Find out how to decrypt MedusaLocker, how it spreads, and how much it costs to recover data encrypted by this ransomware.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
What is MedusaLocker?
MedusaLocker is a ransomware that first appeared at the end of October 2019.
It is designed to encrypt files on a computer system and request payment for the decryption key.
MedusaLocker targets both individuals and organizations.
From 2018 to 2022, this ransomware hit 55.1% to 71% of organizations worldwide, as reported by Statista.

This rate has increased by + 29%.
MedusaLocker is one of the most dangerous ransomware threats, as it spreads over networks and even disables security software.
What is MedusaLocker malware?
MedusaLocker ransomware belongsto the macro malware family.
As stated by the Cybersecurity and Infrastructure Security Agency (CISA):
‘MedusaLocker ransomware actors mostoften gain access to victim devices through vulnerable Remote Desktop Protocol (RDP)configurations. Actors also frequently use email phishing and spam email campaigns – directly attaching the ransomware to the email – as initial intrusion vectors.’
Once installed, it encrypts all your data, including documents, photos, videos, and other important files.
This malicious software is designed to be challenging to spot and remove, making it particularly dangerous for users unaware of it.
MedusaLocker ransomware family
MedusaLocker has been detected in over 80 countries worldwide, making it one of today’s most common malware threats.
It belongs to the STOP DJVU ransomware family, which has become one of the most common forms of malware in recent years.
The STOP family (DJVU) is known for its ability to avoid detection through sophisticated encryption and anti-detection techniques.
As the name implies, MedusaLocker is part of the more prominent locker ransomware family.
This group also includes all CryptoLocker versions.
Locker ransomware and crypto ransomware’s major distinction is that the former disables the device’s primary functions while the latter encrypts data without interfering with the device’s operations.
How does MedusaLocker spread?
MedusaLocker ransomware can infect computers through malicious emails, downloads, and other websites.
This malware, like any other cybercrime, typically employs social engineering to detect user vulnerabilities.
The most common methods of dissemination fall into two categories:
- Drive-by downloading.
MedusaLocker is distributed via drive-by downloads disguised as legitimate software.
These fake software and programs seem trustworthy, but they allow attackers to access your system by installing other unknown malicious applications.
To avoid this attack, we recommend installing an anti ransomware program and keeping your system up to date.
- Phishing emails
MedusaLocker may also spread via phishing emails that appear to be from banks or other financial institutions.
Phishing emails can encourage users to update their account information and password by clicking on a link within the email, which will install malware on the system without their knowledge.
The figures reported by Statista show that this threat mostly affected finance (23.6%), SaaS and webmail services (20.5%), and e-commerce (14.6%) in 2022.
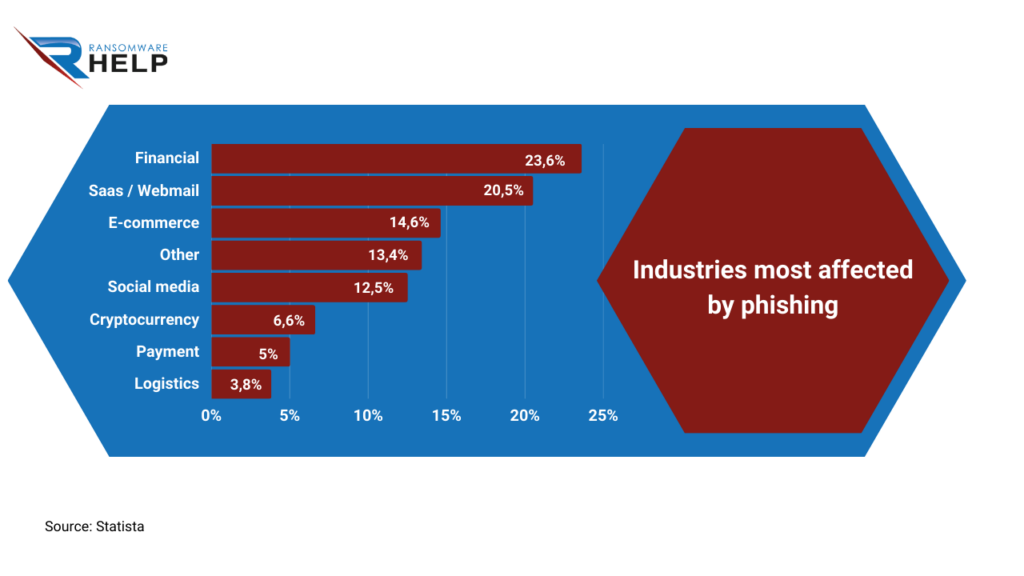
Various versions of MedusaLocker were detected on several computer platforms, including workstations, corporate servers, and even mobile devices.
