Read the Help Ransomware guide and learn how to prevent a ransomware attack. You will find out how a user can recover from a computer virus.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
Some facts about ransomware
Ransomware attacks are on the rise and have evolved in such a way that their level of danger is increasingly high.
An attack on corporate networks that encrypts sensitive information can cost companies hundreds of thousands or even millions of dollars.
In 2021, 68,5% of companies were victims of ransomware.
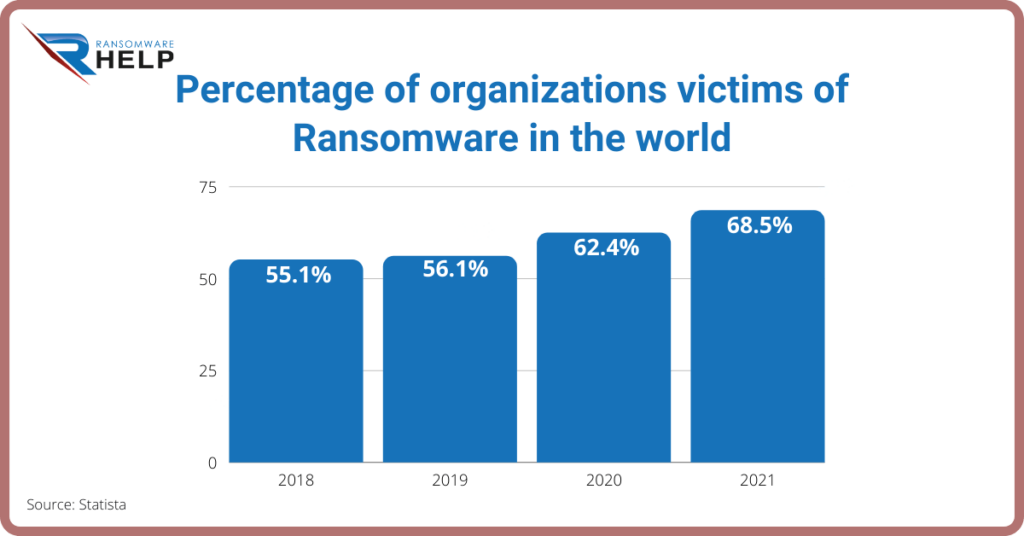
This was an increase from the previous three years and the highest figure reported so far.
More than half of those surveyed stated that their employer had been a victim of ransomware.
Compounding the trend was the pandemic, which forced more and more people to work remotely, and cybercriminals took advantage of the opportunity.
An increase in scams and phishing attempts across all platforms was further evidenced with the arrival of COVID-19.
IDB (Inter-American Development Bank) on its website it states:
“At the aggregated level, the figures are even larger as the economic damage from cyber attacks could exceed 1% of gross domestic product (GDP) in some countries. In the case of attacks on critical infrastructure, this figure could reach up to 6% of GDP”.
Ransomware affects all industries, from technology, insurance, oil and gas, to higher education.
In 2019,over 500 American schools were affected by ransomware.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
Latest malware trends
Ransomware encrypted files continue to pose a major threat to businesses in all industries, but government organizations have undoubtedly been hit the hardest.
It is clear that the pandemic has revolutionized not only our health, but our whole lives: the ways we work, shop or sell, study, etc.
With this increase in online activity, online security risks have also increased, and governments and healthcare organizations have become even more attractive targets.
According to the European Parliament:
“Europe has for years been the target of thousands of serious cyber attacks,
Some of the most serious involving the use of Ryuk malware originating in Russia, which has been in circulation since 2018 and poses a particular threat to institutions that have not updated their lines of defence, as was the case with the Spanish National Employment Service”.
Cybercriminals did not allow themselves to be moved by the urgent need to keep these activities safe, on the contrary, they saw in such organizations the possibility of obtaining maximum economic returns with minimum effort.
This is why beingsufficiently protected and undergoing continuous and frequent backups should be common practice for both large and small organizations.
How does ransomware work?
Ransomware typically spreads through spam or through social engineering attacks.
It can also be spread through websites or drive-by downloads to infect an endpoint and penetrate the network.
The methods of attack are constantly evolving, and there are an incalculable number of ways you can be a victim of a cyberattack.
Once installed, the ransomware locks all files it can access using encryption and, eventually, demands a ransom payment.
To decrypt the files and restore full operations on the affected IT systems, the victims are forced to pay the ransom in Bitcoin.
