Find out how to decrypt ransomware files and recover your data after an immediate attack on the cyber security of your systems. [GUIDE 2022]

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
What does it mean to decrypt Ransomware files?
Decrypting ransomware files means cracking a file that has been attacked and made inaccessible by malware.
The term ransomware, in fact, indicates a class of malware that, once infected with the computer, makes data inaccessible and requires the payment of a ransom to restore it.
On a technical level, it is an encrypted Trojan, with the purpose of extorting money by seizing files that have been rendered unusable.
It is a very profitable type of cyber attack for those who launch it, and for this reason, it has become widespread in recent years.
The investigation conducted by the US agency FinCEN (Financial Crime Enforcement Network) gives strong data on the growth of ransomware attacks.
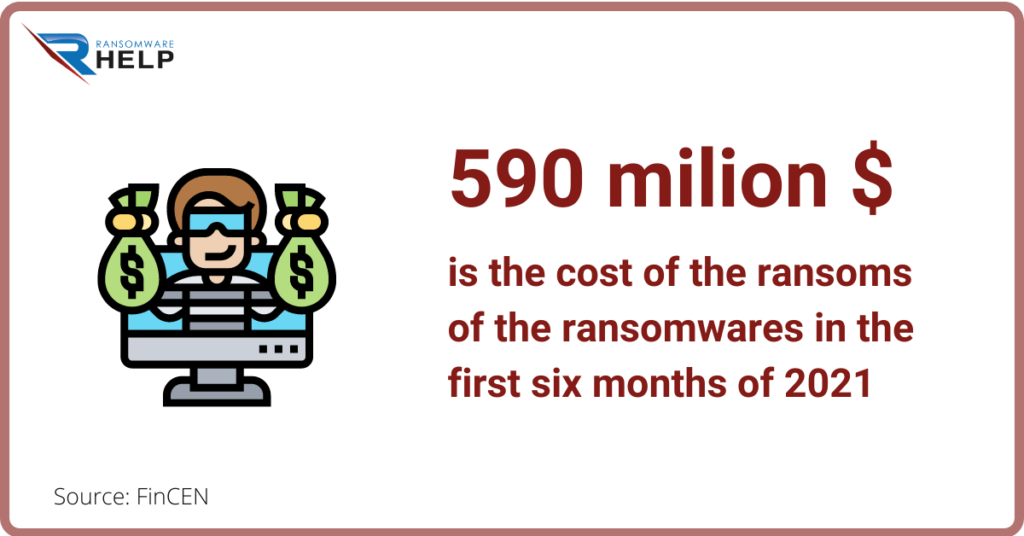
In the first six months of 2021, payment requests for ransomware reached $ 590 million.
This is an increase of +42% compared to the total of $ 416 million recorded for the whole of 2020.
For this reason, ransomware can be considered the main cyber threat.
But how does ransomware manifest itself?
Instead of the classic desktop wallpaper, the user sees a notification that appears to come from the police or another security organization.
This notification contains blackmail: paying the sum to receive the password to open encrypted files.
Till date, the ransom request often involves a payment in Bitcoin.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
What happens when Ransomware encrypts a file?
Ransomware can infect a computer in several ways.
However, one of the most popular methods out there is definitely phishing.
It is malicious spam sent through unwanted emails containing infected links or attachments.
Thinking that the email is authentic, the user clicks on the attachments by downloading the virus directly to his device.
From then on, the ransomware infiltrates the system and starts encrypting files.
Through the use of complex algorithms, encryption acts on the encoding of files and on the sensitive data they contain.
This coding is not inherently harmful; in general, it has only the task of preventing unauthorized access and tampering with malicious people.
According to the National Institute of Security and Technology (NIST), the word cryptography means:
“The discipline that embodies the principles, means, and methods for the transformation of data in order to hide their semantic content, prevent their unauthorized use, or prevent their undetected modification.”
In the case of ransomware, however, by encrypting files, hackers ensure that the user cannot access her data.
An encrypted file becomes unreadable without a decryption key.
