Learn about Buhti ransomware and how to protect yourself from becoming a victim. Learn steps to prevent and effectively respond to a ransomware attack.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
What is Buhti ransomware?
Buhti ransomware is an advanced form of malware that has the ability to encrypt your files, making them inaccessible.
Once your data is encrypted, the attackers demand a ransom, often in cryptocurrency, for the decryption key.
This new variant was identified in February 2023 by Unit 42, which informed users via its Twitter profile.
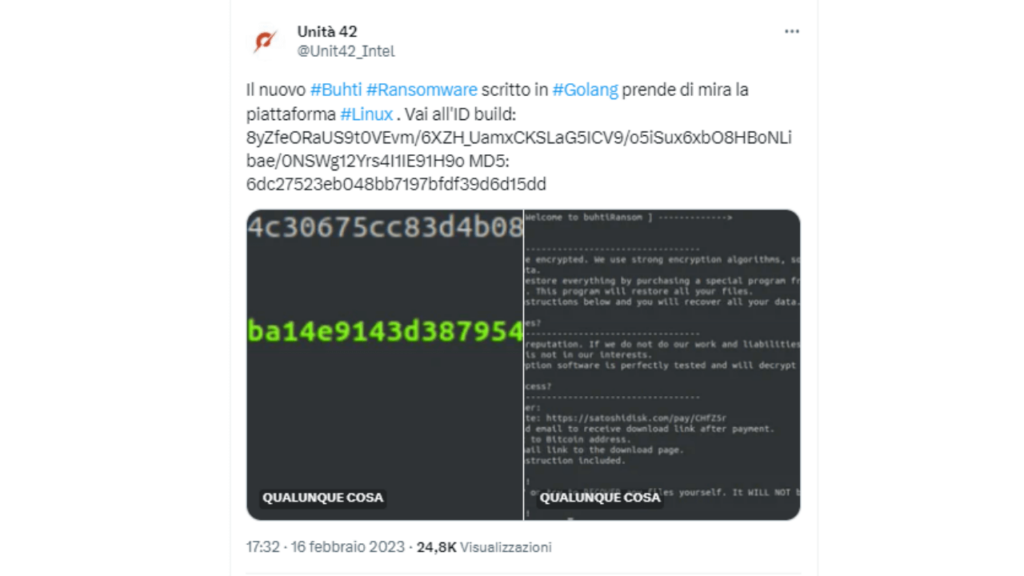
As you can read, this type of ransomware prefers attacks against the Linux and Windows operating systems.
Moreover, experts have presented the Buhti ransomware as a particularly insidious form of malicious software, as it poses a serious threat to companies, professionals and individuals.
Once opened, the ransomware activates by encrypting files and rendering them unusable.
How does it work?
As written in the HivePro report, the Blacktail group responsible for the ransomware demonstrates a quick response to exploit vulnerabilities.
Their attacks specifically targeted a recently discovered vulnerability in PaperCut NG and MF (CVE-2023-27350).
This ransomware is unique in three ways:
- Instead of developing its own malicious payload, Buhti chose to use variants of the leaked LockBit and Babuk ransomware families to target both Windows and Linux systems;
- Buhti created a custom data exfiltration tool coded in Golang;
- Hackers run ransomware remotely and use exploits to steal data and distribute the payload to computers on the same network.
Many antivirus and firewall software have difficulty detecting it because of its ability to disguise itself as a legitimate application or use rootkit techniques to hide in the operating system.
This makes it extremely difficult to detect and remove, increasing the risk and potential consequences of infection.
Often, the victim does not realize they have been attacked until the ransom demand appears on their screen, which looks like the image below.
