Consult the HelpRansomware list updated to 2022: discover the twelve versions of cryptoLocker and the tools for their elimination.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
What is Cryptolocker
CryptoLocker is a ransomware that has been active since September 2013.
As soon as the data is encrypted, the hackers demand a ransom to recover the decrypter for the unusable files.
The computer shows ransomware notes in a “CryptoLocker” program which informs the victims they have 72 hours to recover their files.
CryptoLocker virus terminated on June 2, 2014, when Operation Tovar blocked the Gameover Zeus botnet.
The security company gained access to the database used by hackers to store all decryption keys, allowing users to recover their data.
Many other versions of the virus have emerged since then, but they are unrelated to the original one.
The malware uses seemingly harmless email messages as a medium: these messages contain malicious attachments that carry the ransomware.
The virus infiltrates the target PC’s system, encrypts the files, and displays a ransom note.
CryptoLocker versions uses RSA public-key cryptography to lock the following types of files on the victim’s PC:
3fr, accdb, ai, arw, bay, cdr, cer, cr2, crt, crw, dbf, dcr, der, dng, doc, docm, docx, dwg, dxf, dxg, eps, erf, indd, jpe, jpg, kdc, mdb, mdf, mef, mrw, nef, nrw, odb, odm, odp, ods, odt, orf, p12, p7b, p7c, pdd, pef, pem, pfx, ppt, pptm, pptx, psd, pst, ptx, r3d, raf, raw, rtf, rw2, rwl, srf, srw, wb2, wpd, wps, xlk, xls, xlsb, xlsm, xlsx.
This list is filled with widely used filenames, such as doc, Xls, and the like.
Cryptolocker asks you to pay a ransom via Moneypak or Bitcoin to restore them.
HelpRansomware recommend not pay the ransom.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
According to Data Center Knowledge, 42% of organizations that paid the ransom, did not get their files decrypted.

How ransomware spreads
CryptoLocker is considered one of the most efficiently distributed crypto-ransomware viruses.
Hackers combine several techniques to spread it.
According to experts, the Cryptolocker versions spreads using official-looking emails, fake pop-ups, and similar techniques.
Previously, the ransomware was distributed via email that contained malicious attachments, malware-laden ads, advertising programs, or updates that have the virus executive file or exploit kits.
Beware that this threat infiltrates your computer via fake pop-ups claiming that you need to update Java, Flash Player, or similar programs.
Make sure you install these programs from their verified developer sites, not suspicious third parties.
In September 2016, several new ransomware distribution techniques were identified, and, during 2020, other methods were refined.
As the virus tries to exploit human weaknesses, developers closely follow current events.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
This is why, especially this year, a lot of focus has been placed on masking malware in emails from healthcare companies.
The content can refer to false analysis results that communicate to the victim a disease or positivity, at Covid-19.
The message asks you to print the blood test results found in an attached document and take them to the family doctor as soon as possible.
As we said, by leveraging the panic of the victims, the criminals efficiently manage to enter their devices.
When the victim opens the attachment, the ransomware takes control of the system and encrypts all the files without remorse.
An interesting report by Bitdefender shows the terrible connections between the pandemic and the rise of ransomware attacks.

On the other hand, they are criminals whose sole purpose is to earn money.
Versions of the Cryptolocker ransomware virus
Here are some of the known cryptolocker versions of this ransomware.
Crypt0L0cker virus
Crypt0L0cker virus is one of the file-encrypting viruses that can infiltrate computers via fake Java updates or infected email attachments.
After encrypting the victim’s files, this virus adds the extension .encrypted or .enc to each of them and starts showing a warning message asking the victim to pay the ransom.
This virus was first detected in 2015.
However, several years later, it is still actively infecting computer users.
CryptoLocker-v3
You may have downloaded it by clicking on the fake popup that says you need to update Java or Flash Player.
To encrypt files, this threat uses RSA-2048 (a unique public key) and demands a ransom.
This malware uses the .crypted file extension, which is appended to every file it encrypts.
