Read the guide and discover the ransomware definition in all its facets: what is it, why it is such an effective attack method and how you can protect your organization from this danger.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
What is ransomware [DEFINITION]
What is ransomware? It’s an advanced form of cyberattack and one of the threats that security teams around the world face most frequently.
Ransomware is used to target all organizations, from small teams to large enterprises, from cities to government networks.
While simple in concept, ransomware is extremely malicious – it has the potential to cripple networks and cause catastrophic damage to infrastructure.
It is a type of malware that, once downloaded on a device, encrypts or deletes all data until a ransom is paid to restore it.
It was estimated that in 2020 there was a ransomware attack every 14 seconds, numbers that will drop further in 2021: forecasts speak of an attack every 11 seconds.

One of the most famous ransomware attacks is the one triggered by WannaCry.
WannaCry infected over 230,000 computers in 150 companies in a single day, encrypted all files found on the devices, and required users to pay $ 300 in bitcoins to restore them.
The options are either you pay the ransom or you decide not to give in to blackmail and address to a company that can ransomware decryption.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
WannaCry mainly affected large organizations – the National Health Service in the UK was one of the highest-profile targets.
Surprisingly, the impact of the attack was less powerful than assumed because it was stopped relatively quickly and did not target highly critical infrastructure, such as railways or nuclear power plants.
Even so, the attack caused economic losses of millions of dollars.
More recently, 23 cities in Texas were hit by ransomware attacks in which attackers demanded $ 2.5 million to restore encrypted files.
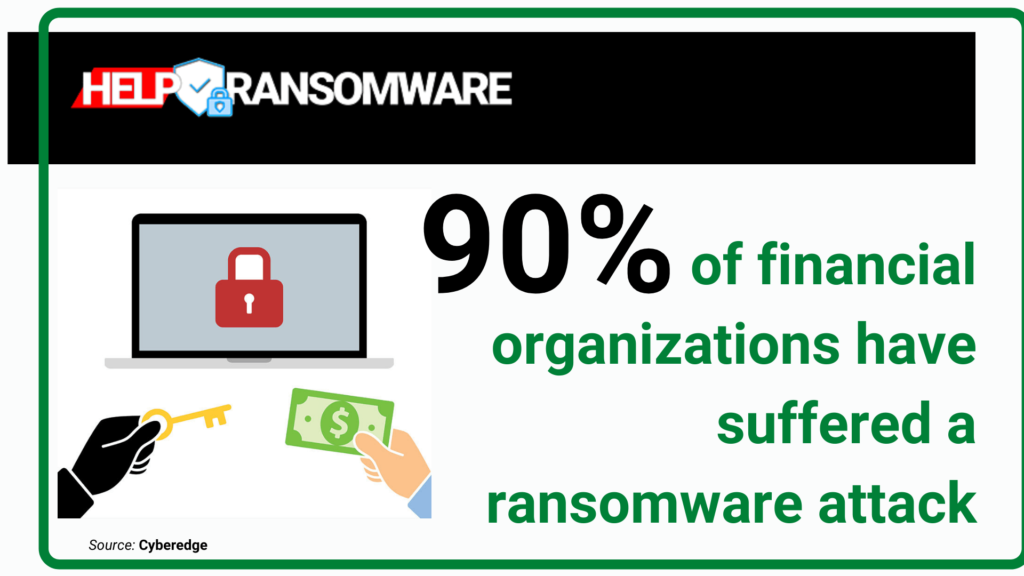
In general, ransomware is a type of attack particularly prevalent in financial organizations: 90% have suffered an attack in the last year.
How does ransomware work?
Ransomware is triggered by downloading malicious software to an endpoint device, such as a desktop computer, laptop or smartphone.
Usually, this process is caused by user errors and ignorance of security risks.
A very common method through which malware is spread is phishing attacks: the attacker attaches an infected document or URL to an email, masking it as safe to trick users into opening it and installing the malware on the device.
Equally popular is the use of a type of virus called trojan horse.
In this case, the ransomware is disguised as legitimate software, so it will infect devices after users install it.
File encryption
Ransomware typically works very quickly.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
Within seconds, the malicious software will take control of the critical process device and search for files to encrypt, which means that all the data inside will be encrypted while, probably, the ransomware will delete all those files it cannot encrypt.
The ransomware will then infect any other harddrive or USB device connected to the infected host machine.
Any new devices or files added to the infected device will also be encrypted after this point.
Then, the virus will start sending signals to all other devices on the network, trying to infect them as well.