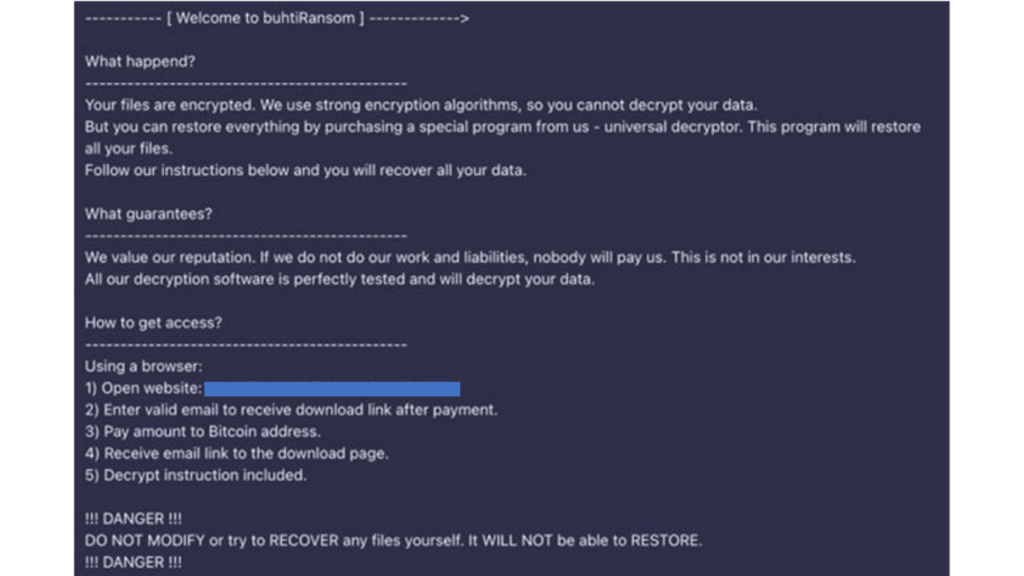
Key features of Buhti ransomware
Buhti ransomware is known for a number of characteristics that make it a particularly fearsome adversary in the cybercrime landscape, such as:
- Advanced encryption: its algorithms are designed to be resistant to decryption efforts, making it nearly impossible for victims to access their data without the specific key provided by the attackers;
- Cryptocurrency payment: this payment method provides a level of anonymity that makes it extremely difficult for authorities to trace attackers;
- Security evasion: Buhti uses masquerading and rootkit techniques to hide in the operating system, making it difficult for antivirus software to detect.
This means that even if you have the latest anti ransomware, there is a chance that Buhti could slip through the net;
- Speed of action: Buhti executes a rapid, automated attack that can cripple an entire organization in minutes, leaving no time to respond.
As noted in the Sophos report, in the first half of 2023, the average dwell time for ransomware incidents dropped dramatically from 9 days to 5 days;

- Selective targeting: while many ransomware take a blanket approach, Buhti is known to pick and choose its targets, focusing its efforts on companies or individuals that are more likely to pay the ransom.
For all of these reasons, if you suspect or experience a Buhti ransomware attack, it is important to act quickly and contact a specialized company like HelpRansomware for an immediate assessment and action plan.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
Consequences of Buhti ransomware
The consequences of a Buhti ransomware attack go far beyond simply losing access to data.
Here are some of the more serious consequences:
- Operational disruption: from accessing customer databases to managing human resources and finances, the loss of critical data can cripple a business;
- Reputational damage: ransomware attacks can lead to a loss of trust among customers and business partners, which can have a long-term impact on a corporate reputation;
- Financial costs: in addition to the ransom demanded, which can run into the thousands of dollars, there are costs associated with recovering from the attack and the loss of business during the downtime.
Consider that, according to IBM, the average cost of a data breach in 2022 was $4.35 million;

- Legal implications: data protection laws, such as the GDPR in the European Union, impose severe penalties for data breaches, which can add another layer of cost and complexity to recovering from an attack;
- Emotional and psychological impact: the anxiety and stress associated with having one’s privacy breached through attacks such as doxing and the loss of critical data can have long-term mental health implications;
- Risk of future attacks: Paying the ransom not only does not guarantee data recovery, but may also make you an easy target for future attacks.
Given the severity of these consequences, it is crucial to take every precaution to prevent an attack and have a plan of action in case one occurs.
Consulting with a specialized company like HelpRansomware can provide invaluable assistance in navigating the complex challenges posed by a Buhti ransomware attack.
Why be prepared?
