GlobeImposter 2.0 ransomware is a severe threat to your devices and data. Learn how to protect yourself from this dangerous malware.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
What is GlobeImposter 2.0?
GlobeImposter 2.0 is a ransomware-style file encryption malware.
It is an enhanced version of the original GlobeImposter, first appearing in 2017.
This ransomware infiltrates a computer system, encrypts the user’s files, and demands a ransom to restore them.
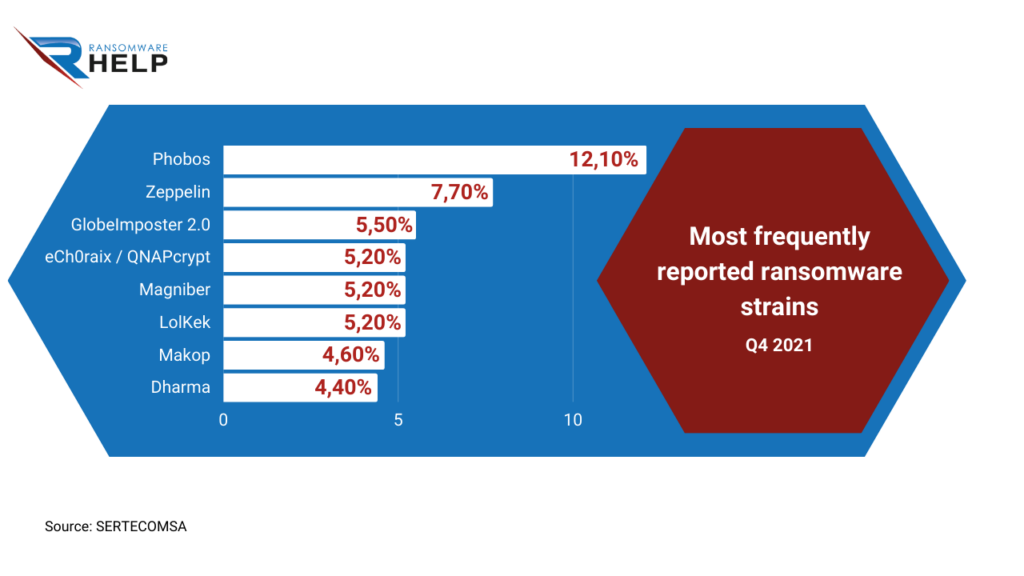
In the fourth quarter of 2021, GlobeImposter 2.0 was the third most reported strain, according to SERTECOMSA, Communications Technical Service, trailing only Phobos and Zeppelin.
Who is it directed at?
GlobeImposter 2.0 main targets are companies and organizations with more financial resources to pay the demanded ransom.
Cybercriminals can exploit system vulnerabilities to obtain confidential information and customer data.
The official website of the state of New Jersey reveals GlobeImposter 2.0’s attack target:
How does GlobeImposter 2.0 work?
This malware combines advanced encryption techniques to ensure the victim’s data remains hijacked until the ransom is paid.
Malwarebytes, anti-malware software, reveals the following symptoms:
‘Ransom.GlobeImposter may run silently in the background during the encryption phase and not provide any indication of infection to the user.’
How does GlobeImposter 2.0 spread?
The cybercriminals behind GlobeImposter 2.0 primarily use phishing emails and compromised websites.
The UK government’s Department for Digital, Culture, Media and Sport (DCMS) indicated that 83% of businesses and 79% of charities reported phishing attacks in 2021.

What are its features?
GlobeImposter 2.0 features are as follows:
- It combines advanced encryption techniques: encryption of individual files, generating unique encryption keys for each victim;
- Data recovery without paying the required ransom is challenging;
- It evades detection using traditional antivirus programs;
- It can infect the victims’ systems without being detected;
- Ability to encrypt any file.
Due to all these characteristics, GlobeImposter 2.0 is a severe threat to companies and institutions.
What are the different types of Globeimposter 2.0 attacks?
One of the most common methods is phishing emails; cybercriminals send fraudulent emails, including malicious links or infected attachments.
Another technique used by GlobeImposter 2.0 is exploiting system or application software vulnerabilities, allowing attackers to gain unauthorized access to the system and deploy malware.
GlobeImposter 2.0 spreads through malicious downloads of infected software or torrent files.
What effects of a successful Globeimposter attack?
Users lose access to their files and receive a ransom request to pay in cryptocurrency in exchange for the decryption key.
When paying the ransom, victims have no guarantee that cybercriminals will return the key to unlock their files.
Furthermore, encryption and decryption can damage files, making them irreparable and unusable, even after the ransom is paid.
A successful GlobeImposter 2.0 attack can have severe financial and emotional consequences, cause critical data loss, and damage corporate reputation.
According to the World Economic Forum report, the average cost of breaches for an organization is $3.6 million.

How to detect a Globeimposter 2.0 infection, and which devices are at risk?
Some indicators are:
- Encrypted files with a “.crypt” or “.oops” extension;
- Ransom messages that demand payment to restore encrypted files;
- Unknown files on your system.
Devices using Windows operating systems are particularly vulnerable to Globeimposter 2.0 attacks.
What should you do if Globeimposter infects your device?
You should not pay the ransom to cybercriminals, as this does not guarantee you recover encrypted files and only encourages hackers to continue their malicious activities.
Instead, you should disconnect your device from the Internet and turn to a cybersecurity expert for assistance or use reliable malware removal software.
Another good practice is to back up vital files on an external device or in a cloud to protect them from future threats.
If you don’t know how to manage a ransomware attack, contact a specialized company like HelpRansomware.
The corporation is a global leader in ransomware removal, cybersecurity, and decryption.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
What are the best strategies to prevent a Globeimposter attack?