Cryptographic Locker
Cryptographic Locker is very similar to CryptoLocker ransomware.
It allows the victim to know which files they have encrypted by adding the .clf extension to each file.
Immediately after appearing on the Internet, this ransomware demanded a ransom of 0.2 BTC to exchange the decryption key needed to restore the encrypted files.
If you suffer an infection by this malware, please do not pay the ransom as there is no guarantee that the payment will help you restore the connection to your files.
PCLock ransomware
PCLock is another ransomware that tries to scare its victims by encrypting their files.
This procedure is usually initiated with the help of XOR encryption.
It is not as aggressive as the original version of CryptoLocker, so you should be able to get rid of it by removing its main WinCL.exe file and other files with the help of security software.
The ransom note is named last_chance.txt.
CryptoTorLocker2015
CryptoTorLocker2015 is capable of infecting the Windows OS and Android OS.
Once done, it uses XOR encryption to lock the victim’s files.
Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
If your system is full of valuable photos or business documents, consider that you may lose them.
Infected files are usually marked with the. CryptoTorLocker2015 extension, and you should also find the ransom note called AS DECRYPT FILES.txt on your desktop.
To remove this virus from their devices, Android users only need to uninstall the application they used to download the CryptoTorLocker virus onto their computers.
Windows OS supports users to use reputable antivirus or antispyware software for CryptoTorLocker2015 removal.
Crypt0 ransomware
Crypt0 ransomware was discovered in September 2016.
This ransomware leaves a HELP_DECRYPT.TXT ransom note, which informs the victim of the attack and asks to use contactfndimaf@gmail.com for data decryption instructions.
Cryptolocker infected Your computer! ransomware
Cryptolocker infected Your computer! Ransomware it is one of the versions of cryptolocker that targets italian-speaking users.
Like its predecessor, this ransomware modifies file extensions (uses the .locked extension) and gives the victim a certain amount of time to pay.
Currently, malware researchers are unaware of a free decryption tool.
CryptoLocker 5.1 ransomware virus
CryptoLocker 5.1 ransomware virus was released in 2016.
Since its first appearance, it has worked to infect Italian users.
Alternatively, it is also known as “Your computer is infected with Cryptolocker!”.
Although it tries to disguise itself as a notorious cyber threat, IT experts still suspect it is not as powerful as the original version.
Cryptolocker3 ransomware virus
Cryptolocker3 ransomware virus is malware that can also be called lock screen ransomware.
Such viruses do not encrypt computer files, but they prevent their victims from accessing them and using normal computer functions.
However, after several months of functionality, Cryptolocker3 has entered another subsection where the malware behaves like the original ransomware virus.
This parasite uses the XOR encryption algorithm and adds the .cryptolocker file extension.
MNS Cryptolocker
MNS Cryptolocker is another ransomware virus that uses the name of Cryptolocker.
After encrypting the victim’s files, the ransomware releases its ransom note asking the victim to send 0.2 BTC to be sent via Tor or other anonymous networks.
The virus does not add new extensions to the target files, so you only notice the infection when you try to open one.
CryptoLockerEU ransomware virus
CryptoLockerEU ransomware virus was detected in January 2017.
It appears to be a modified copy of the initial CryptoLocker virus.
The virus is called CryptoLockerEU 2016 rusia, which gives the idea that it was developed in 2016 by Russian hackers.
During the data encryption procedure, the virus encrypts files using an RSA-2048 algorithm.
The name of the ransom note should look like this: РАСШИФРОВАТЬ ФАЙЛЫ.txt.
However, due to an error in the source code of the virus, it appears as ĐŔŃŘČÔĐÎ ŔŇÜ ÔŔÉËŰ.txt.
CryptON
The Portuguese ransomware Cryptolocker or CryptON is the latest variant of the CryptoLocker related ransomware.
Some believe the same hacker group may have released it because it uses similar source code and displays the typical nature of CyptoLocker on the infected computer.
