Learn all about REvil ransomware, how it spreads, and major attacks. Find out when it started and why it was successful.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
What is REvil ransomware?
REvil ransomware is one of the latest types of ransomware that has recently gained ground.
This malware is distributed through phishing emails, malicious links, and other social engineering methods.
REvil first appeared in 2019 and has been spreading until early 2022.
It is part of the Ransomware-as-a-Service (RaaS), known as Sodinokibi.
When did the REvil ransomware start?
Considering that this ransomware first surfaced in April 2019, its criminal history is not particularly extensive.
And it has now been shut down.
Who are the REvil hackers?
It took a lot of work to determine who the REvil ransomware hackers were.
In November 2021, INTERPOL announced a joint operation involving 19 agencies in 17 countries in relation to this ransomware, among other crimes:
‘GoldDust has disrupted a ransomware cybercrime gang and arrested seven suspects. The operation established a global threat picture about attacks by ransomware families, particularly GandCrab and REvil Sodinokibi.’

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
Who is behind REvil?
All theories and evidence suggest that the group behind REvil ransomware is Russian.
Joe Biden said in a White House statement about the INTERPOL operation:
‘When I met with President Putin in June, I made clear that the United States would take action to hold cybercriminals accountable. We are bringing the full strength of the federal government to disrupt malicious cyber activity and actors.’
Where did REvil originate?
According to experts, REvil ransomware, known as Sodinokibi, comes from Russia.
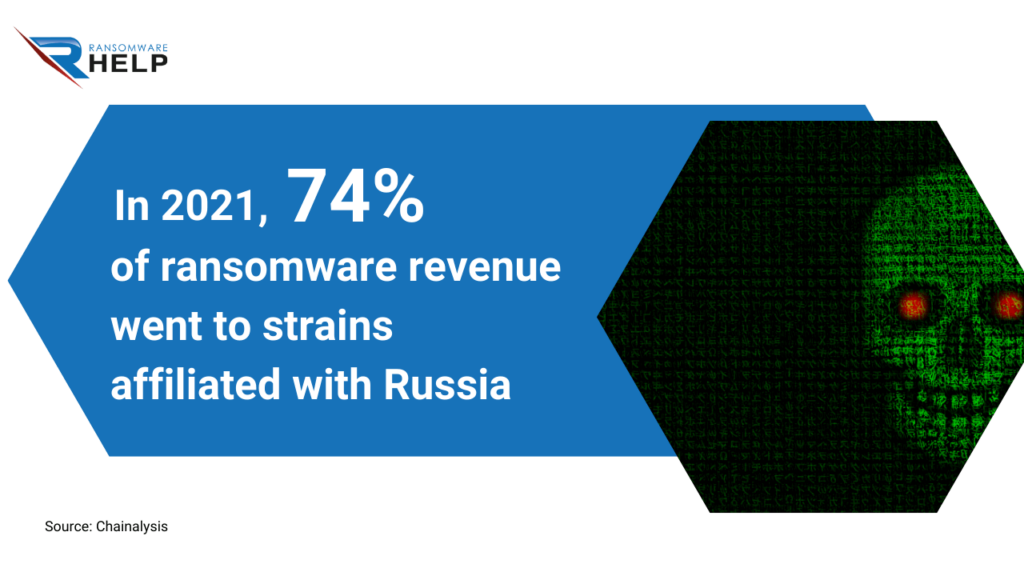
The study of the blockchain company Chainalysis reinforces the theory, as 74% of ransomware revenue in 2021 went to strains affiliated with Russia.
The UNIT 42 report indicates that REvil or Sodinokibi ransomware bears similarities with the GandCrab group:
‘In early 2019, the authors behind GandCrab announced that they were retiring as they had made enough money and done enough damage. However, around the same time, a new ransomware threat called REvil was emerging.’
REvil ransomware file extension
The added file extension warns that the data has been encrypted by ransomware.
Documents are most likely to have a different length.
For example, they change from myCV.docx to myCV.docx.locked.
If ransomware has encrypted your files with some of these extensions, contact HelpRansomware.