This key usually takes the form of a password or passphrase, which is configured as a string of alphanumeric digits.
Is it possible to decrypt files infected with Ransomware?
The answer is positive: yes, it is possible to decrypt files infected with ransomware.
There are many ransomware decryption tools to deal with the attack.
The problem, however, is that every ransomware needs its tool, and it is not always easy to recognize what type of virus it is.
The best option is always to contact specialists.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
HelpRansomware relies on a team of IT experts who are constantly developing new technologies and solutions to counter ransomware attacks.
On the other hand, you never have to pay the ransom.

According to Sophos’s analysis, about 92% of the companies that paid the ransom did not receive the decrypted files.
Indulging criminals only fuels their illicit activities.
Can files encrypted by Ransomware be recovered?
Both to decrypt and recover encrypted files, it is possible to succeed.
The process, however, is far from straightforward: each ransomware has a different encryption system and, therefore, a different method of decryption.
However, decrypting a file does not mean recovering it.
Files attacked by ransomware, even after decryption, can be damaged or corrupted.
Even in this case, the advice is to turn to specialized companies and avoid the do-it-yourself route.
The tools that are available online are handy but require the user to have a certain level of familiarity with the technology.
Furthermore, these tools present an additional problem: by downloading a software of dubious origin, you could be responsible for downloading malware on your PC.
Some ransomware exploit bugs in execution programs such as Adobe Flash or Java.
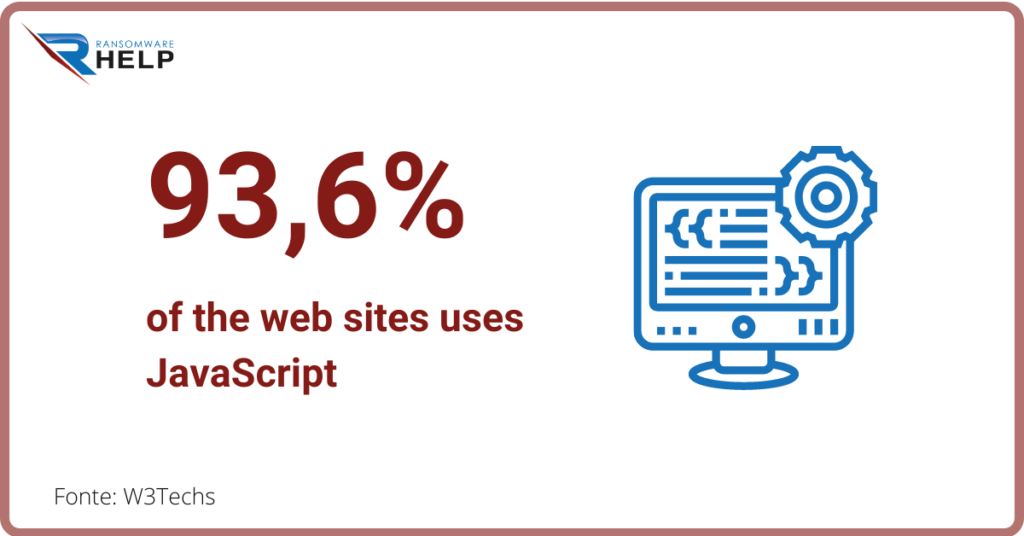
As also researched by W3Techs, JavaScript is used by 93.6% of websites, making it particularly attractive to hackers.
How to decrypt Ransomware files?
To decrypt Ransomware files, you need special softwares.
Each ransomware has its decryption tool, which makes the process more difficult.
There are two main types of problems:
- Decryption of a software can be costly, especially if it works on the more complex types of encryption;
- Using a decryption software isn’t easy, so you need to have various non-basic computer skills.
For this reason, DIY tools are not very successful.
Instead, you should contact a specialist who can analyze your situation and determine what options are available at the time of the request.
