Ransomware attack is a threat that has been hanging over businesses and individuals since the mid-2000s.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
In 2017, the FBI’s Internet Crime Complaint Center (IC3) received 1,783 ransomware complaints that cost victims over $ 2.3 million.
These complaints, however, only represent attacks reported to IC3.
The actual number of ransomware attacks and costs are much higher – around 184 million ransomware attacks occurred just last year.
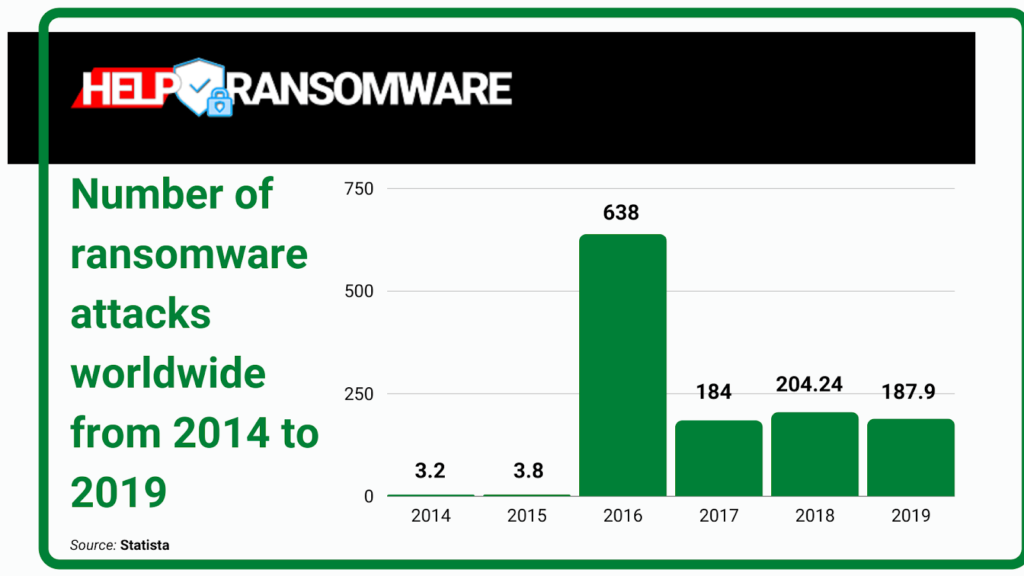
The ransomware’s original intent was to target individuals, who still make up the majority of attacks today.
This article will look at the history of ransomware from its first documented attack in 1989 to the present day.
We will show you in detail some of the most significant attacks and ransomware variants.
Finally, we’ll take a look at future evolution and ransomware solutions.
What is ransomware?
Understanding what ransomware is is very simple: we are talking about a type of malicious software that takes over files or systems and blocks users from accessing them.
All files, or even entire devices, are held hostage using encryption until the victim pays a ransom in exchange for the decryption key.
Although ransomware has been around for decades, its variants have become increasingly advanced in their abilities to spread, evade detection, encrypt files, and force users to pay the ransom.
This means that ransomware attacks have become more dangerous and damaging to victims.
How ransomware attacks work
Now that we have a rough definition of ransomware let’s move on to a more detailed account of how these malicious programs gain access to a company’s files and systems.
The term “ransomware” describes the software’s function, which is to extort users or companies for profit.
However, the program must gain access to the files or system it will hold hostage, and this access takes place through infections or attack vectors.
Technically, an attack vector or infection is the means by which the ransomware gains access.