The company is an expert at removing ransomware and opening encrypted files.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
REvil ransomware world map overview
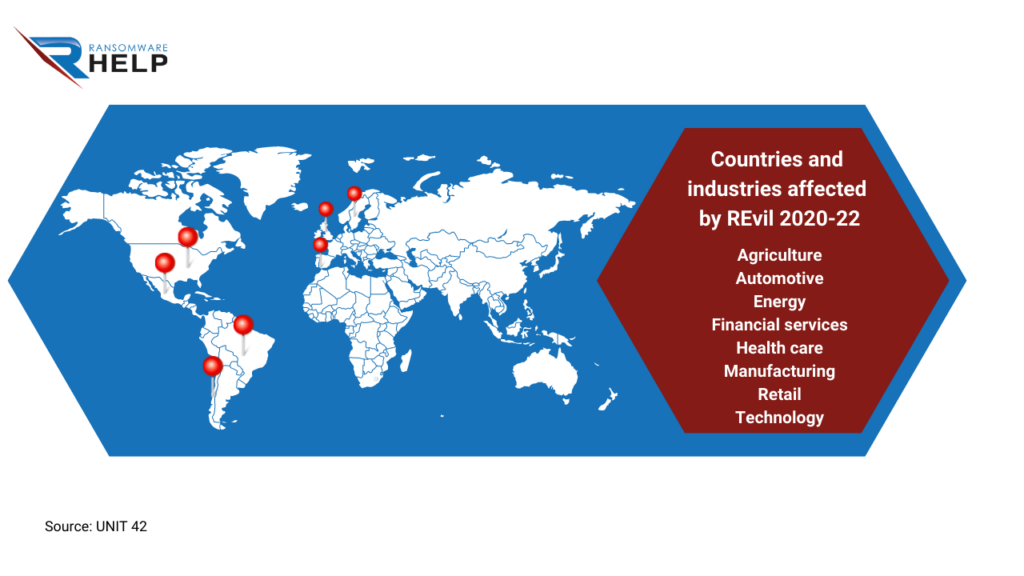
UNIT 42 analyzed REvil ransomware from 2020 to 2022.
From April 2019 to July 2021, it affected the following industries:
- Agriculture;
- Automotive;
- Energy;
- Financial services;
- Health care;
- Manufacturing;
- Retail;
- Technology.
The countries hit were:
- Brazil;
- Chile;
- Spain;
- United Kingdom;
- Mexico;
- Sweden;
- United States of America.
Kaseya was hit by a major ransomware attack in July 2021. We will go through it in the upcoming sections.
Data for 2022 are not available since the year has not yet ended, but the report indicates the following about REvil ransomware:
‘On April 2022, REvil’s old leak site went online and started redirecting visitors to a new Onion address, listing new and previous victims. The new site includes a ‘Join Us’ section for active affiliate recruiting.’
The only economic data referred to 2020, when the average ransom payment was $508,523.

Top REvil ransomware attacks
In July 2022, the REvil ransomware attack against the cybersecurity company Kaseya was the biggest in history.
UNIT 42 describes it:
‘REvil affiliates carried out a supply chain attack on Kaseya. They used Kaseya servers to execute the ransomware and hit unsuspecting victims. It was due to a vulnerability found by the threat actors.’
As mentioned earlier in this article, INTERPOL has arrested several hackers, including the one responsible for this attack.
The attack affected more than 1,000 companies at the same time in numerous countries, such as Argentina, Canada, Spain, the United Kingdom, Mexico, the United States, and South Africa.

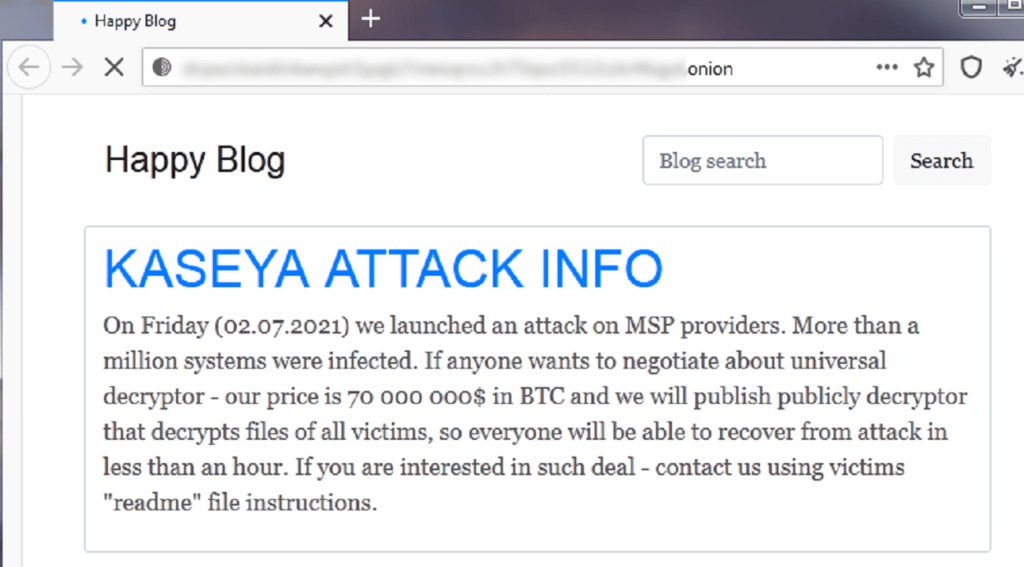
The REvil group reported, on its Dark Web site, that more than a million systems were compromised and offered a decryptor to all victims for $70 million.