Implementing the following key cybersecurity strategies is crucial to prevent ransomware attacks from GlobeImposter or other malware threats:
- Ensure that the security software is always up-to-date and functional;
- Avoid opening suspicious emails or clicking on links, or downloading files from untrustworthy sources;
- Perform regular backups of important files and store them on an external drive or cloud storage;
- Ensure that your operating system and all installed programs are up-to-date with the latest security patches to prevent vulnerabilities;
- Train all users of your network or device about cybersecurity best practices and how to identify potential threats.
By following these strategies, you can significantly reduce the risk of a GlobeImposter attack.
How can you protect yourself from a GlobeImposter attack?
If you want to protect yourself from ransomware, it implies taking preventive measures and being prepared for malware infection.
Installing reliable, up-to-date security software on all your devices is one of the best practices.
Paying attention to signs of a possible attack, such as encrypted files or rescue messages, and taking immediate actions to mitigate the damage is also vital.
Other preventive strategies include using strong and unique passwords for all your accounts and making periodic file backups.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
How to protect your devices from GlobeImposter 2.0?
Taking adequate measures to protect your devices against potential threats is essential.
That is, installing antivirus software, keeping the operating system up to date, using strong passwords with two-factor authentication, avoiding suspicious links or attachments, and backing up data regularly.
Can GlobeImposter 2.0 be decrypted?
There is no definitive solution to decrypt files encrypted by GlobeImposter 2.0, but some tools and techniques can help remove ransomware.
And if you have a recent backup of your files, you can restore them from that copy instead of paying the ransom to cybercriminals.
What should I do when my data has been encrypted by GlobeImposter 2.0 ransomware?
You will need an anti-malware program, such as HitmanPro or Malwarebytes, to recover these files.
This software can remove ransomware but cannot open encrypted files.
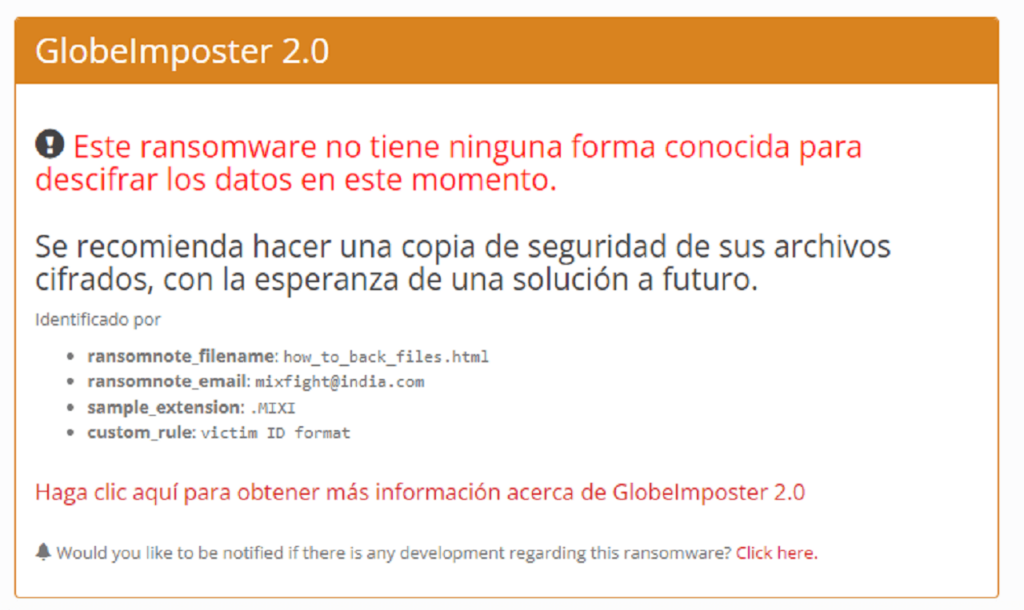
For example, the company ID Ransomware, specializing in ransomware detection, states on its website that GlobeImposter 2.0 cannot decrypt ransomware files.
To do this, contact a company specialized in data removal and decryption, such as HelpRansomware.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
Their team timely assists ransomware victims such as businesses or government corporations.
Will I get my data back if I pay the hackers at GlobeImposter 2.0?
There is no guarantee that GlobeImposter 2.0 hackers will return your data even if you pay the ransom.
Cybercriminals often get the money and don’t provide the decryption key to recover the files.
In addition, paying the ransom encourages ransomware activities and hackers to perpetrate new attacks.
Instead of paying the ransom, it is recommended to take preventive measures to avoid malware infection.
You can restore your files from a recent backup or use decryption tools developed by security researchers that may help in some cases.
Otherwise, contact cybersecurity or data recovery professionals for further assistance.
This is the case of HelpRansomware, a company with over 25 years of experience in cybersecurity.
Its experts are specialized in ransomware removal, cybersecurity, and decryption.
Conclusions
In this article, you have discovered what GlobeImposter 2.0 ransomware is and why it threatens your devices and data. You have also learned how to protect yourself from this malware.
You can draw the following conclusions from this guide:
- GlobeImposter 2.0 is an enhanced version of the original GlobeImposter, first appearing in 2017;
- GlobeImposter 2.0’s primary targets are companies and organizations;
- It mainly spreads through phishing emails and compromised websites;
- Devices using Windows operating systems are particularly vulnerable;
- There is no guarantee that GlobeImposter 2.0 hackers will return the data, even after paying the ransom.
Be aware that you should never pay the ransom to restore files encrypted by ransomware.
Contact a specialized company if you cannot restore your files through backup or removal software.
HelpRansomware is the world’s leading ransomware removal, cybersecurity, and decryption company.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.