It’s interesting that this virus is aimed at Portuguese-speaking users since the ransom note and ransom payment interface are presented in this language.
Encrypted files are renamed as follows: [filename] .id- [victim ID] _steaveiwalker@india.com_.
To regain access to the files, victims are required to pay the usual ransom.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
Tips on how to protect your files from the crypto-virus
Here are some tips for preventing a ransomware attack:
- Never trust misleading ads because they spread the virus;
- Delete spam and double check any emails sent to you from unknown senders;
- Remember to disable hidden extensions (if you are using the Windows operating system);
- Download a reputable anti-spyware on your computer;
- Take backups as frequently as possible, because this may help you recover encrypted files;
- Use solutions like Google Drive, Dropbox, Flickr, etc.
However, be aware that this powerful virus may access these online storage locations via your internet connection and encrypt these files as well.
Therefore, we recommend storing data backups on removable storage devices such as hard drives or USB.
How to remove CryptoLocker
Below I propose two methods to remove CryptoLocker from your infected systems and how to recover your data independently.
Remember, however, thatthe best idea is to contact a company as HelpRansomware.
Method 1: use Safe Mode with Networking
To remove this ransomware with Safe Mode with Networking, please follow the steps below.
Keep in mind that this ransomware comes in a variety of different forms as we have seen before.
Some of these versions will likely attempt to stop you from running security software and remove it from your computer.
If you are in such a situation, skip to the next paragraph to find out how.
The first step is restarting your computer in Safe Mode with Networking.
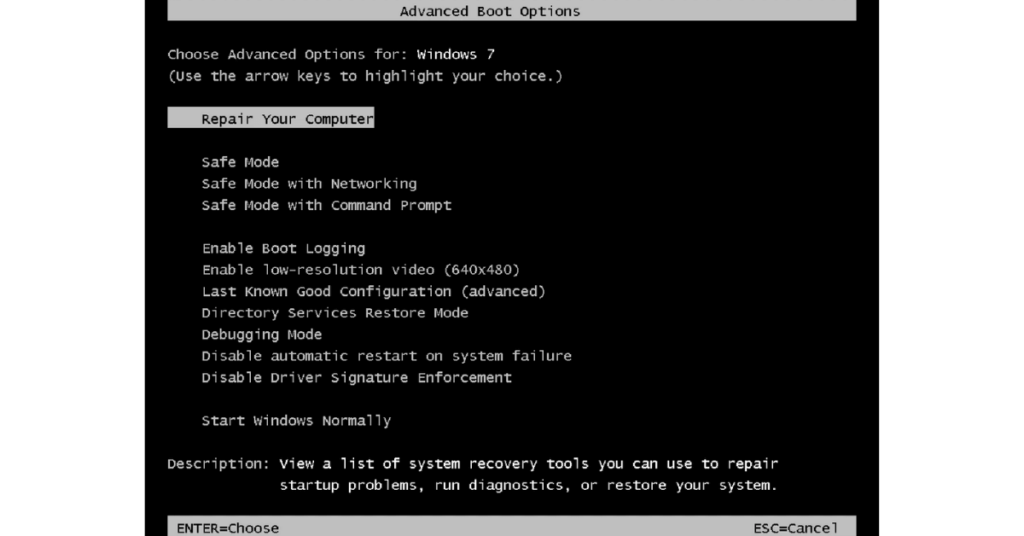
For Windows 7 / Vista / XP:
- Click on “Start”;
- Select “Shutdown”;
- Press “Restart”;
- Select “OK”.
- When the computer is active, start pressing F8 several times until the “Advanced Boot Options” window appears;
- Select “Safe Mode with Networking” from the list.