Kaseya’s website was up to date with the latest information about the ransomware attack.
The multinational Acer is another victim of REvil ransomware.
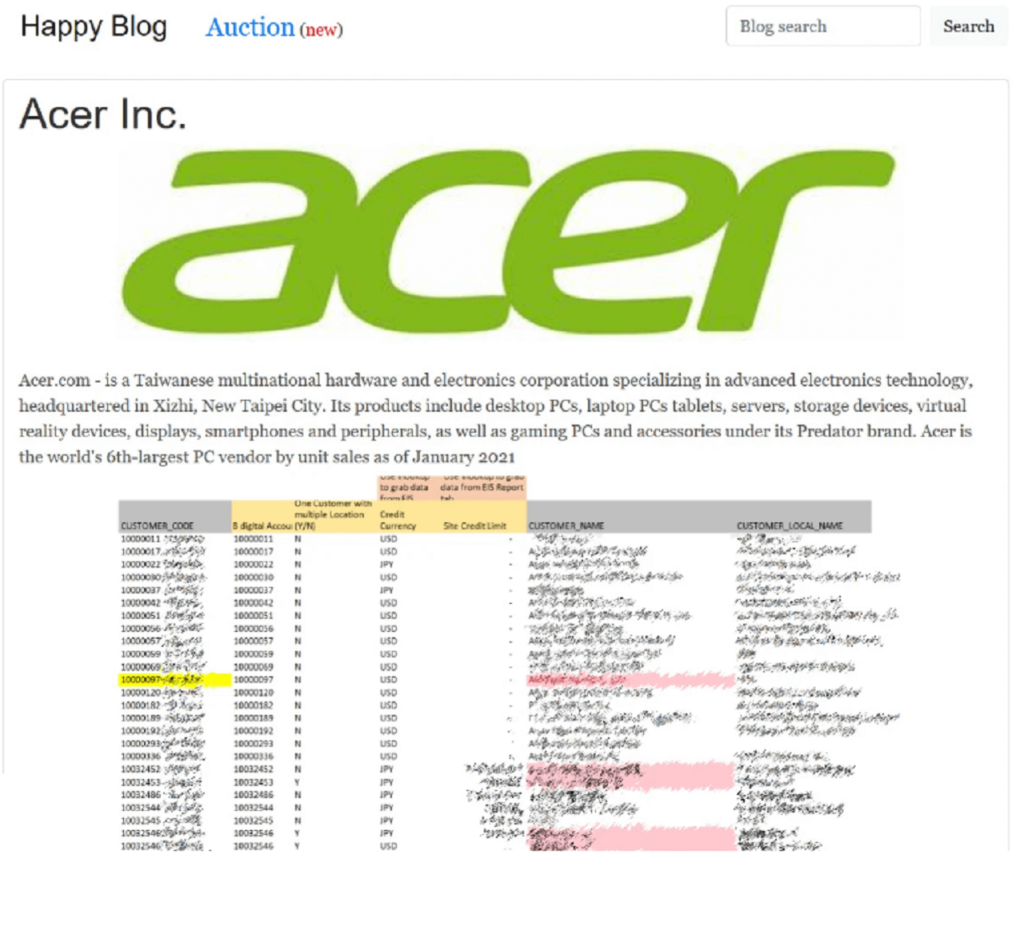
The hacker group leaked private company information, such as bank movement or balance data.
Businesses are the primary victims of ransomware as they need to recover encrypted files quickly.
What they should avoid is paying the ransom to cybercriminals.
If you give in to extortion, the hackers will demand more money again.
In case of a ransomware attack, contact a specialized company like HelpRansomware.
Their team is skilled at remove ransomware and decrypting files.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
Is REvil ransomware still around?
In January 2022, the security service dismantled the REvil ransomware criminal group after arresting its members.
However, on April 2022, REvil’s former Tor platform was back in action.
It was edited to redirect visitors to new ransomware links.
It still needs to be determined who is behind the new movements.
