What is data encryption and measures against ransomware attacks? Discover decryption tools.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
What is data encryption?
Data encryption is the art and science of protecting information by converting it into an undecipherable format.
This process ensures that only those with a decryption key can access the original information.
According to a more detailed definition provided by NIST (National Institute of Standards and Technology), encryption is
“Cryptographic transformation of data (called “plaintext”) into a form (called “ciphertext”) that conceals the data’s original meaning to prevent it from being known or used.
If the transformation is reversible, the corresponding reversal process is called “decryption,” which is a transformation that restores encrypted data to its original state.”
In an increasingly digital world, where information is the most valuable asset, encryption has become essential to ensure the security of online transactions, the protection of personal data, and the safeguarding of corporate information.
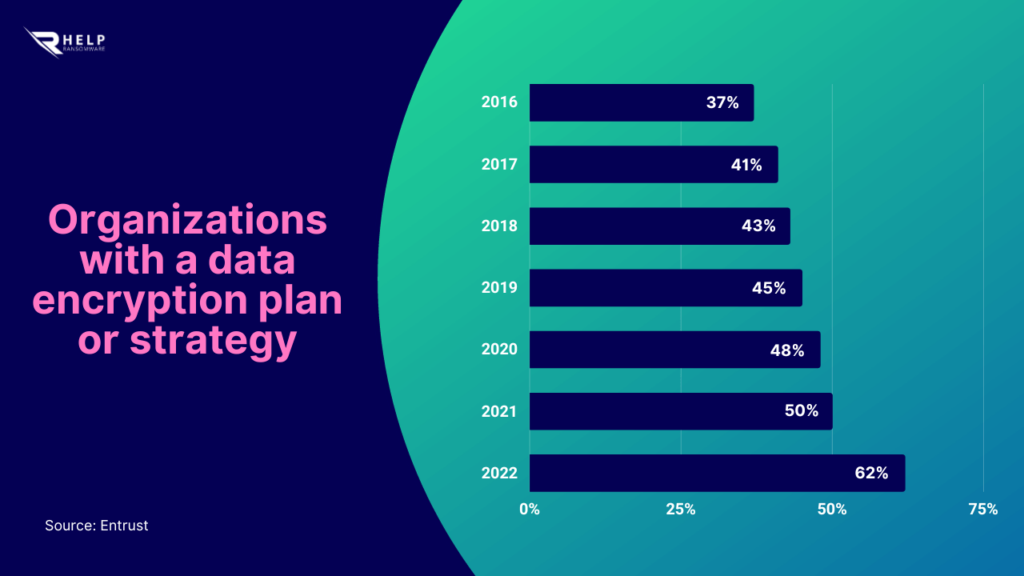
In fact, from 2016 to 2022, the percentage of organizations with a data encryption plan or strategy will increase from 37% to 62%, according to Entrust’s analysis.
The basics of data encryption for ransomware protection
Encryption is not only a tool to protect information, it has become a critical line of defense against ransomware attacks.
Here are some key data encryption principles to protect against ransomware:
- Robust algorithms, such as AES or RSA, known for their resistance to attack;
- Secure management of encryption keys so that they are kept separate from the encrypted data and access to those keys is limited;
- Two-factor authentication (2FA) to ensure that only authorized users can decrypt ransomware files;
- Regular backups, in secure locations, preferably offline, to ensure they can be recovered in the event of an attack;
- Ongoing updates to protect against the latest vulnerabilities;
- Training users on good security practices, such as recognizing and avoiding phishing attempts that can lead to ransomware infections;
- Continuous monitoring and detection of suspicious activity to quickly identify and respond to attacks.
By implementing these core principles, organizations can significantly strengthen their defenses against ransomware attacks and ensure that their data remains secure and accessible.
The most effective data encryption algorithms against ransomware attacks
The choice of encryption algorithm is essential to ensure data security.
Some of the most effective algorithms against ransomware attacks are:
- AES (Advanced Encryption Standard), which has become the de facto standard for data encryption due to its robustness and speed;
- RSA, an asymmetric public key encryption algorithm widely used to secure online transactions;
- ECC (Elliptic Curve Cryptography), known for its ability to provide high security with shorter keys, making it more efficient.
By using strong encryption methods and established security principles, organizations can significantly reduce the risk of being affected by any type of ransomware.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
The correlation between data encryption and ransomware attacks
While encryption was originally designed as a tool to protect information, cybercriminals have turned this notion on its head and used it as a weapon.
In fact, in many cybercrimes, hackers use data encryption to block access to victims’ files.