This ransomware takes control of an infected computer’s file system by replacing the original master boot record (MBR) with one that automatically reboots the computer.
The virus installs a new MBR with malicious code when starting the system.
What attack vectors does MedusaLocker use?
MedusaLocker ransomware employs a variety of attack vectors to gain access to the targeted system.
According to the MITRE ATT&CK classification, the most common matrices are the following:
- T1078, valid accounts: hackers use brute force to find the password and access the victim’s network;
- T1566, phishing: emails with attachments are always an effective way to obtain useful sensitive data;
- T1133, external remote services: hackers use app gateways, such as VPN, to gain network access;
- T1059.001, command and PowerShell scripting interpreters: cybercriminals can use PowerShell to perform many tasks, including detecting information and executing code;
- T1047, Windows Management Instrumentation (WMI): is used to delete shadow copies of the volume to prevent victims from the possibility of recover encrypted files;
- T1547, boot or logon autostart execution: MedusaLocker injects the virus when restarting the system by adding registry entries;
- T1548.002, User Access Control (UAC) bypass: Ransomware bypasses UAC mechanisms to elevate privileges and perform operations with administrator-level permissions;
- T1562.001, disable or modify security tools: this allows hackers to detect malware;
- T1562.009, Safe Mode Boot: hackers can abuse Windows Safe Mode to disable endpoint defenses.
These are just some attack vectors MedusaLocker uses, but the list is much longer.
This ransomware attack is dangerous because of the various ways it can infiltrate victims’ devices.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
How to block MedusaLocker ransomware?
Preventive measures are essential to protect yourself from ransomware like MedusaLocker.
These suggestions are practical measures to counter each of the attack vectors mentioned above:
- Ensure that applications securely store personal data and credentials;
- Check accounts and permission levels;
- Use application control when running tools outside your organization’s security policies;
- Identify weaknesses in the UAC using the highest application level for user account control;
- Ensure your operating system is up to date;
- Use configured application control to block WMI execution if not required;
- Restrict access to remote services and use strong two-factor or multi-factor authentication;
- Enable ASR (Attack Surface Reduction) to prevent Visual Basic scripts and JavaScript from performing potentially malicious downloads;
- Install reliable antivirus software that can isolate suspicious files.
And to reduce human error as much as possible, restrict the admin role to a few accounts, following the principles of least privilege.
Acams reports that 58% of respondents have a cybersecurity incident response plan.
