With the new HelpRansomware guide, you will find out what spyware is and how it works. We explain how to recognize the virus and eliminate it from a device.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
What is spyware
Spyware is a widespread type of malware.
As stated in the glossary of the NIST (National Institute of Standards and Technology), spyware is:
“Software that is secretly or surreptitiously installed into an information system to gather information on individuals or organizations without their knowledge; a type of malicious code.”
The term comes from the word spy and is indicative of how this malware behaves.

Considering that in 2021, cybercriminals are producing 230,000 new malware samples per day, it is easy to understand the importance of knowing how to protect yourself against this cyber threat.
What kind of software is spyware?
Spyware is malicious software that spies on the victim by collecting information about their online activity without their consent.
It is called intrusion software or spying software.
In the text of the European Commission of 10 October 2018/1922, which regulates the export of dual-use items, there is the following definition:
“Software specially designed or modified to avoid detection by ‘monitoring tools’, or to defeat ‘protective countermeasures’, of a computer or network-capable device.”
There are three functions that this software performs:
- Extraction of data and information from a device connected to the network;
- Modification of system or user data;
- Modification of the standard execution path of a program or process to allow execution through externally supplied instructions.
Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
How does spyware work?
Like many cybercrimes, spyware works by stealing data from the victim.
Hackers use this type of malware to collect all kinds of information: passwords, credit card details, personal data.
Then there is a form of spyware that is practically legalized: cookies.
Thus advertisers spy on your online activities to offer you personalized ads targeted to your interests; the risks are lower than ordinary spyware and are limited to the single website that uses them.
Additionally, there are examples of spyware used by governments to collect sensitive information.
This type of attack is known as govware or policeware.
This summer, we saw the Pegasus spyware, from which the Pegasus Project was born.
Software produced by an Israeli agency has been sold to government agencies in several countries, including Morocco, Saudi Arabia, Rwanda, and Mexico, to spy on criminals, journalists, and political activists.
In general, once it enters your device, there are several functions that spyware can take on:
- Send unsolicited advertising (spam);
- Send phishing emails to redirect you to fake e-commerce sites or to push you to communicate confidential information;
- Modify your PC‘s operating system so that it automatically runs the malware every time it starts up, enhancing its damage.
Many free programs on the Internet hide malware of this type; in some cases, it is the same application that promises to free spyware that installs it on your device.
How do spyware attack?
Spyware, unlike ransomware, cannot spread on its own.
This malware needs human intervention to be installed.
Cybercriminals use a variety of social engineering techniques to push the unsuspecting victim to download spyware.
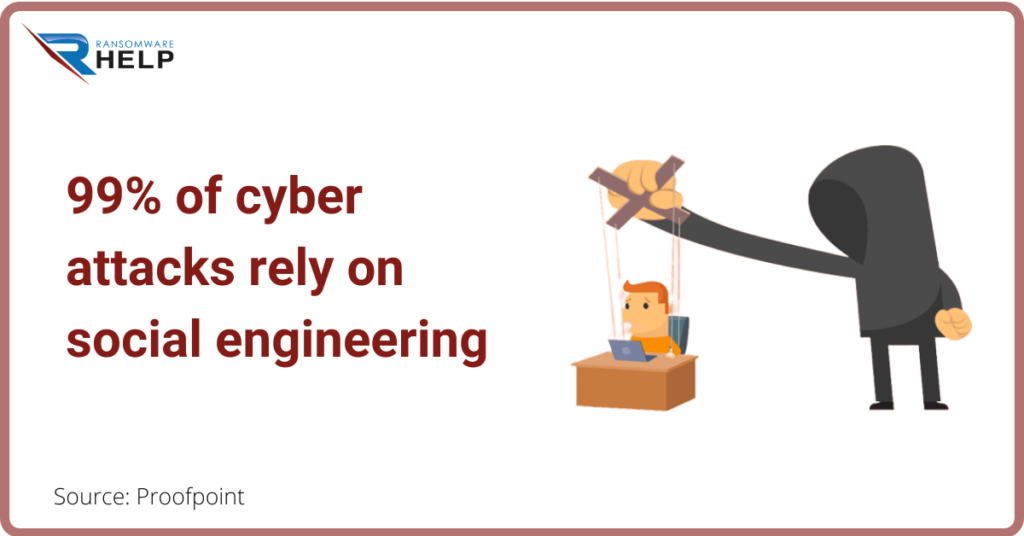
99% of cyber attacks rely on social engineering.