Make sure that the company in question can provide you with the following services:
- Understand the ransomware variant and explain to the customer what to expect;
- Analyze the malware to determine if encryption can be breached;
- Understand which carrier caused the attack and act with preventive methods;
- Change broken or malfunctioning decryption programs that cause delays in decrypting files;
- Repair the damaged database or files.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
If you need a company with such experience, contact HelpRansomware, ready to help you 24/7.
As you can see, decrypting files is only the last step because first, you need to take a series of other measures.
The early stages of analysis are critical to gather informations on preventing the next ransomware attack.
Decrypt Cerber Ransomware files
Cerber Ransomware is a virus that encrypts a user’s data using AES-265 and RSA methods.
The virus is a Trojan horse frequently spread through spam emails containing infected attachments or malicious links.
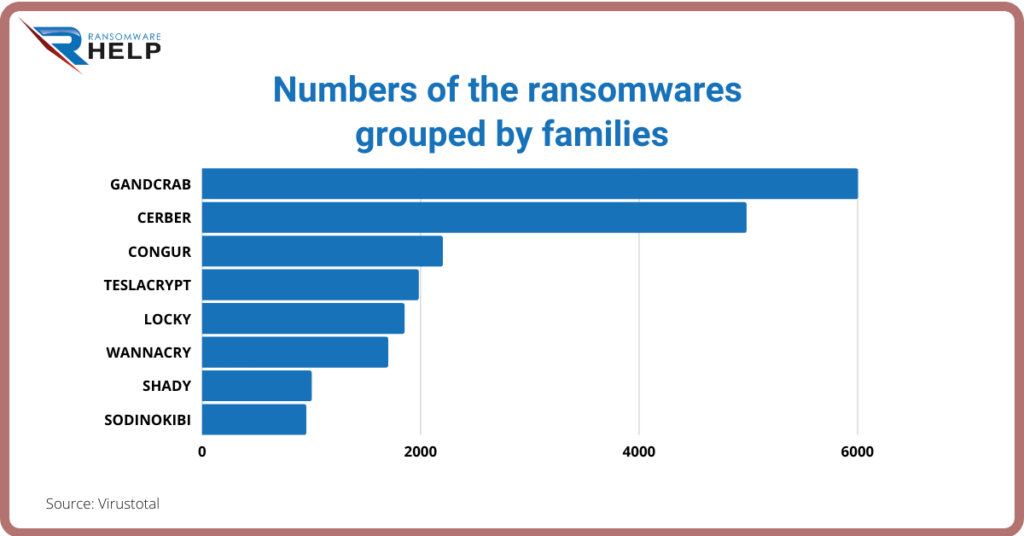
Among the ransomware families, Cerber is second only to GandCrab in the number of viruses it includes, as seen in the Virustotal report.
Once the software enters the computer, it encodes, renames, and encrypts the files on the various disks (internal and external).
During data encryption, the virus creates three files #Decrypt My Files # .txt, #Decrypt My Files # .html, and #Decrypt My Files # .vbs which contain instructions to pay hackers.
These files are placed in every folder where Cerber files are present.
No tool is 100% effective for decryption, which is why many users tend to pay the ransom.
It is essential to act quickly with this ransomware, because after seven days, the demand for money doubles.
However, it is crucial to remove the Cerber virus before decrypting the files.
You can proceed either manually or with anti-virus software.
Also, if you have a backup of your files, you can perform a full system restore.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
Decrypt files corrupted by Spora Ransomware
Spora Ransomware falls into the cryptovirus category, and when it came out in 2017, it was referred to as the most powerful ransomware of all time.
This virus uses the usual social engineering strategies to lure the user into the trap.
These are phishing emails containing copies of seemingly essential documents, such as bills or medical results.
However, as always happens, these documents are viruses that, once triggered, download a JavaScript object into the Windows Temp folder.
After a while, the user sees a Word file appear on the desktop warning of the infection.