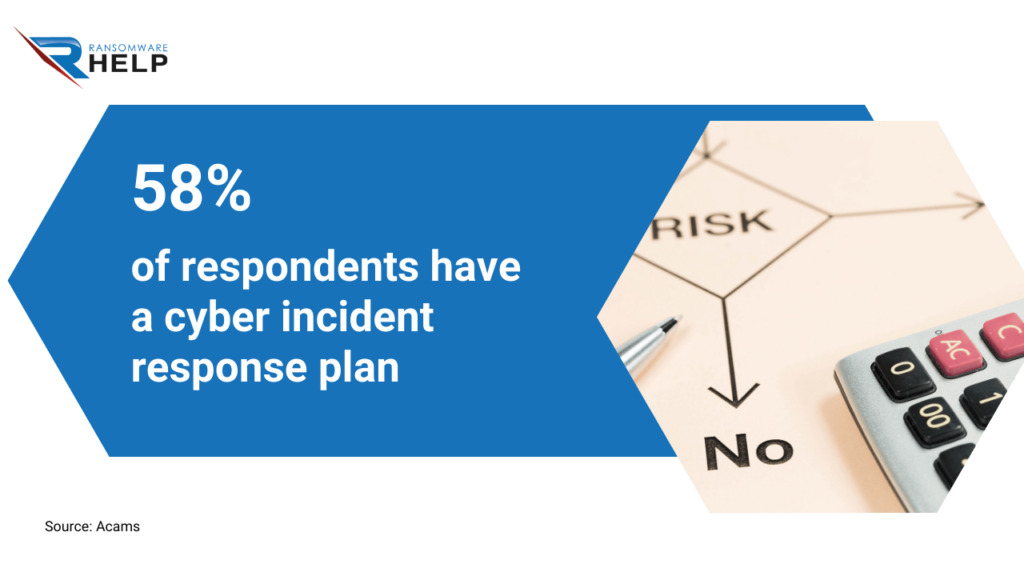
81% believe it is beneficial.
How to remove MedusaLocker ransomware
To remove MedusaLocker ransomware, you must first identify and delete the malicious software.
You have two options to do this:
- Restart the computer in safe mode with networking;
- Scan your computer with anti-spyware to spot files infected by MedusaLocker ransomware.
This first option is more practical without a high level of computing knowledge.
The second option, however, is more drastic:
- Restart the computer in safe mode using the command prompt;
- Start the system restore program;
- Select a restore point from before the virus infected your computer;
- Scan the system to ensure there are no ransomware traces.
These recommendations make sense if you have saved a previous system restore point.
Otherwise, by restoring the original factory settings, you will lose all the files and data.
How to decrypt MedusaLocker?
MedusaLocker randomly generates an encryption key, makingit virtually impossible to decrypt the data without the correct decryption key.
As reported by Cybereason, 54% of victims said system issues persisted even after decryption.

In other cases, some data has been corrupted after decryption.
The best option for deleting the malware and recovering all your data is to use the services of a specialized company.
HelpRansomware brings together the best experts in the industry to provide lasting and practical solutions.
Are there any free tools to decrypt MedusaLocker?
Unfortunately, no free ransomware encryption tools can protect from MedusaLocker.
Indeed, MedusaLocker is a relatively new form of ransomware, and security software has not been updated to detect this threat.
Malwarebytes and Microsoft Windows Defender are the only antivirus programs that can detect this malware.
However, they cannot remove ransomware or decrypt files.
Victims of this ransomware must rely on professional services from cybersecurity companies or law enforcement for data recovery.
HelpRansomware is the world’s number one ransomware removal, cybersecurity, and encryption company. A dedicated team will look after you in critical circumstances requiring quick action.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
Can I decrypt my files from MedusaLocker without paying the hacker?
You should never pay the ransom in case of a ransomware attack.
According to Acams’ analysis, 38% of respondents agree with this warning: never pay the ransom.
36% admit to paying it in the event of a national security threat.
For 29%, paying the ransom means avoiding operational and reputational consequences.