Jakub Kroustek, malware research director at Avast, posted a tweet saying they blocked a REvil ransomware variant.
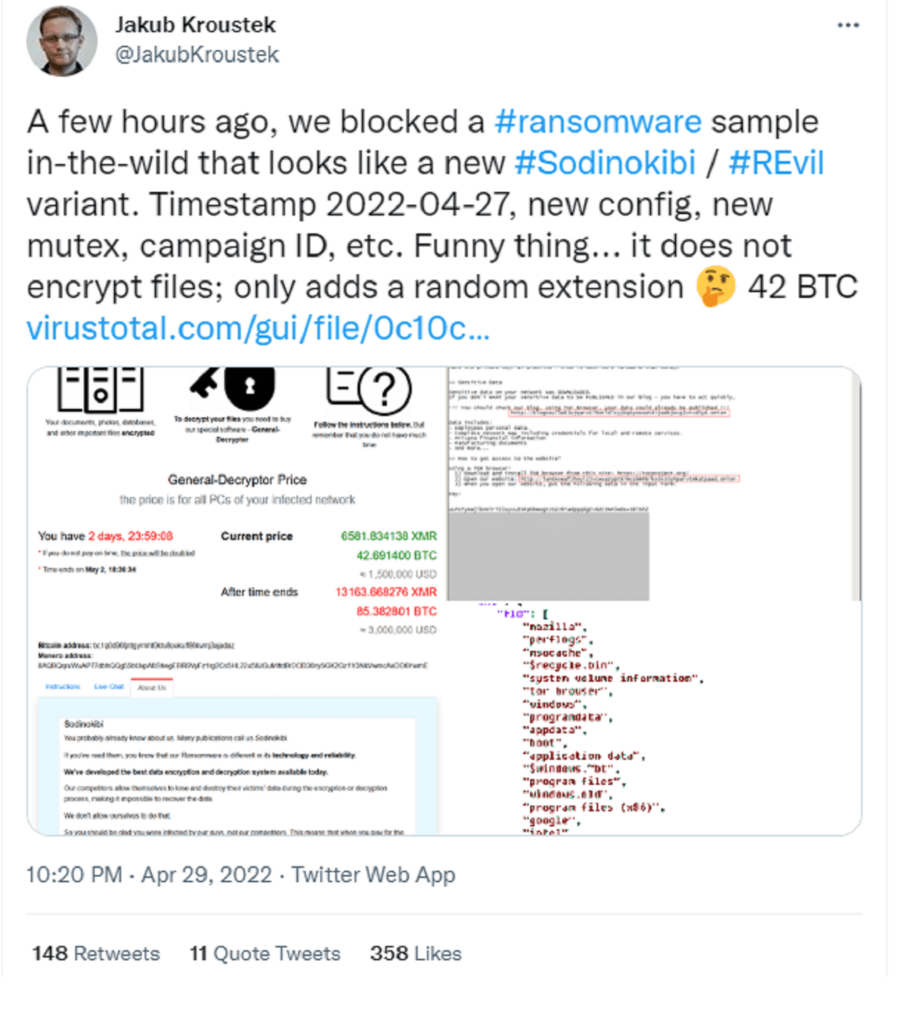
What happened to REvil ransomware?
In January 2022, the Federal Security Service of the Russian Federation (FSB), together with the Investigative Department of the Russian Ministry of Internal Affairs, announced the arrest of 14 Sodinokibi members:
‘The FSB of Russia established the full composition of the REvil criminal community and the involvement of its members in the illegal circulation of means of payment and documented illegal activities.’
In the operation, they seized funds and other assets at 25 addresses belonging to the 14 detained people:
- Over 426 million rubles;
- USD$600,000;
- €500,000;
- Crypto wallets;
- Computer equipment.
With the team’s arrest, REvil ceased to exist in January 2022.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
How does REvil ransomware spread?
This ransomware spreads mainly through phishing emails.
The email contains a malicious attachment, and when opened, the virus runs and starts encrypting files on the computer.
Hackers encrypt all the files and demand a ransom in exchange for the decryption key.
Many cybercriminals are now using email spamming as one of their preferred methods of spreading malware.
They know that most users need to adequately check their email attachments and send them as if they were legitimate.
If you are a ransomware victim, contact a company of experts to help you remove the ransomware and restore encrypted files.