Preparedness isn’t just a preventative measure, it’s an absolute necessity in a digital environment where threats like Buhti ransomware are becoming increasingly prevalent and sophisticated.
In fact, preparation is essential to minimize risk and loss.
It’s not just about installing antivirus software or having a robust firewall; it’s also about training and awareness.
You need to be able to recognize the social engineering tactics used and train yourself and your team to protect yourself from ransomware.
As reported by Thales, only 49% of organizations surveyed have a formal ransomware response plan, while 67% continue to experience data loss after attacks.

Being prepared not only helps you deal with attacks when they happen, but it can also serve as a deterrent to potential attackers.
A well-protected system with robust security measures is less attractive to cybercriminals, who may decide to focus their attention elsewhere.
In conclusion, preparedness is an essential component of risk management in the digital age of constantly evolving threats.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
Key Measures to Prevent the Buhti Ransomware Attack
Prevention is the first line of defense against any form of cyberattack, including ransomware.
Being proactive, rather than reactive, can mean the difference between maintaining data security and managing a crisis.
Here are some key steps every business and individual should consider to mitigate the risk of an attack.
Backup files
Backup your important data regularly and ensure that it is stored in a separate environment that is protected from unauthorized access.
Use both local and cloud backup solutions, and regularly test the recovery process to ensure it works as expected.
It’s also important to regularly test your backups to ensure they can be successfully restored.
As reported by Unitrends, 73% of all ransomware attacks were successful in encrypting files.

Having up-to-date backups means you won’t have to resort to other measures to restore encrypted files.
Update your software
Keeping your software and operating systems up to date is critical for security and ransomware protection.
Developers frequently release security updates that patch vulnerabilities that could be exploited by malware like Buhti.
In addition to security updates, it’s important to keep all business and personal software up to date with the latest versions, which often include performance improvements and new security features.
It is also important to update security patches, which fix known vulnerabilities.
Cybersecurity training
Every team member should be trained to recognize red flags such as suspicious email addresses and unsafe URLs, which are often used in phishing attacks to deliver ransomware.
Investing in cybersecurity training programs for employees can provide a deeper understanding of emerging threats and best practices for mitigating them.
One mistake can compromise the entire network, so it’s important that everyone is aware of the risks.
Strong passwords
Using strong, unique passwords for each service or application is another critical step in preventing ransomware.
Use a combination of letters, numbers and symbols to create strong passwords, and consider using a password manager to keep them safe.
According to Sophos analysis for the first half of 2023, 50% of hacking attacks were carried out thanks to compromised credentials.
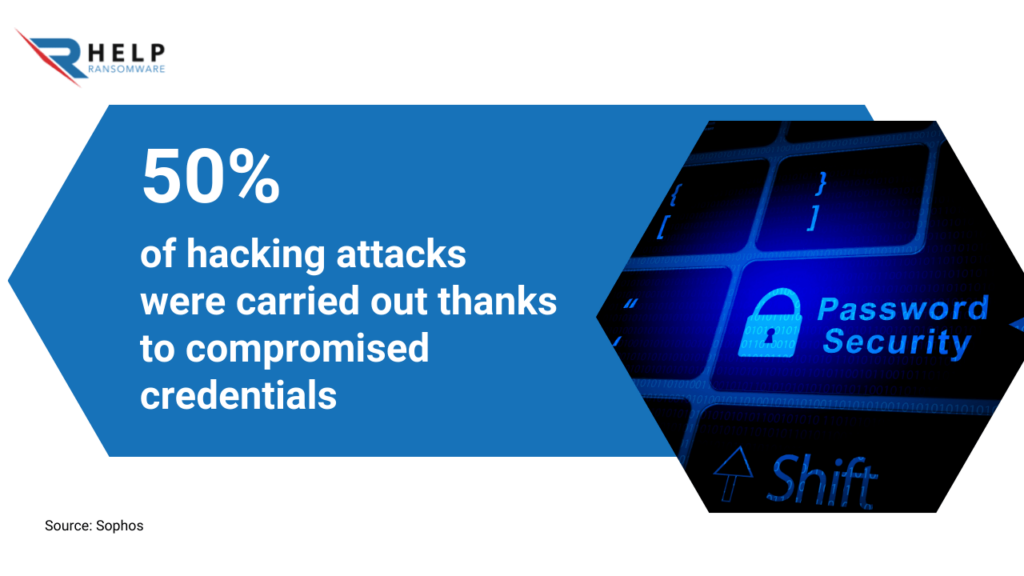
To understand the importance of using strong passwords, consider that only 23% of attacks come from exploiting vulnerabilities.