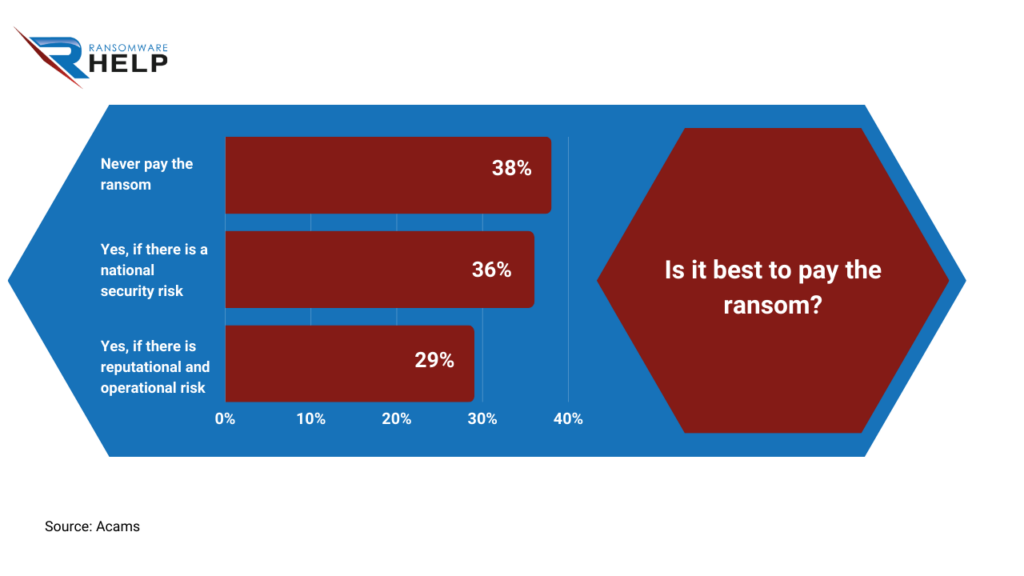
Moreover, paying the ransom does not guarantee data recovery and makes you a more vulnerable victim in the eyes of hackers.
85% of respondents support this thesis.
The only effective way to decrypt ransomware files like MedusaLocker is to contact specialists.
Does MedusaLocker deliver the decryption key after having paid the ransom?
The answer depends on many factors.
Some victims reported receiving the decryption key after paying the ransom, while others did not.
As reported by Cybereason, 80% of the companies that paid ransom suffered a second attack, and 40% made further payments.

70% of this latter group said the second ransom was even higher.
The best advice is to avoid paying the ransom.
Ransomware in the healthcare sector: the sensitive information and the inability to disrupt daily operations make this industry more vulnerable than others.
MedusaLocker ransomware breach level stats
Knowing the indicators of data breach statistics is essential to protect your data and mitigate damage.
First, remember that some types of ransomware may not show signs of a breach.
In these cases, victims are unaware of the attack until they notice the data encryption or receive the decryption request.
Most victims are informed about the attack via an email, text message, or pop-up window with the ransom note.
However, various indicators suggest that you are a victim of ransomware.
You may notice an increase in network traffic, for example.
Or your computer may reboot several times.
If you notice any suspicious behavior, disconnect your device from the internet to avoid compromising other connected users.
Files encrypted by MedusaLocker
The easiest way to understand if your files have been encrypted by MedusaLocker is to check if the file extension has changed.
Today, the list of extensions linked to this ransomware includes 139 variants.
According to Proven Data, the most common are the following:
- .ReadTheInstructions;
- .READINSTRUCTION;
- .ReadInstructions;
- .Malware;
- .redplague;
- .hellomynameisransom;
- .abstergo;
- .readInstructions;
- .deadfiles;
- .EMPg296LCK;
- .zoomzoom;
- .versus2;
- .versus4;
- .lockfilesbw;
- .lockfiles;
- .deadfiles;
MedusaLocker sometimes renames the entire file.
Sudden changes in file size can also indicate a ransomware attack.
Furthermore, MedusaLocker typically injects malicious software you can detect using an antivirus program.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
MedusaLocker ransom note
When MedusaLocker infects a system, it leaves a ransom request that notifies the victims of the attack.