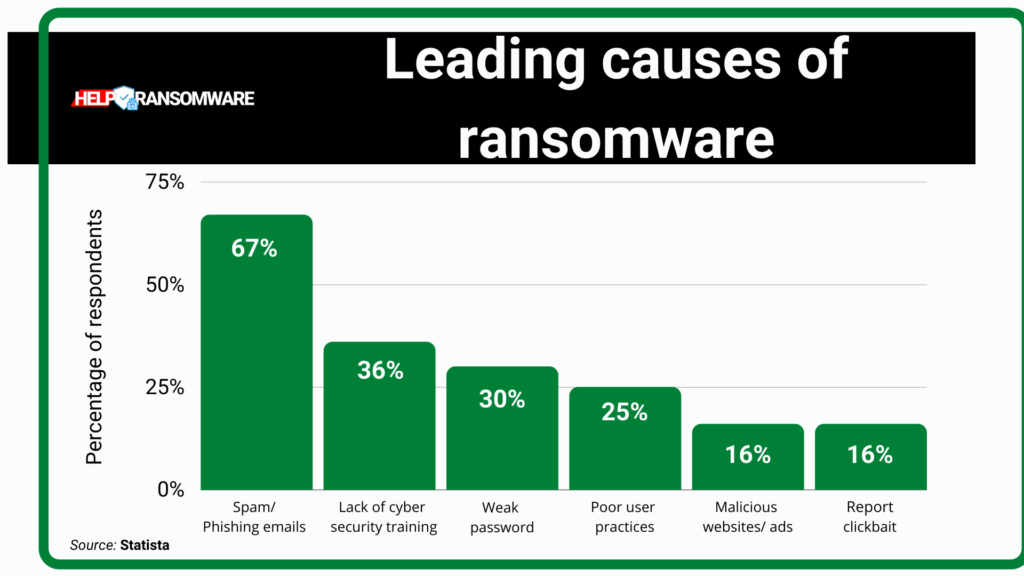
Examples of vector types include:
- Email attachments: a commonly used method to deceive users involves inserting a malicious attachment within an email disguised as urgent.
- Messages: this includes both instant messaging systems and chats related to social networks. One of the most important channels used in this approach is, in fact, Facebook Messenger.
- Pop-ups: pop-ups are created to mimic the software currently in use on the victim’s device so that the victim feels comfortable following the instructions which, in the end, will harm the user.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
The first ransomware attack
Although ransomware has maintained preeminence as a major threat since 2005, the first attacks occurred much earlier.
According to Becker’s Hospital Review, the first known ransomware attack occurred in 1989 and targeted the healthcare industry.
Thirty years later, the healthcare sector remains a major target of ransomware attacks.
The first attack was launched in 1989 by Joseph Popp, an AIDS researcher, who initiated the attack by distributing 20,000 floppy disks to other AIDS researchers in more than 90 countries, claiming that the disks contained a program that analyzed, through a questionnaire, the risk for an individual of contracting AIDS.
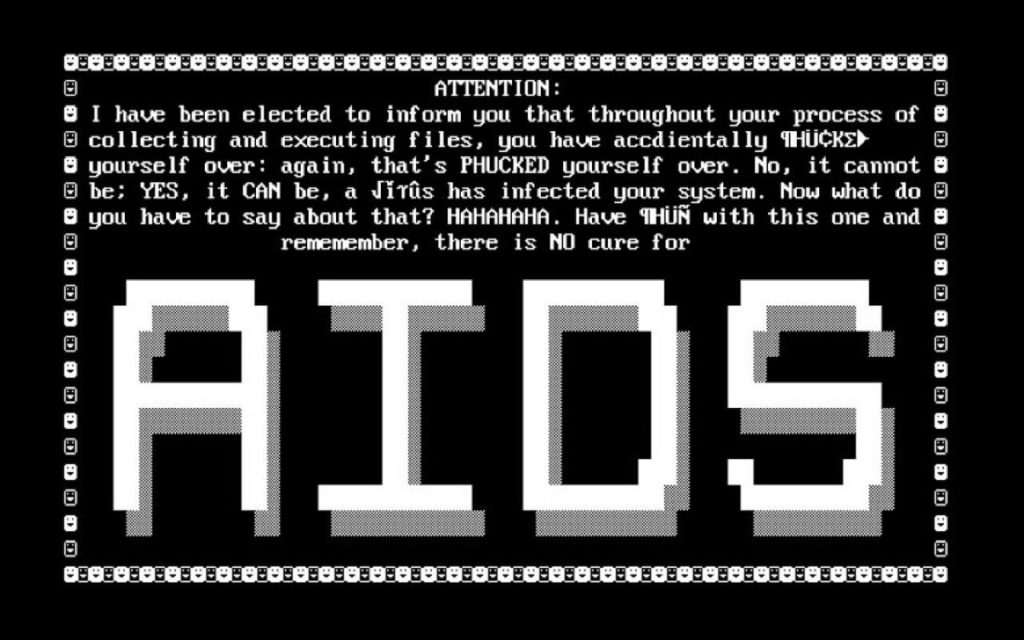
However, the disk also contained a malware program that would have been activated only after turning on the computer 90 times.
