Read this guide about how to remove the CryptoLocker virus from a device. You will learn the instructions, step by step, until its complete elimination [2022].
Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
What is CryptoLocker?
CryptoLocker is a ransomware virus created by cyber criminals.
The virus is distributed using exploit kits, which infiltrate users’ computers using security vulnerabilities found in outdated software.
Some very common ways exploit kits spread are infected emails (phishing), malicious websites, and drive-by (unauthorised) downloads.
Keeping the operating system and all installed programs up to date greatly reduces the risk of ransomware virus infection.
After successful infiltration, CryptoLocker encrypts the files on the infected device and demands the payment of a ransom to unlock the computer and decrypt the files.
Cybercriminals usually order the ransom payment using Ukash, cashU, MoneyPak, or Bitcoin.
Keep in mind that paying this fine is equivalent to sending your money to cyber criminals with no guarantee that your files will be decrypted.
This is why we recommend that you remove the virus and restore your files from a backup.
Files encrypted by this ransomware get the “.encrypted” extension.
Unlike the original Cryptolocker, this ransomware does not remove shadow volume copies of stored files.
Hence, you can use the Windows recovery feature to recover the encrypted files.
Victims of TorrentLocker, on the other hand, can use a tool called “TorrentUnlocker” to decrypt their files.
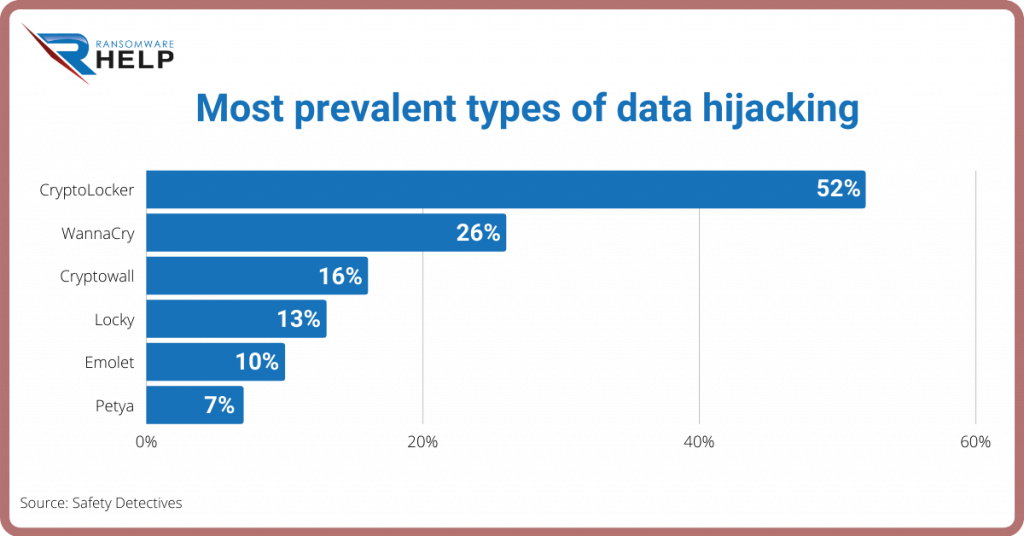
CryptoLocker tops the list of the most prevalent types of data hijacking in 2021.
It is followed by WannaCry, Cryptowall, Locky, Emolet and Petya.
Crypt0L0cker
An updated variant of TorrentLocker is Crypt0L0cker. Cyber criminals spread this ransomware using infected email messages.
PClock ransomware
Another variant of Cryptolocker is called PClock: it requires you to pay a ransom of 1 bitcoin, within 72 hours.
The list of encrypted files is stored in the enc_files.txt file.
The good news is that this ransomware uses weak encryption, and that the company Emsisoft has created a decryption tool for this malware.
Alpha Crypt ransomware
Alpha Crypt is another variant of the original Cryptolocker ransomware.
CryptoLocker encrypts various types of files (.doc .xls .ppt .eps .ai .jpg .srw .cer) found on the compromised device.
Although the removal process of this virus is straightforward, there are no known tools for decrypting encrypted files.
Nowadays, ransomware attacks are becoming more and more complex, and due to the encryption capabilities now available, it is especially important to back up your files.
Automatic malware removal
Manual threat removal could be a lengthy and complicated process that requires advanced computer skills.
Malwarebytes is a professional automatic malware removal tool useful for deleting malware.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
CryptoLocker virus removal: step 1
For Windows XP and Windows 7 users:
- Start your computer in safe mode;
- Click on “Start”, select “Close session”;
- Click on “Restart”, then on “OK”;
- During the computer startup process, press the “F8” key on your keyboard several times until the “Windows Advanced Options” menu appears.