Some of the methods by which it infiltrates your device:
- Security vulnerabilities: clicking on links in phishing emails or pop-ups in an advertising banner can trigger the infection. Pay attention to the content and sites you visit.
- Misleading marketing: spyware often lurks in downloads or drive-by downloads of programs to install on your device.
The same thing happens with bundled software. Check that the sites you download from are trustworthy and avoid giving too many permissions to any application.
- Trojans, worms, backdoors, doxing attacks: in addition to causing various damage, these viruses can also distribute spyware.
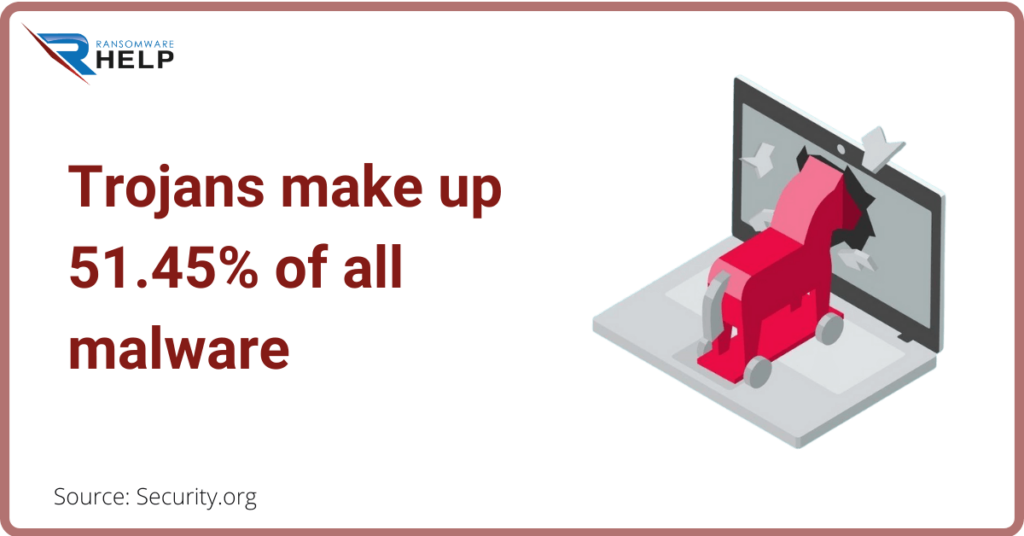
Trojans make up 51.45% of all malware.
- Mobile spyware: they are increasingly common and harder to identify.
The attack can occur either through legitimate applications reworked with malicious codes; both through fake and malicious applications.
The biggest problem is that, even if you uninstall the software that started the infection, the spyware remains on the device and continues to work.
What does spyware do?
Regardless of how the spyware enters your PC, it starts infecting it by acting in the background.
The software collects data and monitors the victim’s activities.
- Record keystrokes: so-called keyloggers spy on everything you type and use it to store credit card numbers, login credentials, and passwords;
- Track online activity: we have already said that cookies can be considered spyware because they track your online movements; by doing so, they allow advertisers to grab your attention through tailored advertising;
- Take control of your computer: some Trojan-type spyware modifies security settings to allow remote control of the device.
It then uses the collected information to take malicious action or to promulgate ransomware attacks.
How do you recognize spyware?
It is complicated to recognize the presence of spyware.
If you notice suspicious behavior on your device, contact a specialized company: HelpRansomware, with over twenty years of experience in the IT security sector, can provide you the appropriate support in recovering encrypted files.
Here are the signs that may reveal the presence of spyware:
- Slowing down of the device, both in the execution of programs and in the responses to commands;
- Unexpected pop-up messages that hide adware;
- Changes to the homepage of the search engine or the favorites bar;
- The battery that wears out more quickly;
- Difficulty accessing secure sites;
- Unusual increase in data or network usage;
- Security systems and antivirus do not work.
All of these can be clues that spyware is looking for and stealing information on your device.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
How to avoid spyware?
To avoid spyware, you need to start with a proactive protection attitude.
