Learn how to get a decryption key and recover data from ransomware using the best decryption software.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
What is a ransomware decryption key?
A ransomware decryption key is a set of instructions to decrypt files encrypted by ransomware.
In the case of ransomware, the malware creators usually release the decryption key after payment of the ransom.
There are several types of decryption keys:
- Symmetric: using the same key to encrypt and decrypt the file;
- Asymmetric: using a different key pair for encryption and decryption, as Microsoft explains;
- Public and private: the two keys used for asymmetric encryption.
The public is potentially available to everyone, while the private one is only available to the party who receives the message;
- Pre-Shared Key (PSK): a decryption key previously shared by two users through a secure communication channel.
Many ransomware attacks use a symmetric key encryption algorithm.
This cryptographic method gives excellent results considering that, as shown in Varonis’ report, 64% of companies keep sensitive files open to all employees.

It means that minimum cryptography is sufficient to gain access.
What is password encryption?
Password encryption converts a readable text (plaintext) into a code (ciphertext).
This process ensures that only those who know the decryption key can access it.
In some cases, the ciphertext can be decrypted or converted back to plaintext using the same key, such as symmetric key encryption.
An encrypted or encoded password is protected by an encryption algorithm that makes access more difficult.
So password encryption is a protection method.
Decryption keys are a combination of numbers and letters and should not be predictable.
It is better to avoid passwords like your name or date of birth since this information is easy to access
What is the password to an encrypted file?
Today’s technology allows decrypting any key.
However, you can use three methods to generate longer keys that are harder to encrypt:
- Use an asymmetric cryptographic system such as RSA or Diffie-Hellman encryption.
These algorithms require two keys: one for encrypting the file and one for decryption.
They are not so widespread because they are much slower than symmetric keys;
- Use a one-way hash function that creates an incredibly long random string.
Trend Micro describes the hash as:
“Fingerprints for files. The contents of a file are processed through a cryptographic algorithm, and a unique numerical value – the hash value – is produced that identifies the contents of the file.”
However, you can generate short hashes combined with other hashing algorithms to get longer keys sharing the same level of complexity;
- Use the birthday paradox to select large prime numbers between 1 and N, where N is the number of bytes in the given file size.
Encoding or encrypting a file makes data unintelligible to those who do not have the decryption key.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
How to get a decryption key?
In principle, you must be the owner of the encrypted file to get a decryption key.
The file creator or someone who knows how to decrypt it can release the decryption key.
You can get the password of an encrypted file using a brute-force attack.
A brute-force attack is when a computer tries every possible combination of letters, numbers, and symbols until it finds the correct one.
According to Abnormal Security, brute-force attacks increased by +160% from May 2021 until mid-June.