Upon reaching the 90th, the malware displayed a message requesting a payment of $ 189 and an additional $ 378 for the software rental.
This ransomware attack became known as the AIDS Trojan or PC Cyborg.
The evolution of ransomware
This first ransomware attack was, to be polite, rudimentary and reports indicate it had flaws.
Nonetheless, it laid the foundation for the evolution of ransomware in the sophisticated attacks taking place today.
According to Fast Company, the first developed ransomware players used to write their own encryption code themselves.
On the other hand, today’s attackers are increasingly relying on “ready-to-use libraries that are significantly harder to crack” and are leveraging more sophisticated delivery methods such as spear-phishing.
Besides, some more sophisticated attackers are developing toolkits that can be downloaded and implemented by attackers with less technical skills.
Meanwhile, some of the most advanced cybercriminals are monetizing ransomware by offering ransomware-as-a-service programs, which has led to the growth of well-known ransomware such as CryptoLocker, CryptoWall, Locky, and TeslaCrypt.
These are some examples of common types of advanced malware.
CryptoWall alone has generated over $ 320 million in revenue.
After the first documented ransomware attack in 1989, this type of cybercrime remained rare until the mid-2000s, when attacks started using more sophisticated and harder-to-crack encryption algorithms such as RSA encryption.
Popular during this time were Gpcode, TROJ.RANSOM.A, Archiveus, Krotten, Cryzip, and MayArchive.
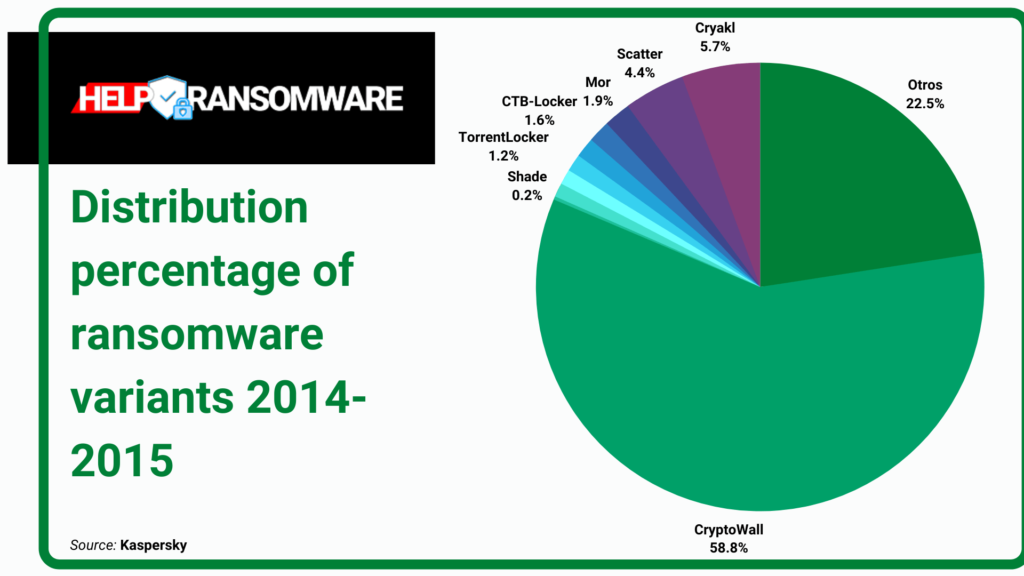
Kaspersky’s SecureList reports that from April 2014 to March 2015, the most prominent ransomware threats were CryptoWall, Cryakl, Scatter, Mor, CTB-Locker, TorrentLocker, Fury, Lortok, Aura, and Shade.