Ransomware encryptionor cryptoware is by far the most recent variety of ransomware.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
Other types that may be encountered are:
- Unencrypted ransomware: restricts access to files and data, but does not encrypt them.
- Ransomware that encrypts a drive’s Master Boot Record (MBR) or Microsoft’s NTFS: prevents victims’ computers from booting into an active operating environment.
- Leakware: they steal compromising or malicious data that attackers threaten to release if the ransom is not paid.
- Mobile Device Ransomware: Infects mobile phonesvia drive-by downloads or fake apps.
Steps into a typical ransomware attack
Typical steps in a ransomware attack are:
- Infection: after being delivered to the system via an email attachment, the ransomware installs itself on any network device that it can access.
- Secure Key Exchange: the ransomware contacts the control server run by the cybercriminals to generate cryptographic keysto use on the local system.
- Encryption: the ransomware starts encrypting any files it can find on local devices and on the network.
- Extortion: once the encryption work is complete, the ransomware will display instructions for extortion and payment of the ransom, threatening data destruction if the victim fails to pay.
- Unlock: you can pay the ransomand hope that the cybercriminals actually decrypt the affected files.
Or you can attempt recovery by removing infected files and restoring data from clean backups.
Ransomware attacks are one of the biggest threats in technology today, requiring payments through cryptocurrencies to unlock them.
Even in many instances, in addition to being suffering from data theft, victims are also subjected to scams, since for the most part victims do not solve the ransomware problem.
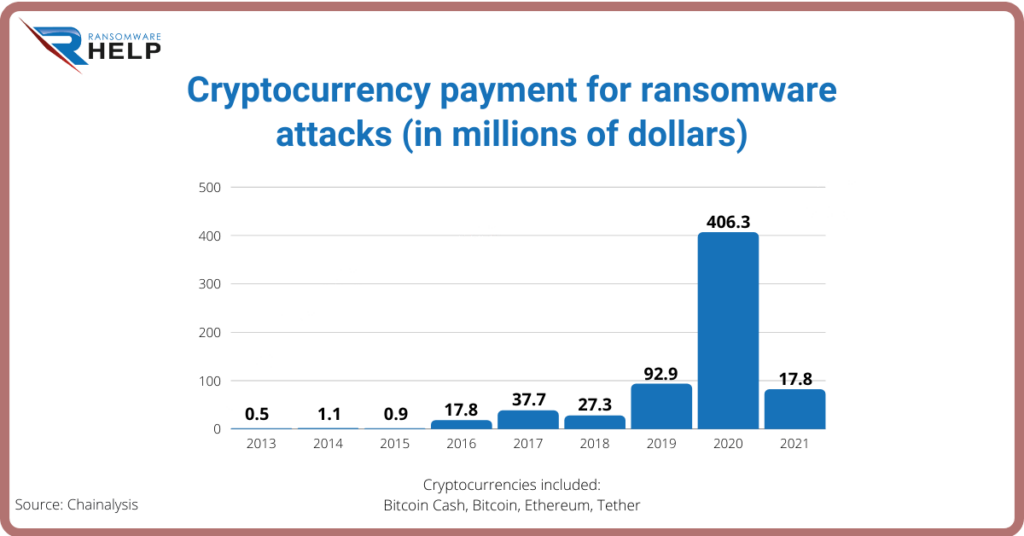
Specifically, ransomware victims paid to attackers more than $406 million in Bitcoin Cash, Bitcoin, Ethereum, and Tethera.
Chainalysis analysts say this number will continue to grow as more ransomware addresses are discovered to receive these payments.
Who is being attacked?
Ransomware attackstarget companies of all sizes (5% or more of the companies that converge in the top 10 industries have been attacked).
No business, large or small, can be considered immune: attacks are increasing in size in every sector.
Furthermore, the recent phishing attempt directed at the Spanish Ministry of Labor shows that attackers have no limits when it comes to choosing their victims.
These attempts, on the other hand, indicate that some organizations, which have weaker controls, must take special care to protect themselves and their data.
Windows computers are the prime targets, but there are also strains of ransomware for Macintosh and Linux.
Ransomware has become a crucial enemy as most companies already know that they will be the victim of a ransomware or malware attack.
Emails and visits to malicious websites have been connected to viruses, but other methods have recently become even more common.
The weaknesses of Microsoft Server Message Block (SMB) and Remote Desktop Protocol (RDP) have allowed the spread of viruses.