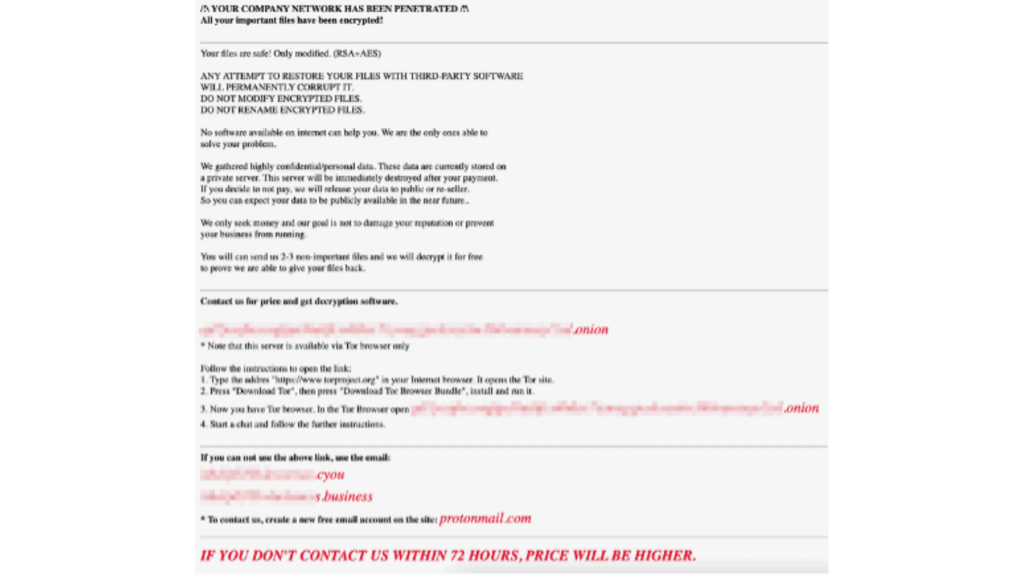
This ransom request typically has payment instructions to restore access to encrypted files.
It also warns you will permanently lose data unless you pay.
The ransom request with instructions is placed in each encrypted file folder.
Victims are given a specific Bitcoin wallet address to pay the ransom.
MedusaLocker Portal
Some ransom requests sometimes also include a Tor link to a MedusaLocker portal.
These links are frequently broken, but the portal is primarily used as a collection point for ransomware victims.
There is a platform for victims to get in touch with the attackers and negotiate the ransom payment.
Does MedusaLocker ransomware steal data?
Since MedusaLocker belongs to the macro family of ransomware lockers, data theft is not its primary purpose.
This type of ransomware blocks user data to extort money from users.
Its primary feature is to lock data, not steal it.
But with the rise of double extortion ransomware techniques, this malware is also moving in that direction.
It also captures personal photos, videos, or text files before encrypting and storing them on its servers, asking victims to pay again.
How much does it cost to recover from MedusaLocker ransomware?
The ransom varies greatly.
According to IBM reports, in 2022, the average cost of a data breach reached 4.35 million dollars, much more than in recent years.

The cost of recovering from MedusaLocker ransomware depends on the type of attack, the number of systems affected, and the damage severity.
Proven Data reports that the initial ransom demand is around $12,000.
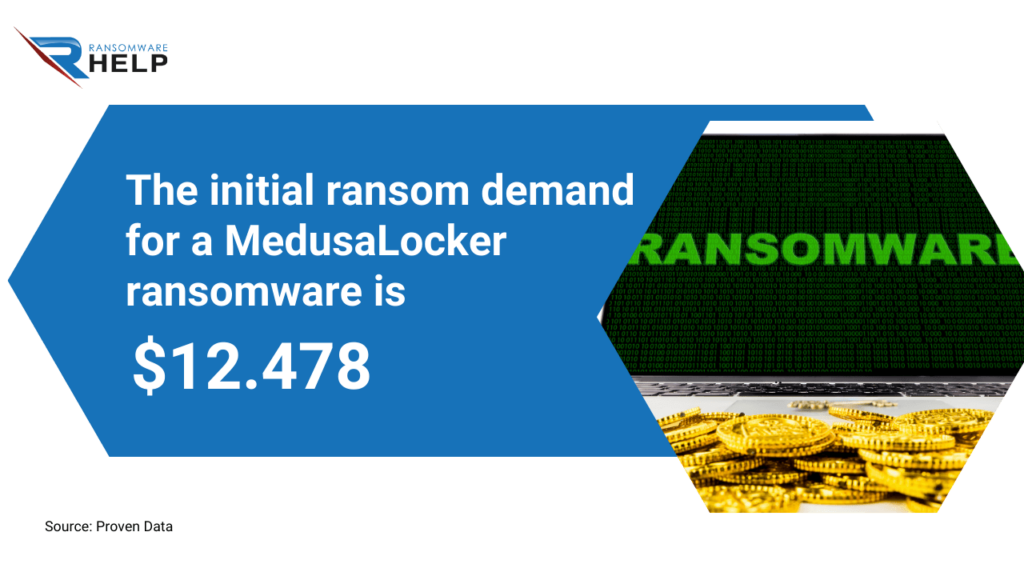
Consider that the online payment platform where this malware is delivered may also add a fee to the ransom amount.