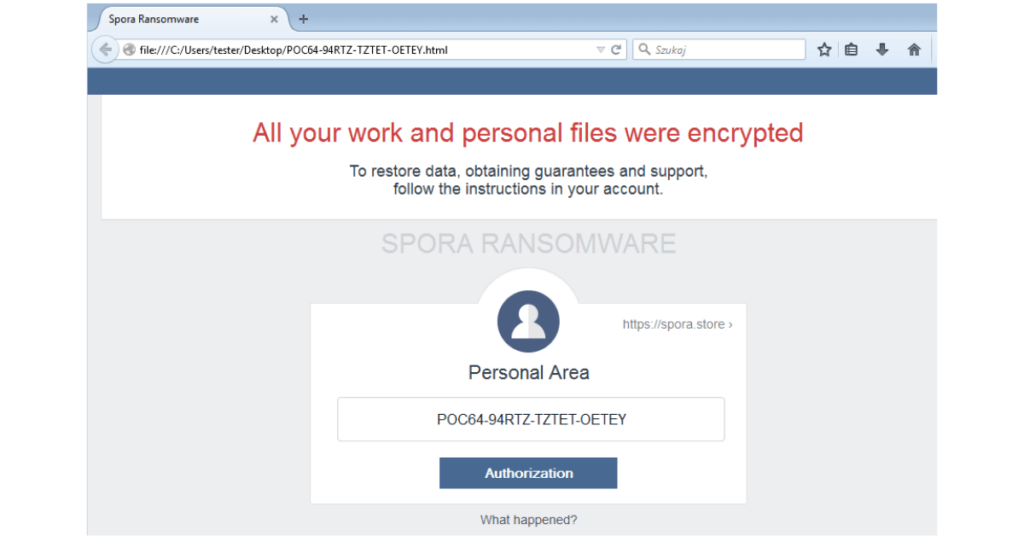
The virus could also distribute the payload through social media or file-sharing sites.
Furthermore, Spora Ransomware may infiltrate the PC’s registry as well, and by doing so will start every time the operating system is restarted.
For these two reasons, if you notice the infection, immediately disconnect your PC from the network to prevent it from spreading.
At the same time, avoid turning off your computer to prevent the virus from performing other functions.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
Decrypt files from Nasoh Ransomware virus
Nasoh Ransomware belongs to the STOP / DJVU family.
Like all other Ransomwares, even Nasoh, once executed, can block access to files on a device’s disks.
As soon as the encryption is completed successfully, Nasoh generates a “readme.txt” file that contains the ransom payment instructions and places it in all folders that contain the modified files.
Nasoh compromises data using an encryption algorithm that generates a unique decryption key for each victim.
The cost of each key is $ 980; however, victims are offered a 50% discount if they contact the developers within 72 hours of encryption.
Hackers also offer to send a decrypted file as proof of restoring data.
It’s just another way to entice victims to pay the ransom.
Some procedures on the net would allow you to decrypt Nasoh Ransomware files, but even in this case, the effectiveness is not guaranteed.
Such procedures suggest restarting your PC in Safe Mode with Networking and installing a reputable anti-malware immediately after that.
At this point, a full system scan will be required to remove the infection.
To recover the data, however, you have three possibilities:
- Volume Shadow Copies if you have a backup on your device;
- Third-party software, such as that developed by NoMoreRansom;
- Use data recovery tools.
As already mentioned, these are not easy tools to handle for those who do not have the proper knowledge in the sector.
Decrypt Hermes Ransomware files
Hermes is a Ransomware-type malware discovered by Michael Gillespie.
Once infiltrated, Hermes encrypts files using RSA-2048 encryption.
This malware does not add extensions to encrypted files, making it more challenging to identify.
After encryption, it creates an HTML file containing the ransom message “DECRYPT_INFORMATION.html” and places it in each folder containing the encrypted files.