First of all, it’s good to understand what you are dealing with, which is why the HelpRansomware experts have written this guide.
As users’ knowledge and awareness increase, cybercriminals will have a more challenging time getting into devices.
Start by following these simple rules:
- Do not open emails from unknown senders: around 92% of malware is transmitted via email;

- Do not download files unless they come from a trusted and verified source;
- Move the mouse over the links to check the URL: carefully observe and check that it is written correctly and refer to an HTTPS site;
- Set ad blocking to avoid malvertising cases;
- Install a cybersecurity program that includes real-time protection to stop spyware before it’s even activated on your device.
By following these simple steps, you can reduce the risk of getting infected with malware and, at the same time, you can prevent ransomware attacks.
How do you remove the spyware?
We have already mentioned that it is complicated to identify the presence of spyware on your device.
Similarly, if the infection has occurred successfully, it won’t be easy to remove it.

63% of small businesses feel that malware attacks are becoming too hard to deal with.
Despite the difficulty, there are several effective ways to remove spyware:
- Use malware and spyware removal software to clean up your computer or phone.
Pay close attention to the program you use, as some software is spyware itself.
- Clear your internet cache to delete any remaining traces of the malware.
- Change all login credentials (username and password) of any account.
If the attack occurred on your phone, we recommend that you first perform the removal in emergency mode or offline; this will prevent the spyware from connecting to other networks and installing itself again.
To proceed, follow these directions:
- Unroot or jailbreak your device: many spyware require your phone to be rooted or jailbroken to work.
In the case of iPhones, you can restore the device to its pre-jailbroken state by performing an iOS update.
- If this option did not work, then consider resetting to factory settings.
In this way, the device will return to its original state, eliminating all data and programs downloaded up to then.
Before doing this, make a backup of your data.
However, these measures may not be enough.
The only truly 100% effective solution is to contact HelpRansomware; our experts will restore the files.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
What are the most common spyware?
Spyware can take extremely changing forms.
Below we see what the most common categories are and how they work.
- Password stealers: these applications infect devices to obtain passwords and logins.
One particular password stealer is the banking trojan, which acts to obtain credentials from financial institutions.
The Trojan-Banker.AndroidOS.Asacub malware application, for example, attacked over 250,000 users.

These spyware exploit security vulnerabilities to modify web pages or take action on transactions without leaving a trace.
In addition, they can transmit the collected information to a remote server for retrieval.
- Infostealer: are applications that scan computers for any information.
Username, password, email addresses, browser history, system information, documents, media files: this is their loot.
- Keylogger: also known as system monitors, they store all the activities carried out on the device.
These spyware record keystrokes, sites visited, search history, chat or email conversations, and system credentials.
They usually take screenshots of the active window at regular intervals.
Furthermore, they can transmit images, audio, and video even by accessing the printers connected to the infected device.
Belonging to these groups, some spyware have stood out over the years for the amount of damage done to users.
Here are some of the most dangerous:
- FinFisher: It was designed to be used by law enforcement and governments but ended up serving the purposes of cybercriminals;
- GO Keyboard: it was an application that can be easily downloaded from Google Play which, by spying on consumers, managed to steal a lot of personal data;
- Look2Me: this powerful spyware made the PC securely accessible every time it was turned on, making the threat nearly impossible to detect;
- Trojan.Zlob: in addition to spying on the victim, it distributed pop-up ads and swapped PC controls.
What are rootkits, and what is their purpose?
Rootkits also fall into the category of malware.
As the name implies, they are kits or sets of tools that allow the hacker to access the computer remotely.
Rootkits behave like backdoor programs, giving the hacker the ability to install and uninstall specific components.
As with other malware, the most common vector of infection is a vulnerability in the operating system or the installation of an application.
In any case, the ultimate goal of rootkits is to steal information from the victim.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
How do Hijackers viruses behave?
Hijackers viruses manifest themselves with the intrusion of unwanted software into an Internet browser whose activity it alters.
A browser hijacker is a malware that can change browser settings without permission.
In this way, it redirects the user to websites other than the original one.
The aim is to generate traffic on specific websites from which the hacker makes a profit or implement scams starting from those websites.
One of the most common methods of scamming the victim is by changing the browser home page.
Every time the user connects to the Internet, he directly accesses the scam site.