Also consider using two-factor authentication, which adds an extra layer of security and makes it harder for attackers to gain access to systems.
What should I do if my system is infected with Buhti ransomware?
If your system has been compromised by Buhti ransomware, it’s important to act quickly but thoughtfully to minimize the damage and begin the recovery process.
Follow these steps:
- Isolate the infected system from the network: this step is important to prevent the ransomware from spreading to other devices.
Immediately disconnect the computer from the network and disable Wi-Fi and Bluetooth connections to limit the damage to a single device;
- Notify security experts: contact HelpRansomware for a quick and effective damage assessment and action plan;
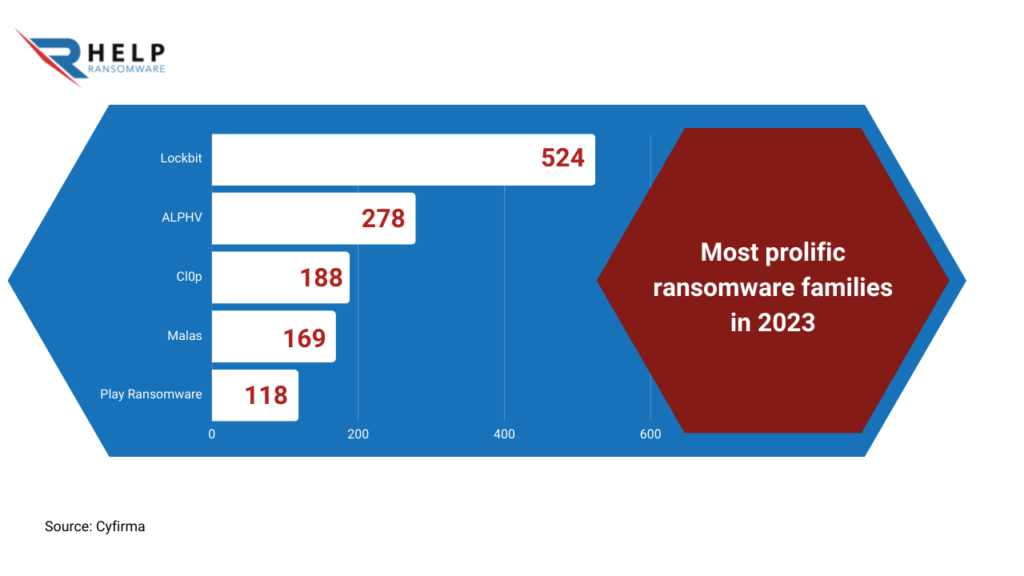
- Identify the type of ransomware: before you can proceed with a data recovery attempt, it is important to identify the specific type of ransomware you are dealing with.
Cyfirma reports that the most prolific ransomware families in 2023 are Lockbit, ALPHV, Cl0p, Malas, and Play ransomware, with Lockbit holding the record with 524 victims;
- Document everything you can about the attack: collect screenshots and at least one example of an encrypted file, but don’t click on any links;
- Communicate with your internal and external team: notify team members, partners, and customers as necessary, following the guidelines of your incident response plan.
Transparency is key to maintaining trust and complying with data breach notification laws.
If, despite your precautions, your system is infected with Buhti ransomware, remember that it is critical to act quickly.
Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
Data recovery steps
Recovering encrypted files is a critical step after a Buhti ransomware attack, and it requires a methodical and well-planned approach.