Once the data is encrypted, criminals demand a ransom, often in cryptocurrency, to provide the decryption key.
This twisted use of encryption has created new cybersecurity challenges, making it even more important for organizations and individuals to understand and implement encryption correctly.
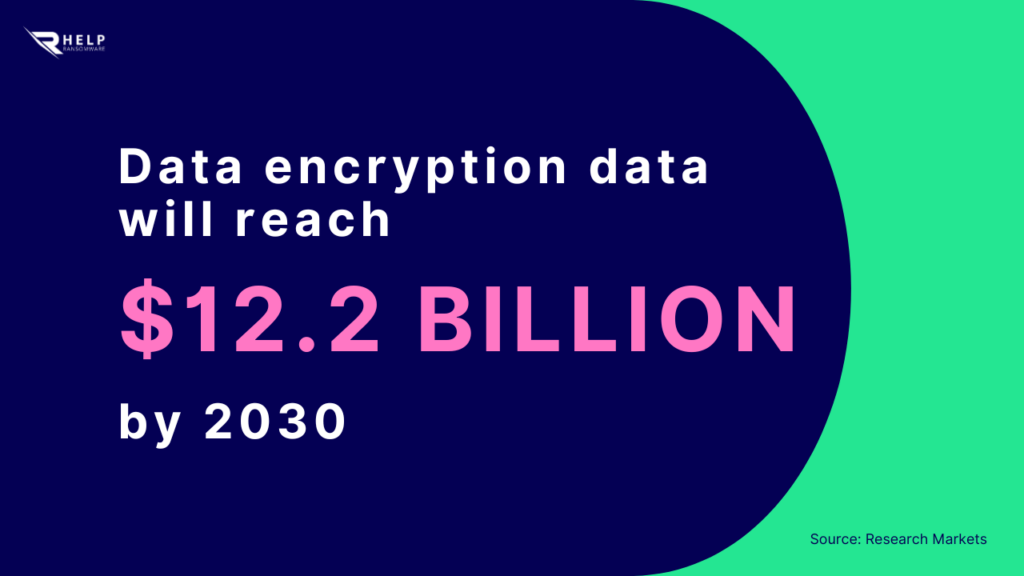
However, the dual use of cryptography also justifies the high growth rates of this market reported by Research Markets: from $4.3 billion in 2022 to $12.2 billion in 2030.
How data encryption is used in ransomware attacks
Specifically, data encryption in ransomware attacks follows this process:
- Infiltration and installation: it all starts when a ransomware malware manages to infiltrate a system; once inside, the ransomware installs itself or with the unwitting help of the user;
- File selection: ransomware scans the system looking for specific files to encrypt, which may include documents, images, databases, and other files that are critical to the user or organization;
- Encryption process: once the target files are identified, the ransomware begins the encryption process using strong encryption algorithms;
- Key generation: during the encryption process, the ransomware generates a unique decryption key that is essential for decrypting files;
- Ransom note: Once all target files have been encrypted, the ransomware presents the user with a note with instructions on how to pay a ransom, often in cryptocurrency, to obtain the decryption key and recover the files.
In some recent attacks, cybercriminals may also steal a copy of the data before encrypting it.
This is called double extortion ransomware, which allows hackers to further threaten victims with data exposure if the ransom is not paid.
Ransomware decryption and advanced data encryption techniques
The challenge of decrypting data affected by ransomware is compounded by the complexity of the encryption algorithms used.
Sophos’s 2023 report found that data encryption was effective in 76% of ransomware attacks.

Business and professional services reported the highest frequency of data encryption (92%).
On the other hand, IT, Technology and Telecommunications had the lowest rates, with hackers succeeding in encrypting data in only 47% of attacks.
However, with the advent of advanced techniques and continued research in data encryption, solutions have emerged that can help open encrypted files without necessarily paying the ransom.
These solutions often take advantage of vulnerabilities in ransomware or mistakes made by cybercriminals during the attack.
Encryption strategies for data affected by ransomware
The first line of defense against a ransomware attack is always prevention.
However, if you are already a victim of ransomware data encryption, there are several strategies that can help you recover encrypted files, including:
- Free decryption tools, often provided by security researchers or specialized companies;
- Restoring data from recent backups that were not compromised by the attack;
- Collaboration with IT security experts who can provide specific assistance and advice.
HelpRansomware is the world leader in recovering data encrypted by ransomware.
Its technology experts provide 24/7 support to ensure fast and efficient action in the event of an attack.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
Specialized data decryption tools and technologies
In an effort to combat the threat of data encryption, numerous ransomware decryption tools and technologies have been developed to help victims decrypt their data.
