma il rapporto.
I più grandi attacchi ransomware e le varianti più importanti
Dato il progresso del ransomware, non sorprende che i più grandi attacchi di ransomware si siano verificati negli ultimi anni.
Parallelamente, anche le richieste di riscatto sono aumentate.
I rapporti indicano che, a metà degli anni 2000, le richieste si aggiravano in media intorno ai 300$, mentre oggi sono vicine ai 500$.
Di solito, per il riscatto viene prevista una precisa scadenza entro la quale la richiesta di riscatto raddoppia o non è più possibile accedere ai file perché questi vengono distrutti o bloccati in modo permanente.
CryptoLocker era uno dei ceppi ransomware più redditizi del suo tempo: tra settembre e dicembre 2013, ha infettato più di 250.000 sistemi guadagnando più di 3 milioni di dollari prima di essere messo KO nel 2014 tramite un’operazione internazionale.
Sfortunatamente, la fine di CryptoLocker ha portato solo all’emergere di diverse varianti di ransomware di imitazione, inclusi i cloni comunemente noti CryptoWall e TorrentLocker.
Lo stesso Gameover ZeuS è riemerso nel 2014 “sotto forma di una campagna evoluta che invia messaggi di spam dannosi”.
Da quel momento, c’è stata una costante ascesa nel numero di varianti e attacchi, con obiettivi primari di alto livello nei settori bancario, sanitario e governativo.

Soccorso Immediato per Ransomware
Il ransomware non deve paralizzare la tua attività. I nostri specialisti sono pronti a recuperare i tuoi dati e proteggere i tuoi sistemi.
Varietà di attacchi ransomware
A metà del 2015, CryptoWall aveva estorto oltre 18 milioni di dollari dalle vittime, spingendo l’ FBI a rilasciare un avviso per mettere in guardia gli utenti dalla minaccia.
Nel 2015, una varietà di ransomware nota come TeslaCrypt o Alpha Crypt ha colpito 163 vittime, facendo guadagnare agli aggressori 76.522$.
TeslaCrypt di solito richiedeva riscatti in Bitcoin, anche se in alcuni casi venivano utilizzate carte PayPal o My Cash, con importi che variavano dai 150$ ai 1.000$.
Vittime di ransomware
Si stima che i riscatti raggiungono i 50.000$, sebbene un attacco ransomware lo scorso anno contro un sistema ospedaliero di Los Angeles, l’Hollywood Presbyterian Medical Center (HPMC), avrebbe richiesto un riscatto di 3,4 milioni di dollari.
L’attacco ha costretto l’ospedale a tornare all’era pre-informatica, bloccando per dieci giorni l’accesso alla rete aziendale, alla posta elettronica e ai dati cruciali dei pazienti.
In realtà, un aggiornamento di HPMC indica che i rapporti iniziali di una richiesta di riscatto di 3,4 milioni di dollari erano imprecisi e che l’ospedale ha pagato i 17.000$ richiesti (o 40 Bitcoin all’epoca) per ripristinare le operazioni in modo rapido ed efficiente.
Poco più di una settimana dopo, il Dipartimento dei servizi sanitari della contea di Los Angeles è stato infettato da un programma che ha bloccato l’accesso dell’organizzazione ai suoi dati; tuttavia, l’agenzia ha isolato con successo i dispositivi infetti e non ha pagato il riscatto.
Alcune varianti di ransomware
Marzo 2016 ha visto anche la comparsa della variante del ransomware Petya.
Petya è un ransomware avanzato che crittografa la tabella dei file master di un computer e sostituisce il record di avvio principale con una richiesta di riscatto, rendendo il computer inutilizzabile a meno che non venga pagato il riscatto.
Petya è stata anche tra le prime varianti di ransomware.
In un articolo del maggio 2016, ZDNet ha riportato
“Secondo i rilevamenti dei ricercatori di Kaspersky Lab, le prime tre famiglie di ransomware durante il primo trimestre dell’anno sono state: Teslacrypt (58,4%), CTB-Locker (23,5%) e Cryptowall (3,4% ). Tutti e tre infettano principalmente tramite e-mail di spam con allegati dannosi o collegamenti a pagine Web infette”.
Entro la metà del 2016, Locky aveva consolidato il suo posto come una delle varietà di ransomware più comunemente utilizzate.
Durante il Black Friday (25 novembre) del 2016, l’Agenzia municipale di trasporto di San Francisco è stata vittima di un attacco ransomware che ha interrotto i sistemi di biglietteria dei treni e di gestione degli autobus.
Gli aggressori hanno chiesto un enorme riscatto di 100 Bitcoin (equivalente a circa $ 73.000 all’epoca), ma grazie alla risposta rapida e ai processi di backup completi, SFMTA è stato in grado di ripristinare i suoi sistemi entro due giorni.
Si ritiene che il ransomware utilizzato nell’attacco sia stato Mamba o HDDCryptor.
Nel 2016 è emersa anche una delle prime varianti di ransomware a prendere di mira Apple OS X.