You can also use a password recovery tool to decrypt your file.
However, you must use password recovery software compatible with the encrypted file type to decrypt the file.
For example, you will need RTF-compatible software if your encrypted file is a .rtf document.
Also, having access to your encrypted file does not mean you can decrypt it.
How to obtain the AES 256 decryption key?
AES 256 is a symmetric-key algorithm, as you can read on the Intel website.
It is designed to encrypt data securely so that a brute-force attack cannot break it.
The AES 256 decryption key is generated using the user password and the salt, a random sequence of bits.
Salt and passwords thatare never stored or transmitted outside your computer help your ransomware protection.
Each data block is encrypted using a unique password-based key.
This algorithm is basedon the AES-CBC block cipher.
The encryption algorithm adds an initialization vector to the input block of plaintext followed by a nonce of 214 bytes.
As explained by TechTarget, the nonce is:
“A random or semi-random number that is generated for a specific use. It is related to cryptographic communication and information technology (IT). The term stands for “number used once” or “number once” and is commonly referred to as a cryptographic nonce.”
The result is then subjected to XOR with the key to make ciphertext that you can only determine if you know the initialization vector and key.
AES 256 uses 128-bit keys and can only support a maximum of 16,000,000 blocks.
As reported by the EE Times, it could take 1 billion billion years to crack AES with a 128-bit key using a brute-force attack.
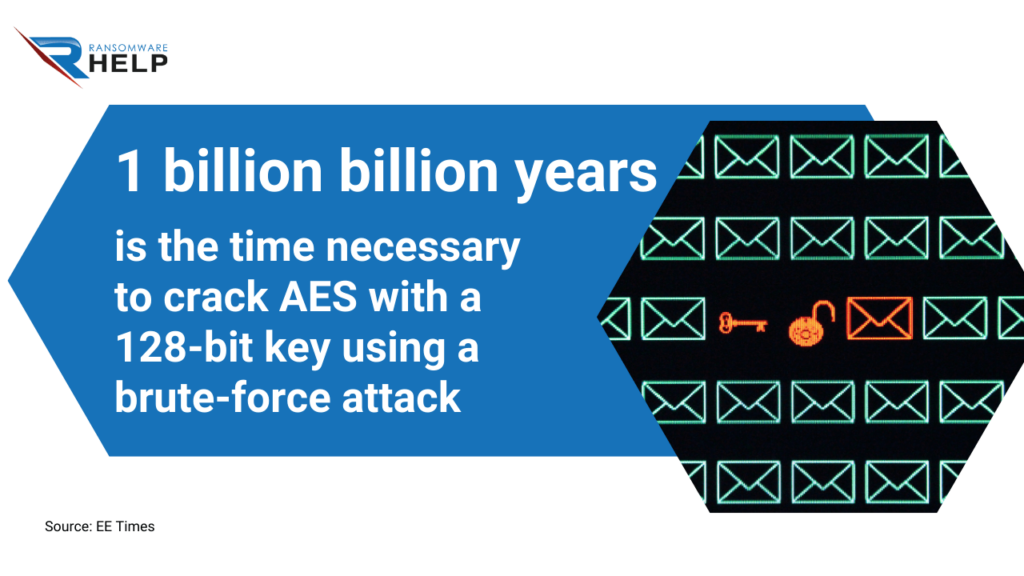
It makes the AES 256 decryption key very secure.
What is ransomware decryption software?
Ransomware is malware that installs on your computer and encrypts all files.
After that, hackers demand a ransom to decrypt the files.
Ransomware decryption software is a program to decrypt your files if you are hit by ransomware.
It generates a decryption key based on information about this ransomware.
This software decrypts files and restores them to their original form.
Decryption software is designed to prevent system encryption and collect the data needed to decrypt files on a computer.
What is the best ransomware decryption software?
The different types of ransomware have one thing in common: they encrypt your files and demand money in exchange for the decryption key.
Nowadays, ransomware is one of the most common cyber threats.
It encrypts your personal and business files, asking for a ransom to decrypt them.
Instead, a decryption key can help recover your files without paying the ransom.
Many ransomware decryption tools are available on the market for free or for a fee, but not all are reliable.
So, how to choose the best ransomware decryption software?
The best ransomware decryption software should unlock encrypted files and provide information to help you identify, locate, and recover deleted or lost data.
In addition, it should have a user-friendly interface with simple steps to follow while browsing the program.
It should also provide a good customer support team that assists you after you purchase the software.
Considering users’ reviews is an excellent way to see if you can trust them.
Finally, ensure that the decryption software is compatible with your operating system and devices.
Can Kaspersky decrypt ransomware?
Yes, Kaspersky can decrypt some ransomware.
The company has established a decryption service for victims of the latest WannaCry ransomware attack.
The service is free and available to users hit by ransomware.
The decryption key is generated on the user’s device and protected with a robust encryption algorithm to prevent abuse.
Moreover, the decryption key is automatically deleted from the device once used.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
Can Avast decrypt ransomware?
Avast is one of the few antivirus softwarethat can decrypt ransomware.
It uses deep machine learning to identify and remove malware, including ransomware.
Avast’s built-in decryption tool can decrypt files encrypted by many ransomware variants.
This ransomware decryption key is not free; however, you can purchase it with other products.
Is it possible to decrypt ransomware?
The best and most secure option to decrypt ransomware is to contact a specialist company such as HelpRansomware.
Alternatively, you can decrypt ransomware by paying the ransom or finding a way to get the decryption key.
As the HelpRansomware experts suggest, you should never pay for ransomware!

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
As for the decryption key, it is usually stored on the same server as the ransomware.
That means you can decrypt all your files if you can access the system, but it takes work.
Ransomware is typically injected through an email attachment, link, or phishing email.
According to the UK Government’s Department for Digital, Culture, Media, and Sport (DCMS), 83% of businesses and 79% of charities reported phishing attacks in 2021.