“Between them they were able to attack 101,568 users around the world, accounting for 77.48% of all users attacked with crypto-ransomware during the period” – states the report.
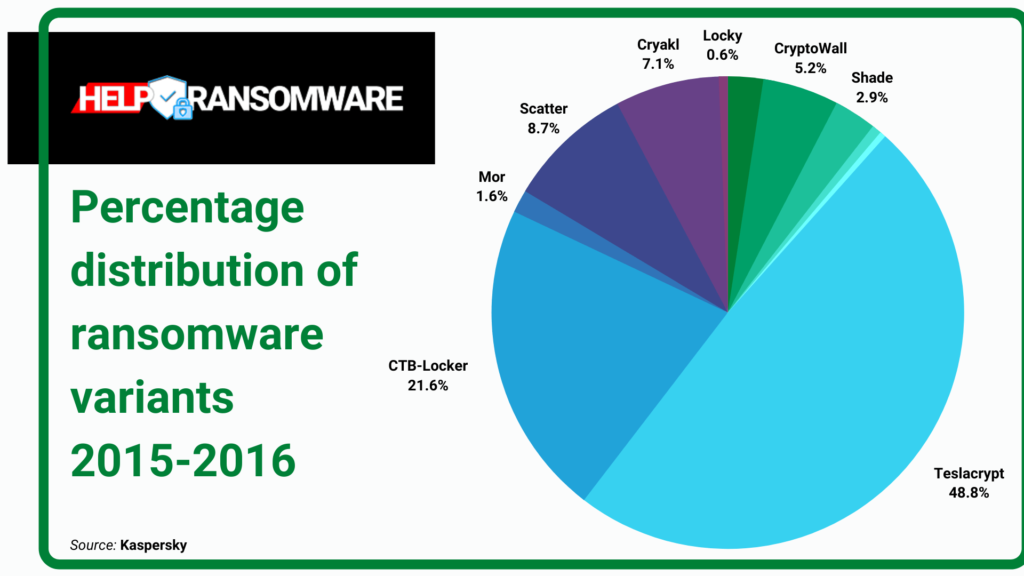
In just one year, the landscape has changed significantly.
According to Kaspersky 2015-2016 research,
“TeslaCrypt, together with CTB-Locker, Scatter and Cryakl were responsible for attacks against 79.21% of those who encountered any crypto-ransomware.”
The biggest ransomware attacks and the most prominent variants
Considering the advancement of ransomware, it is not surprising that the largest ransomware attacks have occurred in recent years.
Reports indicate that, in the mid-2000s, requests were averaging around $ 300, while today they are close to $ 500.
Usually, there is a specific deadline for the ransom by which the ransom note doubles or it is no longer possible to access the files because they are destroyed or permanently blocked.
CryptoLocker was one of the most profitable ransomware of its time: between September and December 2013, it infected more than 250,000 systems, earning more than $ 3 million before being KOed in 2014 via an international operation.
Later, its encryption model was analyzed and now an online tool is available to recover encrypted files compromised by CryptoLocker.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
The demise of CryptoLocker only led to the emergence of several imitation ransomware variants.
CryptoWall
From April 2014 until early 2016, CryptoWall was among the most commonly used ransomware varieties, with several variants targeting hundreds of thousands of individuals and companies.