For removing ransomware from Windows 10 / Windows 8:
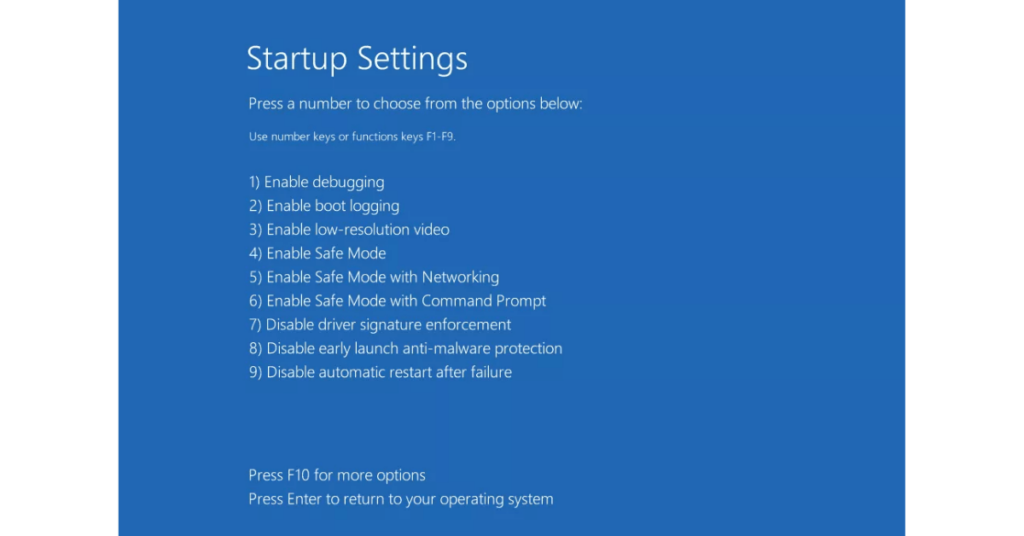
- Press the Windows power button on the login screen;
- Hold down the “Shift” key on your keyboard, and click “Restart”;
- Select “Troubleshoot”;
- Choose “Advanced Options”;
- Click on “Startup Settings”;
- Press “Restart”;
- Once your computer is up and running, select “Enable Safe Mode with Networking” in the “Startup Settings” window;
- Select “Enable Safe Mode with Networking”.
The second step is removing CryptoLocker.
- Log into your infected account and launch your browser;
- Download an anti-spyware program and update it before a full system scan;
- Remove malicious files that belong to your ransomware;
Method 2: use System Restore
If your ransomware is blocking Safe Mode with Networking, try this other method.
The first step is restarting your computer in Safe Mode with Command Prompt, as we saw in method 1.
The second step is resetting your system files and settings.
- Once the command prompt window appears, enter cd restore and click “Enter”;
- Now type rstrui.exe and click “Enter” again;
- In the next window, click on “Next” and select the restore point before the infiltration of CryptoLocker;
- Click “Next”;
- When the “System Restore” window appears, select “Next”;
- Click “Yes” to start the system restore;
- Download an anti-malware and scan your computer to make sure the CryptoLocker removal is done correctly.
How to recover your data
The guide presented above should help you remove CryptoLocker from your computer.
Opening encrypted files and making them usable again is more complicated.
Do not pay the ransom, because you have no guarantee of receiving the decryption key.
If you think you have been infected with CryptoLocker, there is an excellent chance that this is not the case.
The original virus was defeated several years ago and is no longer distributed.
If the ransom note says it infected you through a virus, it may be false.
Some viruses pretend to be this ransomware just to scare the victim.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
The good thing is that you can decrypt some fake versions of this malware.
We strongly recommend that you run a system scan to find out the actual name of the virus.
On the other hand, you can contact HelpRansomware by sending the name of the ransom note; the file extensions added to the encrypted files, and the image of the ransomware appeared on the desktop; plus some information contained in the ransom note.
Conclusions
With this guide, you have discovered the twelve versions of CryptoLocker and the tools to eliminate them.
From the article, you can draw the following conclusions:
- CryptoLocker is a virus that has been active since September 2013;
- The virus was defeated in June 2014;
- New versions have been created, not necessarily related to the original;
- Malware creators combine different techniques to propagate this type of ransomware.
HelpRansomware advises never to pay the ransom; get in touch with the experts to solve file decryption.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.