Desktop applications and even Microsoft Office (Microsoft’s Dynamic Data Exchange – DDE -) were also the agents of the infection.
Recent strains of ransomware such as Petya, CryptoLocker, and WannaCry have incorporated worms to spread across networks, earning them the nickname “cryptoworms”.
For this reason, it is best to be prepared and understand the need for professionals like HelpRansomware, who recover your files safely, quickly and professionally.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
How to defeat ransomware
We hear constantly about ransomware, but not so much about solutions, so we have the big question: what should you do?
- Isolate the infection: prevent the spread of infection by separating all infected computers from each other, shared storage, and the network.
- Identify Infection: from messages, computer tests and identification tools, determine which strain of malware you are dealing with.
- Report: report the incident to the authorities so that they can act to counter the attack.
- Determine Your Options: you have several ways to deal with the infection, the most important thing is undoubtedly to count on professionals like HelpRansomware.
- Restore and Update: use secure backups and sources of programs and software to restore your computer or equip a new platform.
- Plan a strategy to prevent recurrence: Understand how the infection occurred and what you can do to put measures in place to prevent it from recurring.
Isolate the infection
Speed and readiness in detecting ransomware are critical to fighting attacks before they can spread across networks and encrypt vital data.
The first thing to do when you suspect a computer is infected is to isolate it from other computers and storage devices.
Disconnect it from the network (both wired and Wi-Fi) and any external storage devices.
Cryptoworms actively search for connections and other computers, so it’s best to prevent this from happening.
Furthermore, this will prevent the ransomware from communicating over the network with its command and control center.
Note that there may be more than one patient zero, which means that the ransomware may have entered your organization or home via multiple computers, or it may be inactive and not yet visible on some systems.
Apply these measures on all connected and networked computers to make sure all systems are not infected.
Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
Identify the infection
Very often the ransomware manifests itself when it demands the ransom.
Identifying ransomware will help you understand what type of ransomware you have, how it propagates, what file types it encrypts, and perhaps what your options for removal and disinfection are.
It will also allow you to report the attack to the authorities, which is recommended.
There are countless free tools that can help you, however, we advise you to have professionals who can provide you with an immediate and effective solution.
HelpRansomware has more than 20 years of experience, with laboratories in 14 countries and a worldwide service 24 hours a day, seven days a week.
If you are a victim of ransomware, don’t hesitate to contact HelpRansomware.
Complaint to the authorities
Informing the authorities is a very important step to prevent more people from falling into the trap.
Reporting provides law enforcement with the ability to gain a deeper understanding of the threat and enables them to acquire pertinent information on ongoing ransomware cases.
Knowing more about the victims and their experiences with ransomware will help law enforcement determine who is behind the attacks and how criminals are identifying or targeting victims.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
Determine your options
Your options when infected with ransomware are:
- Pay the ransom (not recommended);
- Try to remove the malware with different antivirus;
- Clean up systems and reinstall them from scratch.
You should discard the option to pay the ransom as the payment encourages criminals.
Not to mention that they cannot restore files encrypted by ransomware, since their goal is often just to get the money.
You are left with the other two options: remove the malware and selectively restore the system or wipe everything and install from scratch.
Let’s see what they both entail below.
Reset or start over
You can choose to try removing ransomware from windows or cleaning your systems and reinstalling it from secure backups and sources of clean operating systems and applications.
No more ransom, is a free option that is in the hands of Europol and other collaborators, to avoid spreading scams.
It all depends on the type of ransomware to be treated, we advise you once again to have professionals like HelpRansomware.
The surest way to be sure that malware or ransomware has been removed from a system is to completely wipe out all storage devices and reinstall everything from scratch.
Formatting the hard drives in the system will ensure that no malware remains.
You should have copies of all your important documents, media, and files.
Make sure you determine the date of the infection as best you can from the dates of the malware files, messages, and other information you have discovered.
System restores aren’t the best strategy for dealing with ransomware and malware.
Since malicious software is typically buried all over your system, you cannot rely on “Restore System” being able to eradicate all parts of the malware.
Also, “Restore System” does not save old copies of your personal files so it won’t delete or replace any of them.
Simply put, don’t count on “Restore System” because it works as a backup.
If your backup solution is local and connected to a computer that is affected by ransomware, your backups are likely to be encrypted along with the rest of your data.
With a good isolated backup solution from local computers, you can easily get the files you need to get your system working again.
How to prevent a ransomware attack

A ransomware attack can be devastating for an individual or a company.
Valuable and irreplaceable files can be irretrievably lost.