HelpRansomware, with over 25 years of experience, assists 24/7 and guarantees 100% of the process: from removal to decryption.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
REvil ransomware detection
Let us read below some techniques to detect ransomware:
- Identify ransomware payload: look for executables using ‘REvil,’ ‘WannaCry,’ or ‘Locky’;
- Monitor system registry changes;
- Decrease in disk storage space;
- Rise in CPU utilization.
Sometimes, detecting ransomware infection may be challenging as there might be no apparent signs.
How successful is REvil?
The attack on Kaseya, explained above, demonstrates the strength and success of REvil ransomware.
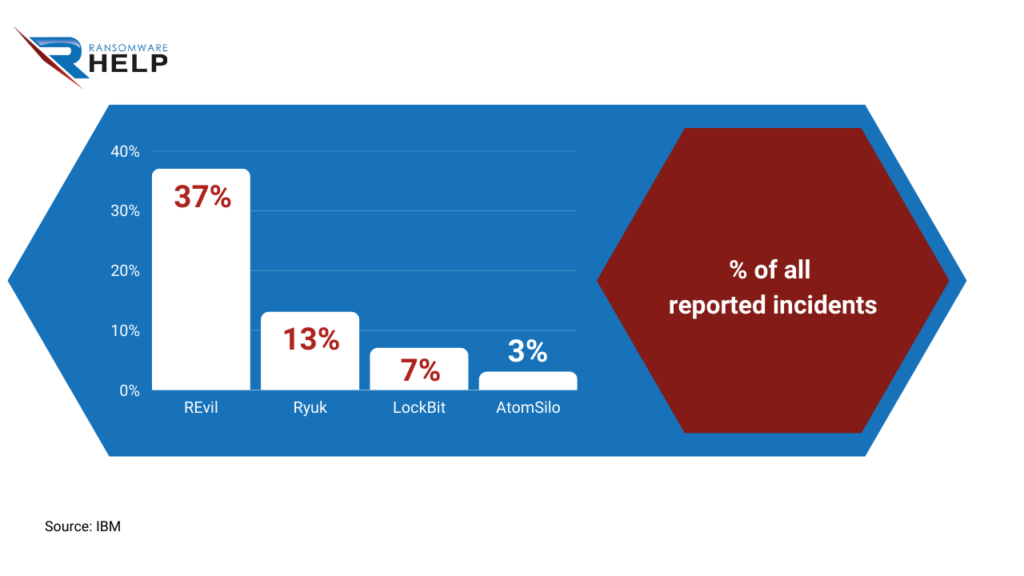
The report IBM Security X-Force Threat Intelligence Index 2022 also provides information about this ransomware.
In 2021, REvil accounted for 37% of all reported incidents, followed by Ryuk (13%), LockBit 2.0 (7%), and AtomSilo (3%).
Protection against ransomware attacks
HelpRansomware offers tips to protect yourself against ransomware:
- Use an external hard drive or cloud storage for backups;
- Keep PC software up to date;
- Be careful what websites you visit;
- Pay close attention to emails in your inbox; check the email sender and attachments;
- Use strong passwords and do not share them with others;
- Enable 2FA (two-factor) authentication on service accounts;
- Avoid downloading pirated software or illegal content.
Ransomware attacks are very aggressive, and it is essential to protect computers against malware.
HelpRansomware helpscompanies prevent ransomware attacks through services such as cyber security consulting.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
How to protect yourself against REvil?
Although REvil is not now among the most potent ransomware, it will be put on the cybercrime market via another variant.
For this reason, Internet users must also apply protection and defense guidelines, such as:
- Backups: back up data regularly and store it offline;
- Antivirus: installing antivirus software on all computers and keeping it up to date;
- Awareness: train employees about ransomware, how to recognize them, and what steps to take in case of an attack.
These tips are fundamental for individuals and companies, which are the main target of ransomware.
Conclusions
This guide shows you what REvil ransomware is, how it spreads, and its major attacks. Find out when it started and why it was so successful.
We can draw the following conclusions from this article:
- REvil has been well-known ransomware from 2019 to the present;
- It no longer operates, but very similar variants are appearing;
- INTERPOL and FSB have dismantled the group of cybercriminals behind REvil;
- The attack on Kaseya is the biggest perpetrated by REvil, affecting more than 1,000 companies and demanding a ransom of $70 million;
- Acer was also a victim of this ransomware, which leaked banking transactions, and more financial data;
- Ransomware typically spreads through phishing emails.
Although security services disarmed the REvil band at the beginning of 2022, new variants have already appeared.
It further proves that ransomware is still evolving and cannot disappear permanently.
If you are a ransomware victim, contact the leading ransomware removal and file decryption company, HelpRansomware.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.