Platforms such as No More Ransom offer free decryption tools for many ransomware variants.
Other security companies offer specialized services and software to help organizations protect and recover from ransomware.
Recent advances in data encryption to combat ransomware
The cyber threat landscape is constantly evolving, and so are the solutions and technologies used to combat these threats.
Data encryption, which is at the heart of ransomware attacks, has seen notable advancements in recent years.
Here are some of the most important:
- Post-quantum algorithms: designed to withstand attacks even from quantum computers, ensuring data security even in a future dominated by quantum computing;
- Homomorphic encryption: allows you to perform computations on encrypted data without decrypting it first, which could offer new ways to securely analyze and manage data, reducing the risk of exposure to ransomware during processing operations.
According to Global Market Insights, the homomorphic cryptography market reached $161 million in 2022 and is expected to reach $300 million by 2030;

- Split-key techniques: splitting an encryption key into multiple parts that require all parts to be present in order to decrypt the data, making it more difficult for cybercriminals to gain full access to the encrypted data;
- Blockchain: its decentralized nature and advanced cryptographic capabilities can provide new ways to protect data and verify the integrity of backups;
- Artificial intelligence and machine learning: by analyzing behavioral patterns and continuously learning, they can identify attack attempts in real time and block them before they cause damage;
- Assisted decryption: the combined use of distributed computing power and advanced analysis techniques makes it possible to decrypt ransomware files without necessarily having the original key;
- Integrated security frameworks: integrating multiple encryption, authentication, and monitoring techniques to provide a comprehensive security solution against multiple types of threats, including ransomware.
These advances are just the tip of the iceberg when it comes to innovation in data security and encryption.
Prevention and protection against ransomware attacks
Preventing ransomware attacks includes:
- Implementing advanced security solutions such as firewalls, anti-ransomware software, and intrusion detection systems;
- Regular software updates to fix any vulnerabilities.
Sophos reports that vulnerability exploitation was the primary cause of ransomware attacks in 36% of cases;

- Educating users on good security practices, such as avoiding suspicious emails and not downloading attachments or software from untrusted sources.
Implementing encryption strategies within corporate systems is an effective way to protect yourself from ransomware.
Data encryption prevention and recovery strategies
In addition to preventative measures, it is essential to have a recovery strategy in place in the event of an attack.
This includes having regular backups of your data, preferably in offline locations or secure clouds, that can be restored in the event of an attack.
It is important not to underestimate the importance of having offline backups in case the entire corporate network is compromised.
Data reported by VPN Alert highlights this point: approximately 50% of data breaches involving data encryption occur in the cloud.

Recommended practices to strengthen the security of data encryption
To ensure maximum ransomware defense, organizations should follow some recommended practices.
These include:
- Use tested and approved data encryption algorithms;
- Securely managing encryption keys by avoiding storing them in the same location as the encrypted data;
- Implementing strong security policies that govern data access and use.
It is also important that all employees within an organization, regardless of their level of use of corporate devices, have adequate knowledge of online threats.
For example, Sophos data shows that sectors such as IT, technology and telecoms have the lowest levels of vulnerability exploitation attacks (22%) and compromised credentials (22%).

This reflects the high level of cyber defense that these sectors have achieved.
However, these same industries have the highest rates of email intrusion attacks (51%).
These numbers only underscore the importance of keeping all aspects under control.
Security and detection tools to mitigate ransomware through data encryption
Data protection requires a layered approach.
The tools used go beyond data encryption to not only help in ransomware detection, but can also play a critical role in mitigating the damage in the event of a breach.
Here is a detailed analysis of the tools and technologies that make up the ransomware defense:
- Endpoint Detection and Response (EDR): continuously monitor activity on devices, detect suspicious behavior, and respond quickly to isolate threats in real time;
- Sandboxing: creates an isolated environment where suspicious files can be safely executed, analyzed, and then blocked before they can infect the main system;
- Next-generation firewalls (NGFW): incorporate advanced features such as deep packet inspection and integration with other security solutions to block complex attacks;
- Intrusion Prevention Systems (IPS): monitor network traffic for suspicious activity or known malware signatures and can actively block attacks before they reach target devices;
- Training: educational tools and simulation platforms as a means of ransomware protection, as they help users identify and respond to intrusion attempts;
- Patch and vulnerability management: automatically monitor and manage software updates to ensure all systems are protected against the latest known vulnerabilities;
- Forensic analysis tools: in the event of an attack, help experts examine the system to understand how the breach occurred, what data was compromised, and how to prevent future attacks;
- Threat intelligence solutions: provide real-time information about the latest threats and vulnerabilities, allowing organizations to adapt their defenses accordingly.