The software used for hijacking attacks acts by replacing the browser home page URL with the one indicated by the hackers.
A system compromised by the Hijackers virus has some typical characteristics:
- Unstable browser;
- Home page changed;
- Opening of numerous pop-ups or unsolicited web pages;
- HOSTS file modified;
- Loss of performance of the device;
- Unknown processes running.
What is the best anti spyware?
To avoid being attacked by spyware, it is essential to have good anti spyware installed on your device.
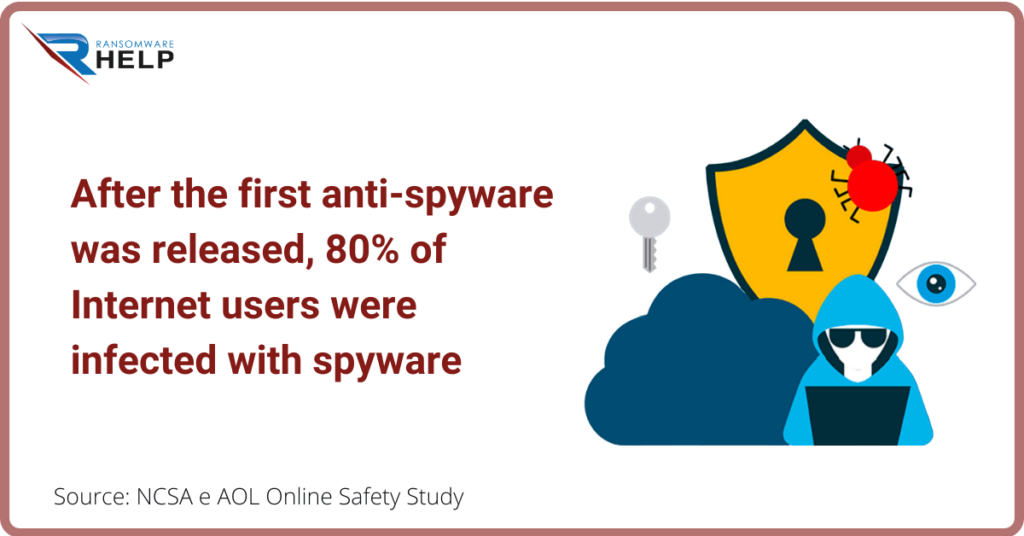
In October 2004, four years after the first anti spyware was released, America Online and the National Cyber-Security Alliance performed a survey.
The result? About 80% of all Internet users had their system infected with spyware.
In addition, 95% of respondents reported that they have never granted permission to install the application responsible for the attack.
As we have already done in the case of ransomware, giving you a list of decryption tools, now we see some of the most useful against spyware.
It is one of the best software out there and is available in a free and paid version.
The latter is particularly suitable for those who use devices for work and need advanced protection.
It is ideal if you already have a good antivirus installed on your PC.
It is one of the most complete software available.
It protects the files on your PC that are encrypted, making them inaccessible to malicious people.
In addition, it protects mailboxes and websites through very efficient parental control.
We mention this antispyware because it is particularly effective in removing browser hijackers.
The program is free and does not require installation on your PC.
Sometimes, however, the presence of antivirus or antispyware is not enough to protect you and your devices, especially if the attack has already occurred.
In these cases, only the action of specialists can counteract the advance of spyware.
Contact HelpRansomware to get the necessary protection against all types of ransomware.
Expert knowledge, combined with the powerful technology at their disposal, is undoubtedly more effective than any software out there.
Conclusions
In this guide, we’ve shown you everything you need to know about spyware and other types of malware threats.
Below, here are the conclusions you can draw from the text:
- Spyware is a widespread type of malware that spies on the victim’s activities and information without them noticing;
- Spyware is part of intrusion or spying software;
- This malware does not act alone, but it needs human intervention to be installed;
- It is complicated to realize that you have been attacked by spyware, and it is equally challenging to remove it from your device;
- Another type of malware is represented by rootkits, which allow hackers to take control of the PC remotely;
- Hijackers, on the other hand, are malware that can change browser settings without permission.
If you have been the victim of a cyberattack, such as ransomware, the best solution is to contact HelpRansomware.
Our decades of experience in cyber security make us the number one company in the world in digital security and protection for businesses and government agencies.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.




