Read the new HelpRansomware guide and you will learn how to restore files encrypted by ransomware and how a specialist can help you [GUIDE 2022].

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
You are the victim of a ransomware attack
Being the victim of a ransomware attack is worrisome. On many occasions, it can affect your business. And this makes it impossible to operate due to encrypted or blocked files.
Suppose you start work and notice suspicious alerts from your servers, and none of the databases are working.
Your co-workers are frantic and can’t access any of their data.
If you investigate and find that all the files on your network have been renamed.
You find ransom demands and a screen asking you to send an email to a given address if you want your data back.
You will immediately realize that you are the victim of a ransomware attack.
The European Union Agency for Cybersecurity (ENISA) defines ransomware as follows:
“Ransomware depicts a type of malware (like Viruses, Trojans, etc.) that infect the computer systems of users and manipulates the infected system in a way that the victim can not (partially or fully) use it, and the data stored on it. The victim usually shortly after receives a blackmail note by pop-up, pressing the victim to pay a ransom (hence the name) to regain full access to system and files”.
Three common ways your files get encrypted or locked
Ransomware is successful when companies have poor security care.
Organizations that lack data security policies and procedures will have an increased risk of ransomware attacks.
Here are some of the most common ways to fall victim to a ransomware attack.
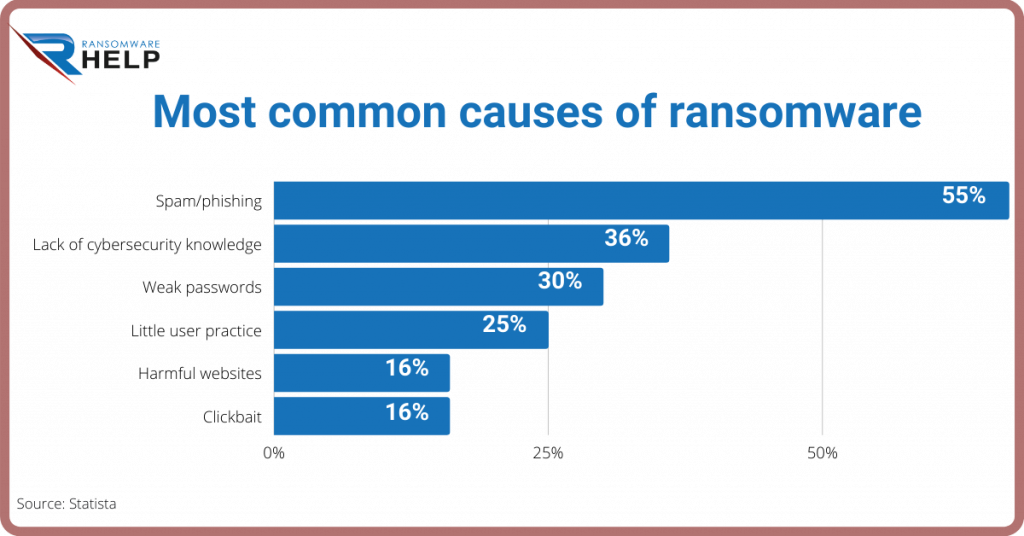
Phishing or electronic spam is the most common, with 55%.
Followed by Lack of cybersecurity knowledge (36%) and the weak passwords (30%).
Aware of the problem with passwords, the Cybersecurity & Infrastructure Security Agency has developed a guide for users to learn how to choose and protect them.
Open Remote Desktop Protocol Ports (RDP)
Companies that have erroneously configured network security can leave the Remote Desktop Protocol (RDP) ports open.
Basically, the user gives cybercriminals the chance to infiltrate with little deterrence.
Once a hacker connects to your network, they can install other Ransomware and backdoors to access your network at a later time.
Many ransomware attacks still use this attack method because so many organizations are unaware of this security vulnerability.
Therefore, you must close the RDP port on your endpoints and servers before it’s too late.