It is important to note that paying the ransom does not guarantee data recovery.
Therefore, it is always advisable to invest in reliable security solutions as a preventive measure against this type of attack.
How long does it take to recover from a MedusaLocker ransomware attack?
Recovering from a MedusaLocker ransomware attack canbe a long and arduous process.
It consists of three main steps:
- Completely remove malicious software;
- Restore encrypted files;
- Implement security measures to protect against future attacks.
Depending on the severity of the attack, it may take days, weeks, or even months to recover from a MedusaLocker ransomware attack completely.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
What is the data recovery success rate for MedusaLocker ransomware?
Unfortunately, recovering data encrypted by MedusaLocker ransomwareis not easy.
It depends on the AES 256 algorithm protected with RSA-2048 encryption, which prevents open encrypted files without the correct key.
Other types of ransomware have less tragic percentages.
As reported by Cybereason, 78% of companies that did not pay the ransom stated they restored systems and data without the decryption key.

A backup or restore point before the ransomware infection allows you to get your data back quickly.
MedusaLocker’s victims
The MedusaLocker ransomware turned out to be very dangerous.
It has affected thousands of companies and organizations, causing them millions of dollars in losses.
According to MedusaLocker‘s portal homepage, ransomware has affected over 80 countries.
Companies hit by ransomware are located mainly in 20 countries:
- Argentina;
- Canada;
- Chile;
- Colombia;
- Costa Rica;
- Denmark;
- Ecuador;
- France;
- Germany;
- Austria;
- Slovenia;
- Spain;
- Switzerland;
- UAE;
- United Kingdom;
- USA.
This attack hit more companies not on the list due to a lack of data.
The Coveware study provides information about the industries most affected by ransomware in the second quarter of 2022:
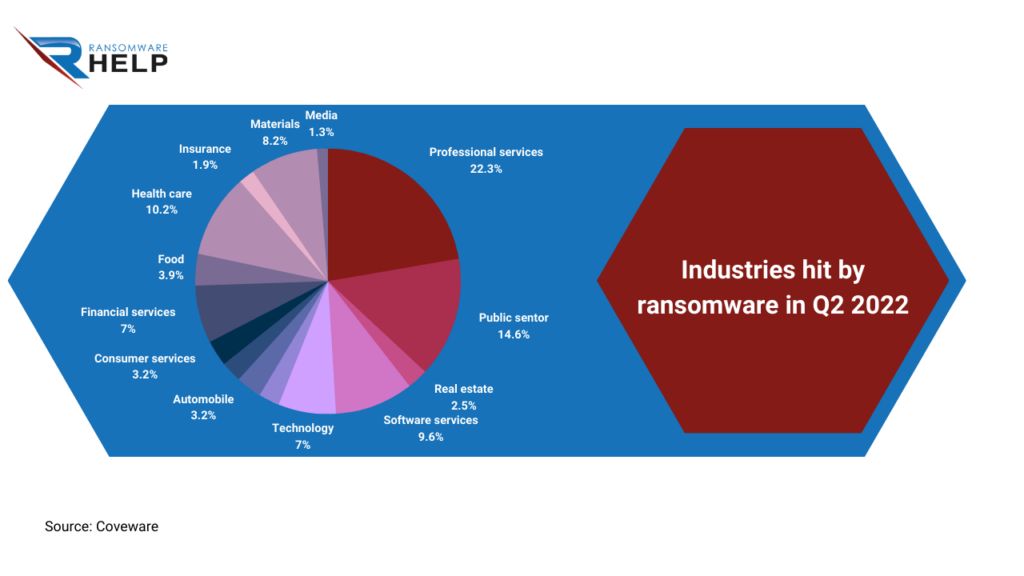
Professional services (21.9%) and the public sector (14.4%) lead the ranking, followed by health care (10%).