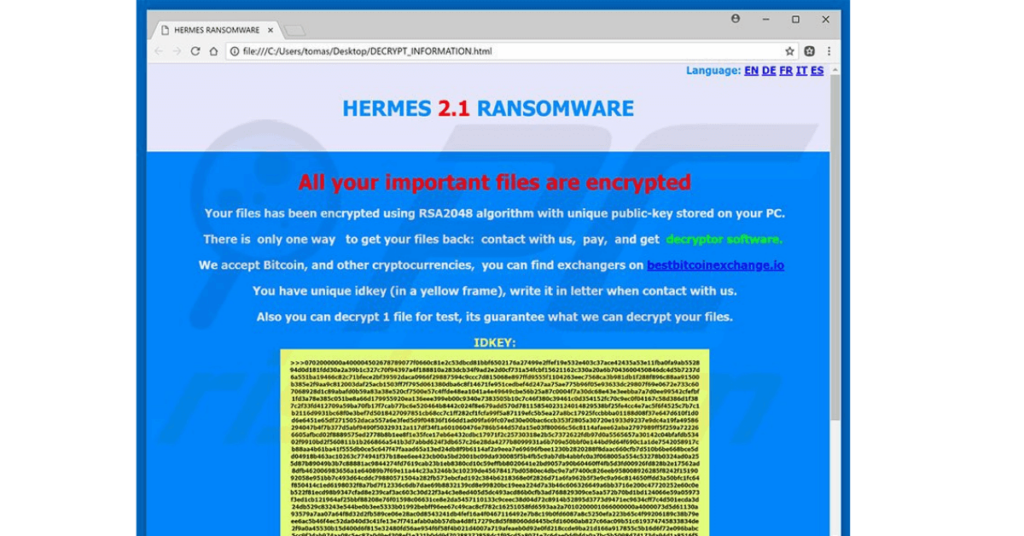
In addition, it provides a UNIQUE_ID_DO_NOT_REMOVE file, which users are invited to add to the email when communicating with the cybercriminals responsible for the attack.
The message informs the victims that they need to purchase decryption software to recover the damaged files.
With the RSA-2048 asymmetric encryption algorithm, Hermes Ransomware generates public (encryption) and private (decryption) keys.
It is impossible to restore encrypted files without a private key.
Manual elimination of threats and subsequent decryption could prove to be a long and complex process requiring advanced computer skills.
Decrypt GandCrab Ransomware files
GandCrab is the most active ransomware family.
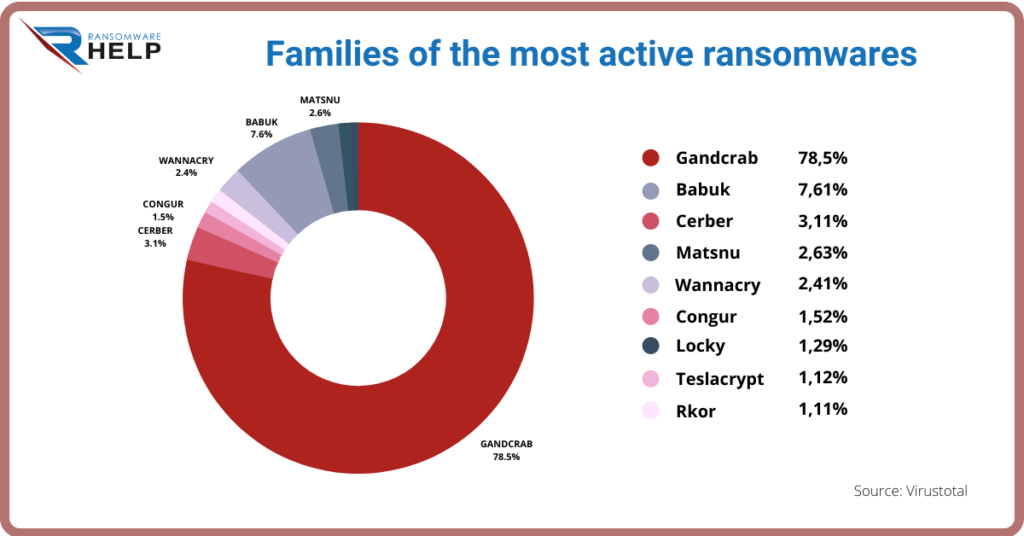
As can be seen in this graph that reports Virtustotal research data, GandCrab ransomware is part of the most active family with 78.5%.
In second place is Babuk, trailing at only 7.61%.