Esperti nella Rimozione di Ransomware
Affidati ai nostri professionisti certificati: oltre 25 anni di esperienza nel campo della rimozione di ransomware, recupero dati e sicurezza informatica.
Il futuro del ransomware
Questi incidenti stanno catapultando il ransomware in una nuova era, in cui i criminali informatici possono facilmente replicare attacchi di piccole dimensioni puntando, però, contro aziende molto più grandi alle quali richiedere somme di riscatto elevate.
Il pagamento del riscatto non ti garantisce l’accesso ai tuoi file.
La soluzione migliore è rimuovere il ransomware e decrittare i file senza cedere al ricatto.
Tanto è vero che il ransomware CryptoLocker “ha estorto 3 milioni di dollari agli utenti ma non ha decrittografato i file di tutti coloro che hanno pagato”, riporta CNET sulla base dei risultati di un articolo del Security Ledger.
Un sondaggio di Datto ha rilevato che in un quarto degli incidenti in cui è stato pagato un riscatto, gli aggressori evitano di sbloccare i dati delle vittime.
Tra l’altro, le operazioni di ransomware continuano a trovare soluzioni più creative per monetizzare i loro sforzi, come è avvenuto con i ransomware Petya e Cerber che hanno aperto la strada agli schemi di ransomware-as-a-service.
Il potenziale di profitto per gli autori e gli operatori di ransomware è ciò che guida la rapida innovazione e la concorrenza spietata tra i criminali informatici.
Il ransomware PetrWrap, per esempio, è stato costruito utilizzando il codice crackato prelevato da Petya.
Per le vittime conoscere la provenienza del codice non ha importanza: che tu sia stato infetto da Petya o PetrWrap, il risultato finale è lo stesso, i tuoi file sono crittografati con un algoritmo così potente che attualmente non esistono strumenti di decrittazione ransomware.

Soccorso Immediato per Ransomware
Il ransomware non deve paralizzare la tua attività. I nostri specialisti sono pronti a recuperare i tuoi dati e proteggere i tuoi sistemi.
Ma quali sono le prospettive per il ransomware?
Un nuovo rapporto del National Cyber Security Center (NCSC) e della National Crime Agency (NCA) del Regno Unito avverte dello sviluppo di minacce come ransomware-as-a-service e mobile ransomware.
Le migliori pratiche per la protezione da ransomware, come i backup regolari e l’aggiornamento del software, non si applicano alla maggior parte dei dispositivi connessi e molti produttori di IoT sono lenti o semplicemente negligenti quando si tratta di rilasciare patch software.
Ora, considerando che le aziende fanno sempre più affidamento sui dispositivi IoT per eseguire le operazioni, potrebbe verificarsi un picco di attacchi ransomware su questo tipo di dispositivi.
Le infrastrutture critiche rappresentano un altro obiettivo preoccupante per futuri attacchi ransomware: il direttore dell’ufficio di gestione delle prestazioni aziendali del DHS, Neil Jenkins, alla conferenza RSA 2017 ha avvertito che i servizi idrici e le infrastrutture simili potrebbero costituire obiettivi allettanti per gli aggressori.
Jenkins ha fatto riferimento a un attacco ransomware del gennaio 2017 che ha disabilitato temporaneamente i componenti del sistema di keycard di un hotel austriaco come potenziale predecessore per gli attacchi più significativi alle infrastrutture a venire.
Come proteggersi dagli attacchi ransomware
Esistono passaggi che gli utenti finali e le aziende possono intraprendere per ridurre significativamente il rischio di cadere vittima del ransomware.
Ecco quattro pratiche di sicurezza fondamentali che qualsiasi azienda deve seguire:
- Backup frequenti e verificati: il backup di tutti i file e sistemi è una delle difese più potenti contro il ransomware. Tutti i dati possono essere ripristinati a un punto di salvataggio precedente;
- Aggiornamenti strutturati e regolari: la maggior parte dei software utilizzato dalle aziende viene regolarmente aggiornata dal creatore del software stesso. Questi aggiornamenti possono includere patch per rendere il software più sicuro contro le minacce note. Ogni azienda dovrebbe designare un dipendente per aggiornare il software.
- Restrizioni ragionevoli: alcune limitazioni dovrebbero essere applicate a coloro che: lavorano con dispositivi che contengono file, utilizzano dispositivi collegati a reti aziendali che potrebbero essere resi vulnerabili, sono lavoratori terzi o temporanei.
- Monitoraggio corretto delle credenziali: qualsiasi dipendente, appaltatore e persona a cui viene concesso l’accesso ai sistemi crea un potenziale punto di vulnerabilità per il ransomware. Il ricambio o il mancato aggiornamento delle password e le restrizioni improprie possono comportare probabilità di attacco ancora maggiori.
Una difesa efficace dal ransomware dipende, in buona parte, da una corretta educazione.
Educare i dipendenti sui segni rivelatori delle tattiche di distribuzione del ransomware, come attacchi di phishing, download drive-by e siti Web contraffatti, dovrebbe essere una priorità assoluta per chiunque oggi utilizzi un dispositivo.
In ogni caso, se sei stato colpito da ransomware, non disperare, evita il fai da te e contatta specialisti qualificati come quelli di HelpRansomware, che sapranno risolvere il tuo problema con le migliori soluzioni.

Recupero Dati Rapido e Sicuro
HelpRansomware garantisce un servizio di rimozione ransomware e recupero dati efficace e sicuro, con assistenza continua, 24 ore su 24, 7 giorni su 7.