Here are some specific steps that should be followed to maximize the chances of successful data recovery:
- Initial Assessment: perform a detailed assessment of the health of your data, including identifying files that have been encrypted, corrupted, or deleted;
- Virus Scan: perform a full system virus scan to identify and remove ransomware or its remnants;
- Use data recovery tools: the effectiveness of these tools can vary and should be used as a secondary option if backups are not available;
- Verify data integrity: ensure recovered files are functional and not corrupted;
- Post-recovery security audit: this step is designed to identify any vulnerabilities that may have been exploited during the attack;
- Continuous monitoring: implement a continuous monitoring system to detect any suspicious activity that could indicate a reinfection attempt or other security issues.
Data recovery is a complex process that requires expertise and attention to detail.
For this reason, it is highly recommended to work with experts in the field, such as HelpRansomware, whose services ensure that recovery is performed in the most effective and secure manner.
What to do if you fall victim to Buhti ransomware
If you become a victim of Buhti ransomware, it is important not to pay the ransom, as this does not guarantee the recovery of your data and makes you a target for future attacks.
Instead, report the incident to the relevant authorities and contact a specialized company like HelpRansomware for immediate assistance in removing and decrypting ransomware files.
Once you have a plan of action to deal with the threat, assess the financial and reputational impact of the attack.
In the report published by CrowdStrike, we read that the average interruption time for interactive cybercrime intrusion activity fell to 84 minutes in 2022 (compared to 98 minutes in 2021).

To minimize damage and costs, the IT team should follow the 1-10-60 rule: detect threats in the first minute, understand them in 10 minutes, and respond in 60 minutes.
Then, once the immediate situation is resolved, review and update your security measures to reduce and prevent ransomware attacks.
Finally, although it’s difficult to accept, it’s important to maintain a proactive attitude and use this experience as a learning point.
So, create or update your incident response plan and make sure all teams are educated on cybersecurity best practices.
Recommended tools and software to protect against Buhti ransomware
Protecting against Buhti ransomware is not only a matter of best practices, but also of using the right tools and software.
For optimal protection, consider using high-quality antivirus software.
According to Astra, antivirus software detects over 560,000 pieces of malware every day.

Try to choose one with anti-ransomware features, a robust firewall, and backup software with quick recovery options.
However, no software is 100% effective, so it is important to use a combination of ransomware solutions.
Some security tools also offer real-time monitoring capabilities that can detect and block suspicious activity before it can cause damage.
On the other hand, you can increase the level of security with password management software or tools that support two-factor authentication.
For comprehensive protection, consider an integrated security suite that combines antivirus, firewall, and other security features such as ransomware decryption.
To complete the security system, use a VPN for secure web browsing.
Why is it a threat to your business?
A ransomware attack negatively affects several aspects of a business.
In terms of operational damage, it can be the loss of critical data or the leakage of confidential information.
In the first case, the impact is a technical problem: employees are unable to do their jobs and the business is paralyzed.
In the second case, the legal ramifications are greater and the damage potentially more dangerous, as not only the company’s confidential data is exposed, but also that of its customers and suppliers.
In both cases, however, we see damage to the online reputation and image of the brand it represents.
The company’s credibility is called into question, and at that point, the way the crisis is handled makes all the difference.
In fact, in an increasingly digital world, data security has become an absolute priority for companies of all sizes.
Conclusions
Buhti ransomware is a growing threat that requires attention and preparation.
Here are the conclusions you can draw from this guide:
- Buhti ransomware was identified by Unit 42 in February 2023;
- Instead of developing its own malicious payload, Buhti chose to use variants from the LockBit and Babuk ransomware families;
- In the first half of 2023, the average dwell time for ransomware incidents dropped to 5 days;
- The average cost of a data breach in 2022 was $4.35 million;
- Only 49% of organizations surveyed have a formal ransomware response plan, while 67% continue to experience data loss following attacks;
- 73% of all ransomware attacks were successful in encrypting files;
- In 50% of attacks, hackers completed the process using compromised credentials;
- The average disruption time for interactive cybercrime intrusion activity will decrease to 84 minutes in 2022.
Taking preventative measures and having a plan of action in the event of an attack can mean the difference between a minor inconvenience and a devastating crisis.
If you do find yourself facing an attack, remember that HelpRansomware is here to assist you every step of the way, from ransomware removal to data recovery.