How to prevent MedusaLocker’s attack from happening again?
The best way to prevent a MedusaLocker attack from recurring is to implement adequate security measures.
This includes implementing the following actions:
- Complex passwords;
- Procedure for notifying the IT team of network changes;
- Two-factor authentication for all accounts;
- Regular updating of software and systems with the latest security patches;
- Training employees about online threats.
Organizations should also invest in reliable backup solutions to recover quickly from ransomware attacks.
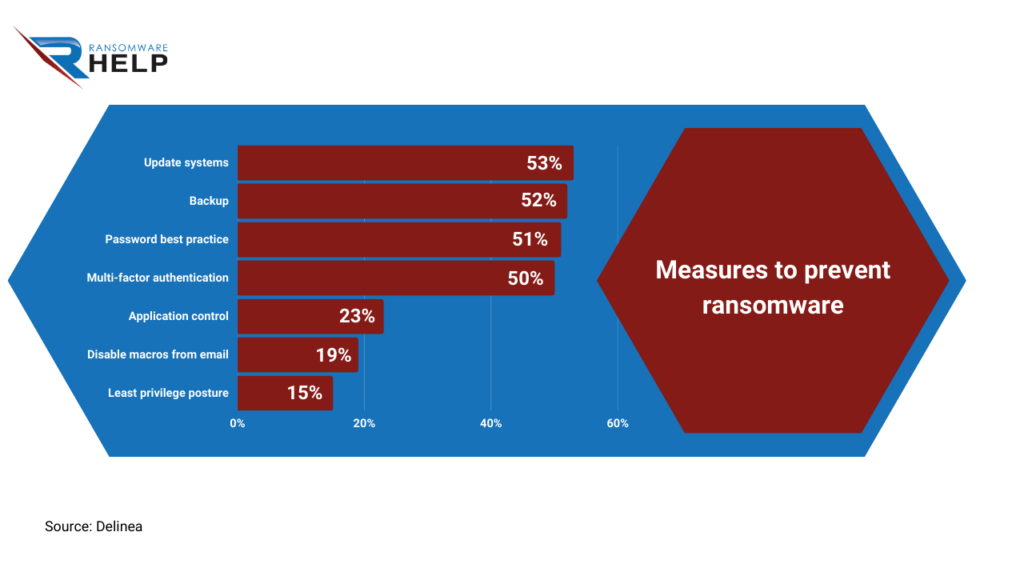
As reported by Delinea, here are some measures that helped prevent ransomware attacks in 2022:
- Software and System Updates: 53%;
- Regular backups of sensitive data: 52%;
- Improving best practices for passwords: 51%;
- Multi-factor authentication: 50%;
- Implementing application controls: 23%;
- Disabling macros from email attachments: 19%;
- Least privileges: 15%.
By adopting these measures, companies can ensure protection from future attacks and minimize the risk of financial losses due to ransomware.
Conclusions
In this guide, we have explained everything about MedusaLocker ransomware, one of the most dangerous malware that appeared recently.
Here are the conclusions you can draw:
- MedusaLocker is a ransomware that first appeared at the end of October 2019;
- MedusaLocker belongs to the STOP SJVU ransomware family, which has become one of the most common forms of malware in recent years;
- MedusaLocker ransomware can spread via malicious emails, downloads, and other websites;
- MedusaLocker ransomware uses various attack vectors to access the targeted system: 58% of respondents have a cybersecurity incident response plan;
- Unfortunately, no free ransomware encryption tools can protect from MedusaLocker;
- As reported by Cybereason, 80% of the companies that paid ransom suffered a second attack, and 40% paid again;
- 78% of companies who did not pay the ransom stated they had restored systems and data without receiving the decryption key.
Contact HelpRansomware for a custom solution to decrypt files encrypted by ransomware.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.