It is particularly dangerous ransomware because, in the beginning, its creators threatened to make the victims’ private and personal information public.
The ransom was requested by threatening the user by telling him that the webcam had been violated.
If the victim did not pay the ransom, the hackers would have made compromising images and videos public.
What makes Ransomware such a revolutionary phenomenon in cybercrime is that there cannot be a single cure for all infections.
The situation is different from other viruses, which can generally be eliminated with an anti-virus.
After first appearing in 2018, GandCrab ransomware continued to be developed in different versions.
Each new variant has an improved encryption mechanism and is more challenging to decrypt.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
How to restore files encrypted by Ransomware?
Several tools allow you to restore files encrypted by Ransomware on the net.
Once again, however, it should be emphasized that all the solutions we talked about previously are not a guarantee of any result; indeed, they often prove to be ineffective, especially for the inexperienced user.
What can be done is to focus on prevention rather than cure.
There is a lot more to talk about how to protect yourself from ransomware, which is what would make a difference in tackling the problem:
- Constantly update your operating system and your anti-virus.
This is a vital step in detecting certain types of ransomware and preventing your files from being encrypted;
- Avoid phishing scams.
Pay close attention to the details that identify the senders of your emails and do not open them if they contain suspicious elements;
- Make periodic backups of all your data.
This way, even in an attack, you can recover your files.
In addition to physical media, it also exploits the potential of cloud storage, which is more secure;
- Follow a zero-trust or minimum privilege model.
A model with minimum privileges limits access only to what is necessary;
- Monitor file activity and user behavior to detect, alert and respond to potential ransomware activity.
If you should still fall into the trap of a ransomware despite all these recommendations, the advice is not to proceed with do-it-yourself solutions.
Contact a specialized company such as HelpRansomware.
A team of experts has developed methodologies that apply to each ransomware attack, shortening the resolution time and, consequently, the company’s downtime.
How is Ransomware detected?
Ransomware is an insidious virus, mainly because it runs in the background without causing slowdowns or anything else, unlike other cybercrimes.
For this reason, it is pretty tricky for the user to notice the infection in time.
One way to realize that you have been attacked is to notice how the files on your device are named.
As seen so far, almost all ransomwares rename files on the PC by adding an extension often corresponding to the name of the virus itself.
On the other hand, the ransomware could be detected by a good anti-virus.
A tip that you must absolutely follow is downloading a certified anti-virus that covers the users and that protects you effectively.Finally, the virus in question can manifest itself when it is already too late for any action or with the window’s appearance with the ransom demand.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
What is Ransomware ID?
The Ransomware ID is the identification code of the virus that attacked your device.
The homonymous website that assists in the fight against malware capable of encrypting files comes from this name.
ID Ransomware to date recognizes 1055 different ransomware in a list that is constantly updated.
Just upload one of the encrypted files to check the availability of a decryption tool.
If the file is infected with one of the viruses present in the system database, ID Ransomware will direct you directly to the decryption tool.
How to decrypt Cryptolocker files?
The new CryptoLocker variants are powerful enough to evade anti-virus and firewall technologies.
Precisely for this reason, it is essential to protect yourself in the right way by strengthening access controls to all devices.
Upon execution, CryptoLocker scans the network drive to which the host is connected to search for documents and any other type of file to name and encrypt.
This ransomware uses a 2048-bit RSA encryption key and an extension, such as .encrypted or .cryptolocker or .[7 random characters], depending on the variant.