It then spreads to other computers on the network and often replicates automatically by installing itself on new hard disks and servers.
Once in the system, the ransomware can encrypt all files on your computer, making them inaccessible until you make a payment.
They will delete your data unless you pay.
Though in the case of double extortion ransomware, hackers can threaten you again even after paying the ransom.
The ransomware can be protected by advanced encryption and even delete all backups of your files.
At this stage, you will need to restore your backups to recover your data.
How long does it take to decrypt ransomware?
Ransomware attacks are becoming increasingly sophisticated and target companies unprepared for this threat.
Alvaka reports it takes a week or two to recover from ransomware.

However, the variables are many, and the timing can differ considerably.
No sum of money can compensate for the direct impact, loss of data, and all associated collateral damage resulting from a ransomware attack.
According to a report from the World Economic Forum, the cost of breaches to an organization is high, averaging $3.6 million.

Moreover, victims are rarely able to restore their data.
The decryption key is the only option to recover encrypted files after a ransomware attack on your computer.
How to decrypt encrypted ransomware files?
The decryption key is often hidden in ransomware code.
Ransomware files decryption can be processed using three basic methods:
- Find and enter the decryption key from memory (if stored on your computer);
- Find and enter the decryption key from your backups;
- Purchase a decryption tool to unlock your files encrypted by the attacker.
You can use numerous decryption tools by choosing according to the type of ransomware that attacked you.
This tool has some limits, as it requires specific IT skills.
When using decryption tools, ensure you don’t run any other programs on your computer while trying to decrypt ransomware files.
They can interfere with the decryption process and make things worse.
If you do not know this field, the best solution to decrypt ransomware files is to contact HelpRansomware.
Contact us to explain your case: send us proof of the ransomware that attackedyou, and we will decrypt and restore all the files damaged by the malware.
In case of a ransomware attack, the first thing to do is to stop using the computer and disconnect it from the Internet.
If you have an uncorrupted backup copy of yourdata, the easiest solution is to restore encrypted files using this technique.
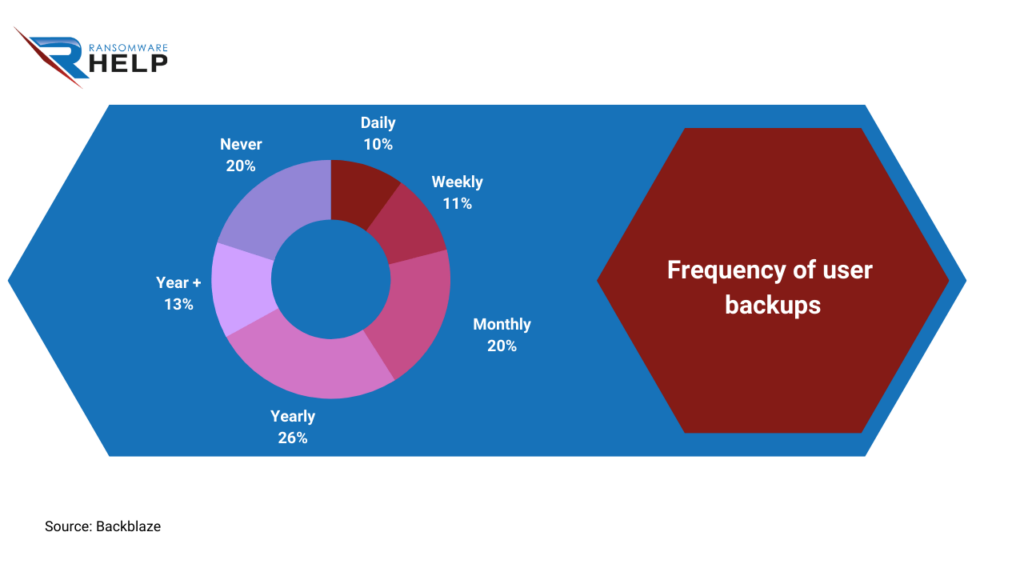
Backblaze reports that only 10% of users backup their data daily, while 20% never backup.
These statistics pose a huge security concern for your business.
Is ransomware file decryption using an online decryption key possible?
The answer is yes, and you can decrypt ransomware files with an online decryption key.
Many reliable websites offer this service for free, such as NoMoreRansom.org, created by Europol, the Netherlands police, Kaspersky Lab, and Intel Security.
However, this depends on the type of ransomware.
If ransomware is a file encryption virus, you can decrypt files with an online encryption key.
But if ransomware is a disk encryption virus, you cannot open encrypted files if you do not access the hard disk.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
Can I decrypt a file without a decryption key?
If you cannot get the decryption key, you must recover the file using other approaches.
You can use different basic techniques when attackers breach files without a key:
- Brute-force attack, the simplest form of hacker attack: it consists of trying every possible key until you get the right one;
- Frequency analysis: like brute-force attacks, it relies on attempting many different combinations of characters and alphabets, but to understand the characters frequency of an encrypted file;
- Temporal analysis: uses algorithms to detect and analyze abnormal behaviors;
- Statistics: help create ransomware behavioral models and find vulnerabilities, but also search for the decryption key based on probability formulas;
- Dictionary attack: another variant of the brute-force attack in an attempt to find decryption keys based on the words of a dictionary.
Anyone can use a decryption key to decrypt a file without knowing cryptography or encryption algorithms.
Is it possible to recover encrypted files from ransomware?
Yes, it is; in principle, you can remove ransomware and decrypt files.
However, this process is insidious because decrypting files does not mean having them back.
Decryption and recovery are two distinct stages and issues that ransomware victims must face.
Sometimes, decrypted files remain corrupted or still not usable.
According to Sophos‘s report, only 8% of the victims recover all their data.

