A new ransomware attack shakes Japan
The recent ransomware attack against Asahi Group Holdings, one of the world’s largest beverage producers, has once again highlighted the magnitude of the global threat posed by cyber extortion groups.
The Japanese company officially confirmed the incident in a corporate statement, pointing out flaws in its ordering and distribution systems.
Although Asahi has not publicly claimed responsibility, multiple cybersecurity firms link the case to Qilin, an emerging collective identified by the ENISA Threat Landscape 2025 report as one of the three most active ransomware groups of the year.
According to the report, Qilin accounts for more than 20% of incidents detected in Europe, along with Akira and FOG, consolidating its presence beyond Asia.

Qilin and the Ransomware-as-a-Service model
Qilin operates under a Ransomware-as-a-Service (RaaS) scheme, where various affiliates rent its infrastructure and encryption tools to execute tailored attacks.
This model—already popularized by families such as LockBit 3.0 — has turned ransomware into a full-blown industry, capable of simultaneously attacking companies in critical sectors, from transportation to energy.
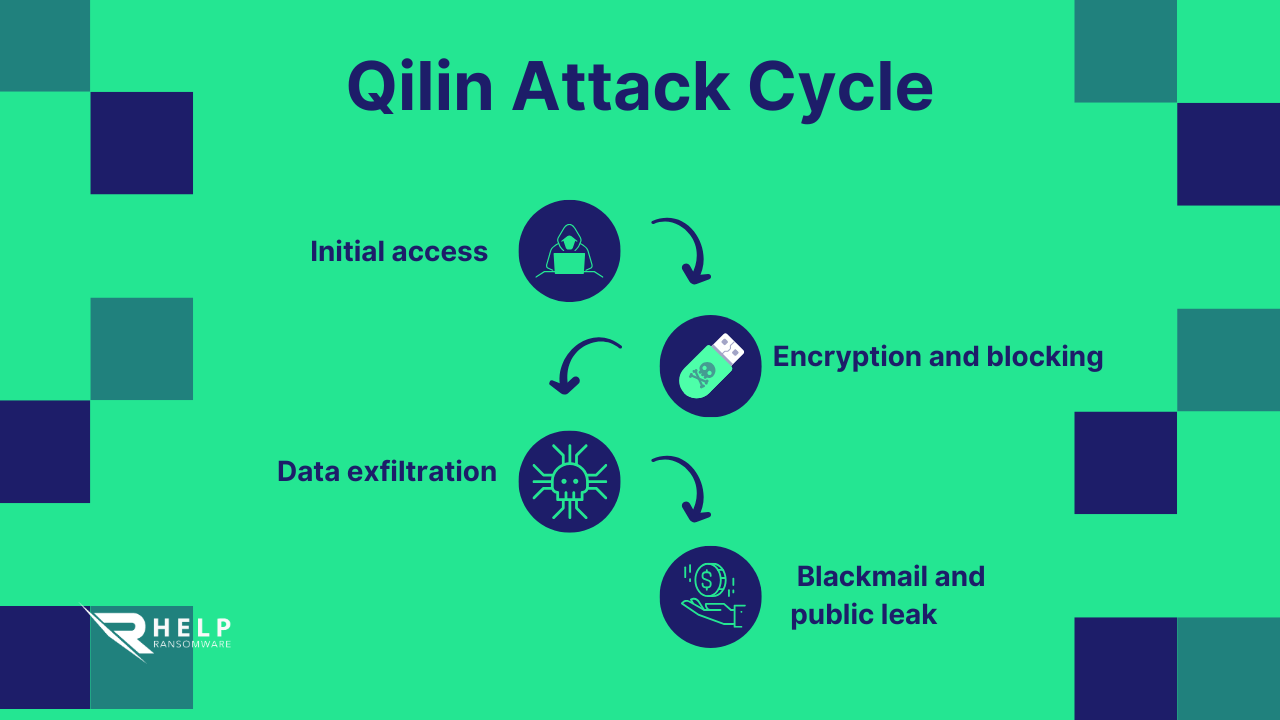
The Asahi case shows the same pattern of double extortion ransomware :
- Data encryption on compromised servers.
- Theft and exfiltration of confidential documents.
- Public threat of leak if ransom is not paid.
This method, which combines operational and reputational pressure, replicates what has been seen in previous attacks on companies such as Costa Rican government or TAP Air Portugal.
Extortion is no longer just about money: it’s about media visibility and brand damage.
Modern ransomware: Rust, automation, and artificial intelligence
Unlike more classic variants like Ryuk or Clop ransomware, Qilin, is developed in Rust and Golang, making it cross-platform (Windows, Linux, and ESXi) and more difficult to detect with traditional security solutions.
Its creators implement advanced obfuscation mechanisms, log erasure, and backup deletion, complicating any recovery attempts.
The group also leverages artificial intelligence in cybersecurity to automate target selection and tailor its negotiation messages.
This trend, which HelpRansomware has already detected in other families such as Buhti and Akira, heralds a scenario where attacks will become more personalized and difficult to trace.

Lessons from the Asahi case: how to strengthen the defense
The Asahi attack confirms that no sector is immune to risk. Defense against ransomware must combine prevention, detection, and response.
The most resilient organizations are those that:
- They maintain isolated and verified backup copies.
- They implement continuous monitoring and detection of anomalous behavior.
- Crisis management plan with communication and immediate response protocols.
- They train their employees through drills and cyberattack training.
Anticipation is key: every minute of delay in detection can mean hours of downtime and millions in losses.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
Conclusion: Anticipate, Resist, and Respond
The Asahi case and the expansion of Qilin demonstrate that ransomware is now a structural threat to the global economy.
It’s no longer enough to simply protect systems: companies must understand that digital resilience is a competitive advantage. At HelpRansomware, we help organizations recover data without paying ransoms using decryption key technologies, secure restoration, and strategic consulting.
The lesson is clear: prevention, visibility, and response capabilities make the difference between a controlled crisis and an operational catastrophe.