Phishing attacks
Ransomware can infiltrate the network by spreading malicious email known as a phishing attack.
Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
Ransomware operators use vast networks of internet-connected devices (botnets) to send phishing emails to unsuspecting victims.
These emails are intended to trick the recipient into clicking on a malicious attachment or link, installing the ransomware virus or other malware.
Phishing emails are becoming increasingly difficult to detect as cybercriminals rely on social engineering.
They find clever ways to make a malicious email appear legitimate.
It is important to invest in security and awareness training for all organization members, not just the IT department.
Compromised passwords
Ransomware operators may use passwords previously used by employees in your organization to gain unauthorized access to networks.
This stems from poor security practices that involve reusing the same passwords for multiple accounts and authentication processes.
If your employees used outdated and weak passwords to access corporate data, a cybercriminal can use a password to initiate the attack.
Remember to always follow a good password cleaning.
Four options for Ransomware Recovery
The variety of attack vectors underscores the importance of a digital forensic investigation that helps victims.
In this way, they will understand how the ransomware got onto the computer and what steps they can take to remedy the vulnerability.
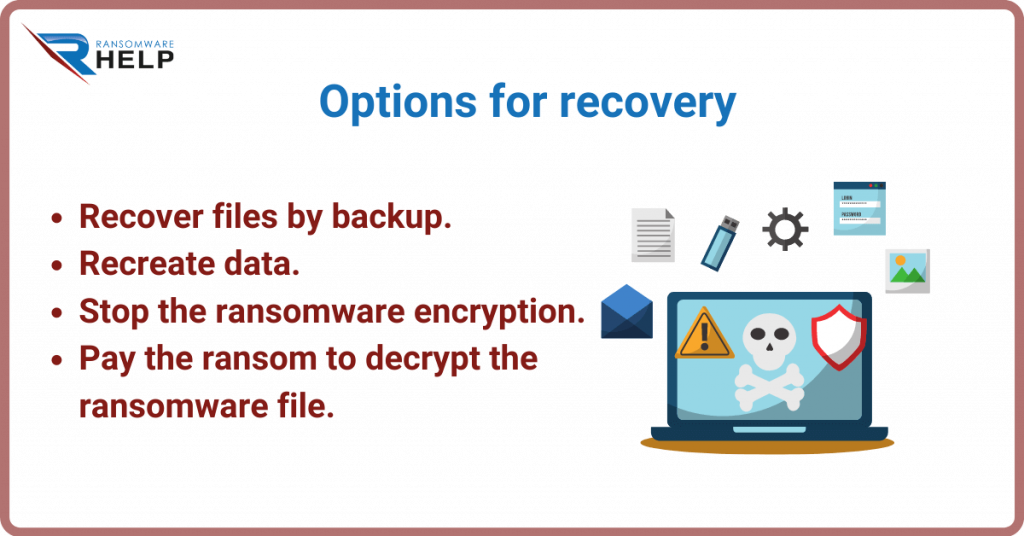
Retrieve files with a backup
If your files are encrypted in a ransomware attack, check (in the following order) if you have backups to restore and recover.
- Off-site or offline backup. having the backup stored in the cloud or offline would protect the data from the virus as it would not be accessible at the time of the attack;
- Check your Windows shadow copies. while most ransomware will delete Windows shadow copies, you may be lucky and find them intact;
- Check your backups on site. Oftentimes, most of the data on site is manually deleted by the attacker or encrypted by the ransomware virus.
Recreate the data
Even if your files have been encrypted by ransomware, you may be able to restore encrypted files from a variety of sources as described below:
- Recreate data from hard copies: this system is almost infallible. When you have physical copies of your data, you can manually reenter the data from hard copies on your computers and servers;
- Gather data from email: email exchanges are a great way to save some data from mail attachments;
- Database mining: some ransomware variants encrypt only a small portion of a database or backup file so that valid and usable data can be extracted.