In mid-2015, CryptoWall had extorted over $ 18 million from victims, prompting the FBI to warn users of the threat.
In 2015, a variety of ransomware known as TeslaCrypt or Alpha Crypt damaged 163 victims, earning attackers $ 76,522.
TeslaCrypt usually requested redemptions in Bitcoin, although PayPal or My Cash cards were used in some cases, with amounts ranging from $ 150 to $ 1,000.
Also in 2015, a group known as the Armada Collective carried out a series of attacks on Greek banks.
Instead of paying for it, the banks increased their defenses and avoided further interruptions of the service, despite Armada’s subsequent attempts.
For attacks on larger corporations, ransoms are estimated to reach $ 50,000.
However, a ransomware attack last year against a Los Angeles hospital system, the Hollywood Presbyterian Medical Center (HPMC), would have demanded a ransom of $. 3.4 million.
The attack forced the hospital back into the pre-IT era, blocking access to the corporate network, email and critical patient data for ten days.

Petya ransomware
Petya is an advanced ransomware that encrypts a computer’s master file table and replaces the master boot record with a ransom note, rendering the computer unusable unless the ransom is paid.
In May, it further evolved to include direct file encryption capabilities.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
Petya was also among the first ransomware variants to be included as part of a ransomware-as-a-service operation.
Locky ransomware
By mid-2016, Locky had solidified its place as one of the most commonly used ransomware varieties, with PhishMe research reporting that Locky’s use had overtaken CryptoWall as early as February 2016.
During Black Friday (November 25) of 2016, the San Francisco Municipal Transportation Agency was the victim of a ransomware attack that disrupted train ticketing and bus management systems.
The attackers demanded a whopping 100 Bitcoin ransom (equivalent to around $ 73,000 at the time), but thanks to the quick response and full backup processes, SFMTA was able to restore its systems within two days.
The ransomware used in the attack might have been Mamba or HDDCryptor.
In 2016, also emerged one of the first ransomware variants to target Apple OS X.
KeRanger mainly affected users using the Transmission application, but it affected around 6,500 computers in a day and a half, after which it was quickly removed.
The future of ransomware
These incidents are catapulting ransomware into a new era, in which cybercriminals can easily replicate small-scale attacks while targeting much larger companies to demand large ransoms from.
While some victims can mitigate attacks and restore their files or systems without paying a ransom, even a small percentage of attacks are enough to produce substantial revenue and incentives for cybercriminals.
As we have said several times in our articles, it is important to reiterate that paying the ransom does not guarantee access to your files.
The best ransomware solution is decrypt files without paying the ransom.
CryptoLocker ransomware “extorted $ 3 million from users but did not decrypt the files of everyone who paid,” CNET reports based on the results of a Security Ledger article.
A Datto survey found that in ¼ of incidents in which ransom was paid, attackers avoided unlocking victim data.
Incidentally, ransomware operations continue to find more creative ways to monetize their efforts, as was the Petya and Cerber ransomware that pioneered ransomware-as-a-service schemes.
The potential profit for ransomware authors and operators also drives rapid innovation and fierce competition among cybercriminals.
PetrWrap ransomware, for example, was built using cracked code from Petya.
For the victims, knowing where the code comes from does not matter: whether you have been infected with Petya or PetrWrap, the result is the same, your files are encrypted with such a powerful algorithm that no ransomware decryption tools currently exist.
What are the prospects for ransomware?
A new report from the National Cyber Security Center (NCSC) and the UK’s National Crime Agency (NCA) warns of developing threats such as ransomware-as-a-service and mobile ransomware.
The pace at which the IoT is growing, combined with IoT devices’ widely reported insecurity, provides a whole new frontier for ransomware operators.