In any case, file recovery is thelast step of the whole process.
However, if you are a victim of a ransomware attack, you should undertake some actions that we will see in detail in the following paragraphs:
- Detect ransomware;
- Recognize the ransomware family;
- Inform law enforcement;
- Restore systems using a backup.
The best way to prevent your data from being encrypted by ransomware is to backup files and use anti ransomware software regularly.
Detect ransomware
Ransomware can take several forms, some of which are not immediately recognizable.
According to an analysis by DataProt, there are more than 1 billion malware programs.

HelpRansomware provides victims with services that cover the entire procedure, from identification to removal and data recovery.
Pay attention to these warning signs to identify if your system has been infected by ransomware:
- Your system screen is locked, andyou cannot access your desktop;
- You are unable to access any files on your computer;
- You receive a ransom request asking for money in exchange for releasing the decryption key.
Other types of malware are hardly recognizable; therefore, it may be more challenging to notice the infection.
One is keylogger malware, which records every keystroke the user makes on their computer and is used to steal personal information from the victim.
This type of spyware is widely used in combination with ransomware.
Firstly, the keylogger steals passwords and helpful information to carry out a computer engineering or phishing attack; then, the ransomware infects the device.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
Recognize the ransomware family
Some tools help you recognize which ransomware has infected the system:
- Bitdefender Ransomware Recognition Tool: the famous cybersecurity company has released this software which, once installed, allows you to identify the ransomware family or its variants.
If available, it also provides you with a decryption key through a link that can help you remove the ransomware;
- Ransomware ID: is an online service that, as specified on the website, can recognize 490 ransomware.
The tool works by inserting the file used by hackers who asked for the ransom or one of the encrypted files.
In general, you can recognize the type of malware by checking the extension of your files: a different extension means that you have been infected.
Depending on the extension, you can also figure out which ransomware has carried out the attack.
Inform law enforcement
The ransomware attack is a cybercrime.
As a result, you must immediately inform the police in case of a ransomware attack.
The Internet Crime Complaint Center (IC3), managed by the FBI, reports that they received 3,729 complaints related to ransomware in 2021.

Authorities will help with investigations, advise on how to proceed, and provide you with a decryption key.
It may take a long process, but this is the right thing to do.
Restore systems using a backup
Backup typically involves copying and storing computer data on secondary devices, such as tapes or magnetic disks.
Files storage is one of the most secure methods to protect yourself from ransomware.
Restoring systems from a backup involves data decryption and use to restore the system.
It is essential to have an offline backup to ensure you always store all your data, even without a decryption key.
Saving your files on a USB device might be the best option for data recovery without paying the ransom.
Conclusions
In this article, we show everything you need to know about decryption keys and their importance in recovering files attacked by ransomware.
Here are the conclusions you can draw:
- A ransomware decryption key is a set of instructions used to decrypt files;
- The malware creators release the decryption key once the ransom is paid;
- There are several types of decryption keys;
- You can get the password of an encrypted file using a brute-force attack;
- AES 256 standard is a symmetric encryption algorithm;
- It takes a week or two to recover from ransomware;
- Only 10% of users backup their data daily, while 20% never backup.
The top priority for ransomware is relying on a team of experts who can assist you and take prompt action.
HelpRansomware provides victims with services that cover the entire procedure, from identification to removal and data recovery.
Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.