Stop ransomware encryption
Most ransomware encryption is indestructible, despite the huge technological advances in our society.
The problem is simple: for every solution they find, ransomware creators find dozens of other loopholes they can walk through without getting caught.
Trying to figure out how to stop ransomware encryption is an option that should always be explored.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
While it tends to be rare, there are poorly constructed ransomware ciphers that have been breached by security researchers.
If this can save you from paying a ransom, you should try at all costs.
In fact, there can be flaws in malware or weaknesses in encryption.
Companies need to look into these options, especially if time is on their side.
Another option is to access free ransomware decryption tools.
Pay the ransom to decrypt the ransomware files
If the encryption is too strong, the only way to get the decryption key for your files is to pay the ransom.
Many ransomware victims have no time to waste as they face severe losses due to business interruption.
Here is a list with the most popular variants, with indestructible encryption:

- Sodinokibi;
- Lockcrypt 2.0;
- Mamba;
- Dharma;
- Phobos;
- Netwalker / Mailto;
- Matrix;
- Maze;
- Cryptomix Revenge;
- Globeimposter 2.0;
- NM4;
- Rapid;
- Nozelesn;
- ACCDFISA;
- Mr. Dec;
- Stop;
- Major;
- Snatch.
There are, however, companies and individuals who have the option of choosing not to pay the ransom.
If paying the ransom is the only option, you should understand the pros and cons that it entails before considering moving forward.
HelpRansomware frees you from hackers, to recover encrypted files on different media.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
Why can’t most ransomware encryption be cracked?
Ransomware is a cryptovirus that uses encryption in combination with malware to lock your files.
Modern cryptography uses sophisticated algorithms and secret keys to encrypt and decrypt data.
Encryption is a security tool created to protect data.
Unfortunately, ransomware attackers are using it as a weapon against innocent victims.
How do I know if the encryption can be breached?
You can start with a free ransomware identification resource to determine the feasibility of decryption.
Keep in mind that the tool is not always 100% accurate.
If the variant is still being investigated, it will need a malware or encryption analyst to determine whether or not there is a possibility of decryption.
Encryption is designed to be indestructible, which is why security researchers cannot simply create a tool to crack the type of malware.
In case of being attacked by ransomware, contact HelpRansomware.
The company recovers your data quickly and efficiently, minimizing business downtime.
How can a ransomware recovery specialist help
If you decide to go to a ransomware recovery company, you must ask yourself how they will recover your data.
HelpRansomware provides you with all this information right from the first approach.
Ask the right questions to ensure a transparent experience:
- How to recover my locked/encrypted data?
- How much will the ransomware restore cost?
- Do you have experience with this variant?
A ransomware recovery specialist can analyze your current situation and determine what options are available at the time of the request.
A knowledgeable and experienced ransomware recovery company should be able to provide several services:
- Understand the ransomware variant and explain to the customer what to expect;
- Analyze malware to determine if encryption can be breached;
- Understand what the vector was that caused the attack, and act with preventive methods;
- Modify broken or malfunctioning decryption programs that cause delays in decrypting files;
- Repair damaged databases or files.
Understanding how your files were affected by the ransomware in the first place will give you the information you need to prevent another attack.
Our experts have years of experience and thousands of cases behind them.
They can undoubtedly enable you to make informed decisions about restoring your data after a ransomware attack.
If you need a company with such experience, HelpRansomware is ready to help you 24/7.
Conclusions
A ransomware attack makes it impossible for users and companies to access their files.
Through this guide, you will learn how to restore encrypted files.
The following conclusions can be drawn from this article:
- Ransomware succeeds when companies or individuals neglect security.
- Files are encrypted through RDP, phishing or shared passwords.
- There are manual ways of decrypting ransomware, but it is neither safe nor efficient.
- Ransomware encryption is designed to be indestructible.
The best option to restore encrypted files is to contact an expert team, such as HelpRansomware.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.