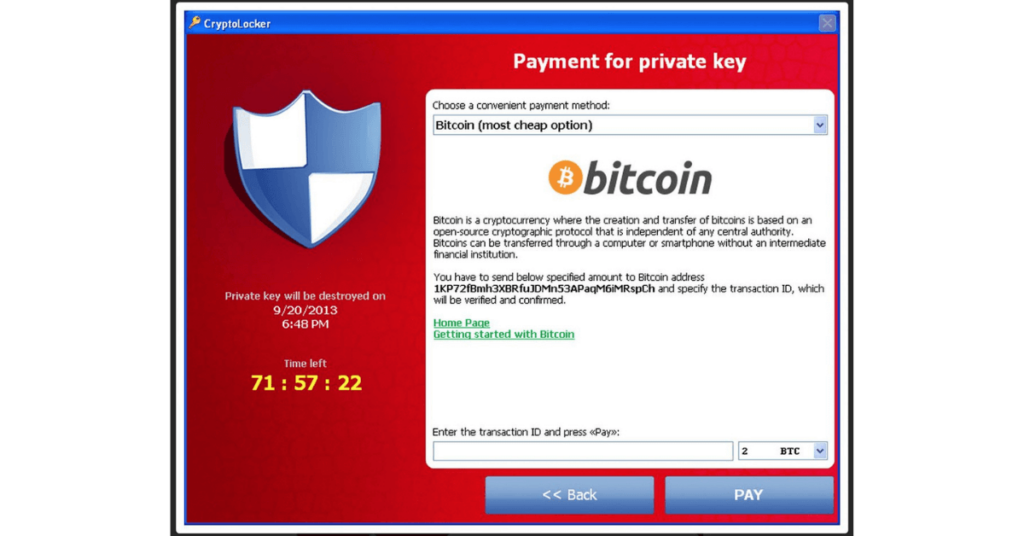
Finally, the malware creates a file in each folder and places the decryption instructions that require payment in bitcoins.
To remove Cryptolocker files, you can find several free solutions, but the paid ones are often more effective.
However, this software all behaves more or less the same way, so once installed and started, they proceed with downloading the anti-malware definitions.
Once this phase is finished, it will be possible to start the scan by indicating to the program which disk drives to act on and decrypt files infected by Ransomware.
Once the process is finished, you will remove the malware.
If the software does not restore the files, the advice is to restart the computer in safe mode and repeat the procedure.
How to recover files damaged by Cryptolocker?
If suddenly all the files on your computer become unreadable and their extension changes to “.encrypted”, it means that the Cryptolocker virus has started its action.
To prevent them from proceeding with damage to your device, follow these guidelines:
- Disconnect the PC from the internet; in this way, you will avoid spreading the infection;
- Run anti-virus software on your PC to identify all infected files;
- Restore original files;
- If you are not successful in restoring the files, proceed with restoring the system.
You must know that, with this last step, your device will return to the latest backup version.
Or, if you don’t have any backups saved, your PC will be restored to its factory version.
Differences between Ransomware and Cryptolocker
Within the Ransomware category, we can distinguish two different types of cyber threats:
- Ransomware locker: the virus uses full-screen images or web pages to block access to the computer.
The device’s primary functions are disabled, and the PC is unusable.
This type of virus, however, tends not to destroy the data on the device; its goal is only to block them;
- Crypto-ransomware: the virus locks your computer files, encrypts them with passwords, and makes them impossible to open.
- Unlike the previous one, this virus encrypts files on the device, but the PC remains usable.
Crypto-ransomware can have a devastating effect, making it impossible to access documents and files of all kinds.
Either way, the hackers require a ransom payment to send the decryption key.
CryptoLocker falls into the second category and is a malware that mainly infects Windows operating systems.
Conclusions
By now, you will have realized that decrypting Ransomware files is very complicated.
From this guide, you were able to draw the following conclusions:
- Decrypting ransomware files means cracking a file that has been attacked and made inaccessible by a malware;
- In the first six months of 2021, payment requests for ransomware reached $ 590 million;
- Ransomware encryption makes it impossible to access files unless you have a decryption key that can be obtained by paying a ransom;
- About 92% of the companies that produced the ransom did not receive the decrypted files;
- GandCrab is part of the most active ransomware family;
- Within the Ransomware category, we can distinguish two types of cyber threats, lockers, and crypto-ransomware.
The world of ransomware is constantly updated, and it is not recommended to remove them with do-it-yourself solutions.
Contact HelpRansomware for specialized advice with professionals in removing and recovering data encrypted by ransomware.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.