Best practices for ransomware protection, such as regular backups and software updates, don’t apply to most connected devices, and many IoT vendors are slow or just plain careless when it comes to releasing software patches.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
Now, as businesses increasingly rely on IoT devices to perform operations, there could be a spike in ransomware attacks on these types of devices.
Critical Infrastructure represents another worrying target for future ransomware attacks: DHS Business Performance Management Office Director Neil Jenkins warned at the 2017 RSA conference that water services and similar infrastructure could be attractive targets for attackers.
Jenkins referred to a January 2017 ransomware attack that temporarily disabled components of an Austrian hotel keycard system as a potential predecessor for more significant infrastructure attacks to come.
How to protect yourself from ransomware attacks
There are some steps that end-users and businesses can take to reduce the risk of falling victim to ransomware significantly.
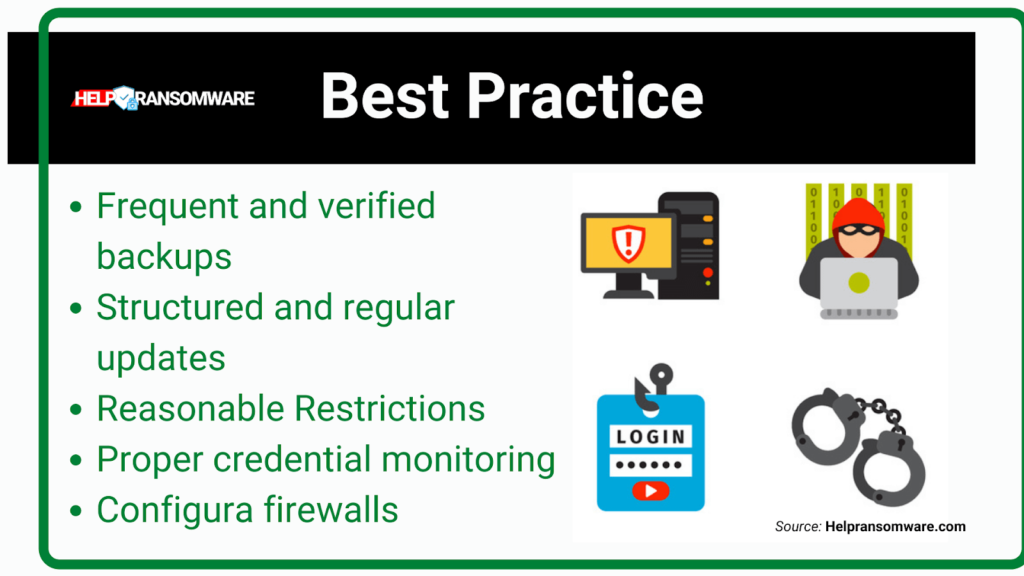
Here are four basic security practices any business must follow:
- Frequent and verified backups: Backing up all files and systems is one of the most powerful defenses against ransomware. All data can be restored to a previous save point.
- Structured and regular updates: The software creator regularly updates most software used by companies.
- Reasonable Restrictions: Certain restrictions should apply to those who:
- Work with devices that contain company files, documents and/or programs;
- use devices connected to corporate networks that could be made vulnerable;
- are third party or temporary workers.
- Proper credential monitoring: any employee, contractor, and person who is granted access to systems create a potential point of vulnerability for ransomware. Replacement or failure to update passwords and improper restrictions can lead to even greater chances of attack.
While these practices are fairly well known, many people fail to back up their data regularly, and some companies only do so within their own networks, which means that a single ransomware attack can compromise all backups.
Effective defense against ransomware largely depends on proper education.
Educating employees about the telltale signs of ransomware distribution tactics, such as phishing attacks, drive-by downloads, and spoofed websites, should be a top priority for anyone who uses a device today.
Businesses should also implement security solutions that enable advanced threat protection.
In any case, if you have been damaged by ransomware, do not despair, avoid doing it yourself and contact qualified specialists like those of HelpRansomware, who will be able to solve your problem with the best solutions.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.