The combination of these tools and technologies ensures that organizations are not only well protected against ransomware attacks, but also ready to respond and recover quickly in the event of an incident.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
Ransomware removal: data encryption tips and considerations
Removing ransomware is a delicate process that requires a combination of technical skills, advanced tools, and a deep understanding of specific ransomware variants.
Ransomware families, such as WannaCry, Ryuk, GandCrab, etc., have unique characteristics that can affect removal and recovery strategies.
Here are some key tips and considerations:
- Device isolation: this can help prevent ransomware from spreading to other systems or the network;
- Ransomware identification: it is important to identify the specific ransomware family or variant to proceed with specific items;
- Avoid payments: there is no guarantee that criminals will provide the decryption key, so you should never pay the ransom;
- Use decryption tools: not all ransomware variants have developed free decryption tools, and remember that doing it yourself always carries some risk;
- Restore from backups: this could allow you to restore encrypted files without having to deal with the ransomware directly.
Sophos reported that in 70% of cases where data had been encrypted, it was possible to recover it thanks to the presence of backups.

Another 21% of users were able to recover their data using a combination of methods.
If you are unsure of how to proceed, or if the situation seems particularly complex, it may be helpful to consult cybersecurity experts or companies that specialize in ransomware removal.
Contact HelpRansomware and provide an example of data encryption you’ve undergone to get a preliminary analysis in no time.
Steps for dealing with a ransomware infection and data encryption
In the case of data encryption, we have already said that it is essential to act quickly.
Protection doesn’t end when the ransomware is deleted.
In fact, after removal, you need to perform thorough security checks to ensure that the system is secure and that there are no remnants of the ransomware.
At a later stage, you should also consider taking preventative measures such as user training, regular software updates and patches, and installing advanced security solutions.
Finally, continuously monitoring your system and network for signs of suspicious or unauthorized activity will help prevent future attacks.
The importance of working with ransomware removal experts
Ransomware attacks can be devastating, but you’re not fighting them alone.
Working with cybersecurity experts can provide valuable perspective, tools, and resources to combat the attack.
HelpRansomware professionals have the experience and knowledge to navigate the complexities of ransomware attacks, and can provide customized solutions for any situation.
Learn how our team works and choose the best for your side.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
Ethical and legal aspects of fighting ransomware through data encryption
While the fight against ransomware is primarily technical, it is also inextricably linked to ethical and legal issues.
Data encryption, which is at the heart of these attacks, raises a number of challenges and considerations from both a moral and legal perspective.
On the ethical side, there is the question of paying ransoms.
While payment may seem like a quick fix to recover critical data, there is a moral argument that paying more money encourages cybercriminals.
In addition, there is always the risk that the criminals will not provide the decryption key once paid, further compromising the victim.
From a legal perspective, the situation is even more complex.
While many countries are tightening their laws against cybercrime, the transnational nature of ransomware makes it difficult to prosecute and convict perpetrators.
In addition, some lawmakers are exploring the possibility of making ransom payments illegal, with the goal of discouraging the practice and reducing funding for criminal groups.
As the FBI has already done:
“Companies that facilitate ransomware payments not only encourage future payment demands, but also risk violating OFAC regulations.”
Another legal consideration is the liability of organizations.
If an organization is compromised due to security negligence, it could be held liable for the loss of customer or third-party data.
This increases the need for organizations to not only protect their data, but also to ensure that their security measures are up to date and compliant with current regulations.
Conclusions
Data encryption is a powerful tool that has the potential to both protect and harm.
From this guide, we can draw the following conclusions:
- Data encryption is the art and science of protecting information by converting it into an undecipherable format;
- From 2016 to 2022, the percentage of organizations with a data encryption plan or strategy will increase from 37% to 62%;
- Some of the most effective algorithms against ransomware attacks include AES, RSA, and ECC;
- The global data encryption market will grow from $4.3 billion in 2022 to $12.2 billion in 2030;
- In 2023, data encryption was effective in 76% of ransomware attacks;
- Approximately 50% of data breaches involving data encryption occur in the cloud;
- In 70% of cases where data was encrypted, recovery was possible due to the presence of backups.
While ransomware attacks continue to pose a significant threat, through education, prevention, and collaboration, we can build a safer digital future for everyone.
HelpRansomware, a global leader in decrypting ransomware-infected data for years, is bringing attention to all of these steps.