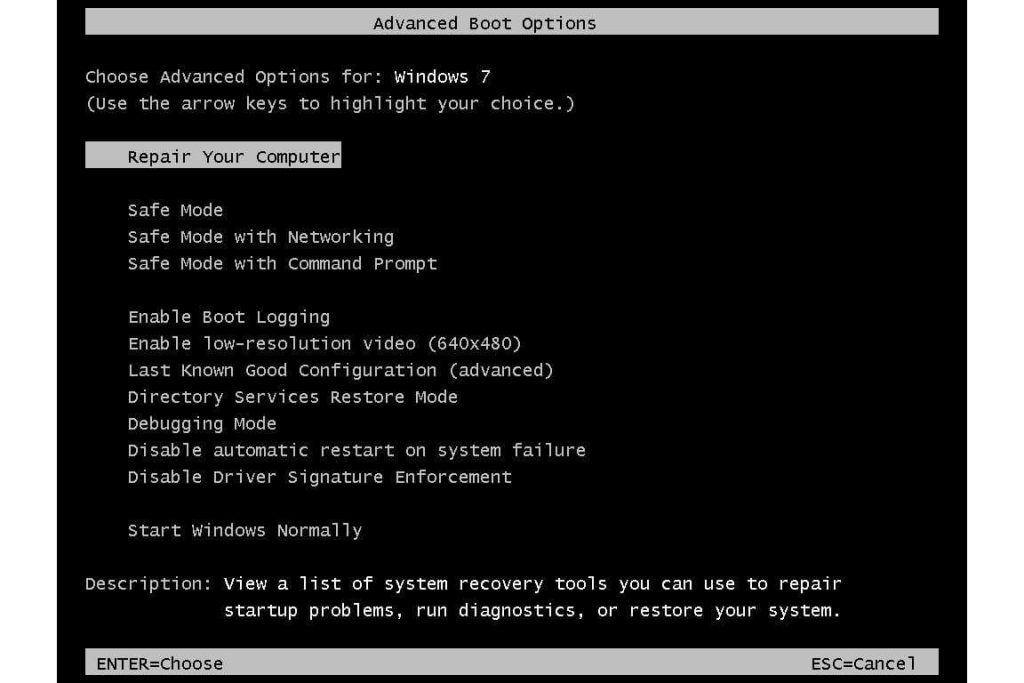
- then select “Safe Mode with Networking” from the list.
Windows 8 users:
- go to the Windows 8 Start screen, type “Advanced”;
- in the search results select “Settings”;
- Click on “Advanced Startup Options”;
- in the “General PC Settings” screen select “Advanced Startup”;
- Click on the “Restart Now” button;
- The computer will now restart in the “advanced boot options menu”;
- Click on the “Troubleshoot” button, then on the “Advanced Options” button;
- In the advanced options screen click on “Startup Settings”;
- Select “Restart”;
- The PC will restart in the Startup Settings screen;
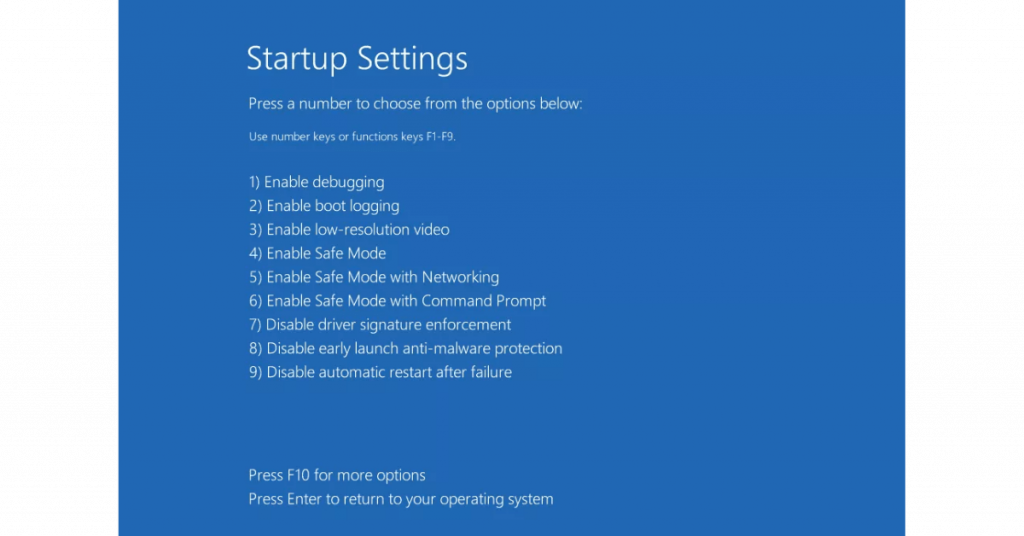
- Press “5” to start Safe Mode with Networking.
CryptoLocker virus removal: step 2
- Log in to the account infected with the CryptoLocker virus;
- Launch your internet browser and download a legitimate anti-spyware program;
- Update the anti-spyware software and start a full system scan;
- Remove all detected entries.
If you can’t start your computer in Safe Mode with Networking, try performing a System Restore.
Follow these steps:
- During the computer startup process, press the “F8” key on your keyboard several times until you see the “Windows Advanced Options” menu,
- then select “Safe Mode with Command Prompt” from the list, press “ENTER”.
- When command prompt mode loads, enter the following code: cd restore and press “ENTER”.
- Then type: rstrui.exe and press “ENTER”.
- In the screen that opens, click on “Next”.
- Select one of the available restore points and click “Next”: this will restore your computer system to an earlier time and date, before the ransomware virus infiltrated your PC).
- In the next screen, click on “Yes”.
- After restoring your computer to an earlier date, download and scan your PC with the recommended malware removal software to delete any remaining CryptoLocker files.
If you can’t startyour computer in Safe Mode with Networking (or Command Prompt), boot your computer using a recovery disc.
Some variants of ransomware disable Safe Mode, making it difficult to remove, so you’ll need to log in to another computer to perform this step.
In any case, as we keep telling you, to protect your computer from such file-encrypting ransomware, you need to use reputable antivirus and antispyware programs.
In case it is too late for the protection phase, contact HelpRansomware to fix the damage that the malware has caused to your PC.
Conclusions
CryptoLocker is a ransomware virus, created by hackers.
From this guide we can draw the following conclusions:
- CryptoLocker is distributed through exploit kits;
- They infiltrate vulnerable computers and software;
- Cybersecurity prevents ransomware attacks;
- Once a system is infected, the cybercriminal asks for a ransom payment.
The power of ransomware has increased in recent years. The best option against CryptoLocker is to not pay the ransom and contact specialists, such as HelpRansomware.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.