It can take tens or even hundreds of hours of work to get rid of the infection and get your systems working again.
Ransomware attacks continue to evolve and attack methods become more and more sophisticated.
Try not to be part of the statistics and have a good plan and smart practices.
To be prepared, you need to know the possible attack vectors – that is, the ways ransomware can enter your system.
Attack vectors can be divided into two types: human attack vectors and robotic attack vectors.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
Human Attack Vectors
Viruses often need the help of humans to break into computers, so they employ what’s known as social engineering.
The CISA explains it as follows:
“In a social engineering attack, an attacker uses human interaction (social skills) to obtain or compromise information about an organization or its computer systems”.
Social engineering consists of using deception to manipulate people into disclosing confidential or personal information that can be used for fraudulent purposes.
In other words, you are being tricked into giving up relevant information that you would otherwise never disclose.
Common human attack vectors include:
- Phishing: uses fake emails to trick you into clicking on a link or opening an attachment containing a malware payload.
Attackers take the time to research individual targets and companies so that their email appears legitimate.
- SMSishing: uses text messages to trick recipients into browsing a site or entering personal information on their device.
Common approaches use authentication messages or messages that appear to come from a financial or other service provider.
- Vishing: the procedure is similar to that used for email and SMS, with the only difference that vishing uses voicemail to deceive the victim.
Cybercriminals can appear professional and use sound effects and other means to appear legitimate.
Like spear phishing, vishing can be tailored to an individual or business as it uses information gathered from cybercriminals.
- Social media: social media can be a powerful vehicle for convincing a victim to open an image downloaded from a site or take some other compromising action.
- Instant Messaging: instant messaging clients can be hacked by cybercriminals and used to distribute malware to the victim’s contact list.
This technique was one of the methods used to distribute Locky ransomware to unsuspecting recipients.
Robotic Attack Vectors
The other type of attack vector is machine-to-machine.
Humans are only involved to a certain extent, as they could facilitate the attack by visiting a website or using a computer.
But the attack process is automated and does not require any explicit human cooperation to invade the computer or network.
- Drive-by: it has this name in reference to the fact that the only thing that is needed for the system to become infected is to open a Web page with malicious code.
- System vulnerabilities: cybercriminals look for vulnerabilities of specific systems and exploit those vulnerabilities to break in and install ransomware on the machine.
This happens very often for those systems that have not been updated with the latest security releases.
- Malvertising: works like a drive-by, but uses advertisements to distribute malware.
These ads could be placed on search engines or popular social media sites to reach a large audience.
A common host for malvertising is adult-only sites.
- Network propagation: once ransomware enters a system,it can scan accessible files and computer shares and spread across the shared network or system.
Businesses without adequate protection may also have infected the corporate file server and other network shares.
From there, the malware will spread as far as possible until it runs out of accessible systems or encounters security barriers.
- Propagation via shared services: online services such as file sharing or synchronization services can be used to propagate ransomware.
If the ransomware ends up in a shared folder on a home computer, the virus can be transferred to other connected machines.
If the service is set to automatically sync when files are added or changed, a malicious virus can be widely spread in milliseconds.
It’s important to pay attention and consider the settings you use for systems that automatically sync.
Best practices for defeating ransomware
HelpRansomware, security expert suggest several precautionary measures to prevent a ransomware attack:
- Use antivirus and antimalware software or other security policies to block known payloads from starting.
- Make frequent and full backups of all important files and isolate them from local and open networks.
- Keep backups of stored data offline, in locations inaccessible to any potentially infected computer.
- Install the latest security updates released by the software vendors of your operating system and applications.
- Consider implementing security software to protect endpoints, email servers, and network systems from infection.
- Practice cyber cleansing, such as being careful when opening email attachments and links.
- Segment networks to keep critical computers isolatedand to prevent the spread of malware in the event of an attack.
- Disable admin rights for users who don’t require them.
- Restrict write permissions on file servers as much as possible.
Conclusions
Ransomware is a form of malware that encrypts a victim’s files. Therefore, from the text we can conclude that:
- Ransomware is generally spread via spam, phishing emails, or through social engineering efforts;
- The most common steps of ransomware are: infection, key exchange, encryption, extortion, unlocking;
- Ransomware attacks target companies of all sizes;
- To combat ransomware, consider isolating the infection, identifying it, creating backup copies, and reporting it to the authorities;
- The most important thing is, without a doubt, to have professionals like HelpRansomware.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.