The whole process happens extremely quickly and in few minutes the device will display a message similar to this:
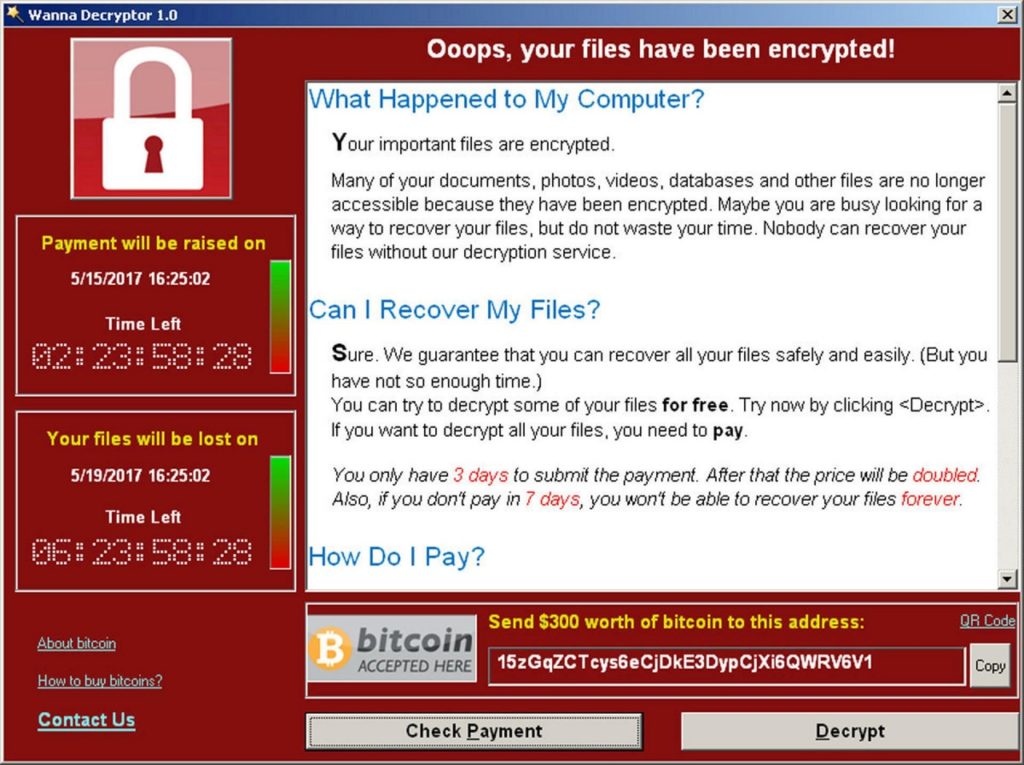
This is the message displayed by users who have been infected with the WannaCry ransomware.
As you can see, this is a form of “cyber blackmail”, in which users are notified that their files are locked and that, if they’ll not pay, files will be deleted.
Payments will probably be required in bitcoin, as this virtual currency cannot be tracked.
Besides, there is often a countdown, which serves to pressure companies to act quickly.
There are several types of ransomware.
Some threaten to make encrypted data public, which is extremely dangerous for companies that need to protect corporate or customer data.
Another way involves scareware, which floods the computer with pop-ups and asks for a ransom to solve the problem following the same system: a malicious program infects the computer and is required a payment to remove it.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
Why is ransomware so effective?
As we just mentioned, ransomware can be extremely harmful to businesses.
First of all, they have to deal with the loss of files and data that are the result of hard work, or customer data that are essential for the smooth functioning of the organization.
Add the loss of productivity, because machines will be unusable: according to Kaspersky, in most cases, organizations take at least a week to recover their data.
Last, but not least, there is the economic loss of replacing infected machines, paying an IT company to remedy the attack and putting in place protections to prevent it from happening again.
For these reasons, many companies feel they have no choice but to pay the ransom, although it is highly recommended not to do (especially considering it doesn’t guarantee the data decryption).

Ransomware makes hackers earn more than $ 25 million in revenue per year, which shows how effective it is to extort money from organizations.
Ransomware targets human weaknesses
By targeting people with phishing attacks, attackers can bypass traditional security technologies with ransomware.
Email is a weak point in many companies’ security infrastructure, and hackers can exploit it by using phishing emails to trick users into opening malicious files and attachments.
Using Trojan horse viruses, hackers target human error by tricking you into inadvertently downloading malicious files.
The main problem here is that many users lack awareness of security threats: many people are not conscious of the type of threat they might encounter, much less what practices they should avoid on the net or even which ones file download or open on the internet or in emails.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
This lack of security awareness helps ransomware spread much faster.
Lack of strong technological defenses
Ransomware attacks are growing at a record high, with attackers developing ever more sophisticated malware.
Many companies lack the strong defenses necessary to block these attacks because they can be expensive and complicated to implement and use.
Business executives often understand the need for having strong security defenses only when it’s too late and systems have already been compromised.
Expired hardware and software
In addition to lacking strong defenses against attacks, many organizations rely too much on outdated hardware and software and, over time, attackers discover security vulnerabilities.
Technology companies often provide security updates, but they can’t verify if all the organizations installed them.
Several organizations also rely on older computers that are no longer supported, which means they are open to vulnerabilities.
This is one of the main reasons why the WannaCry virus has been so successful.
It targeted many large organizations such as the NHS, which mostly use decades-old machines with operating systems that are no longer regularly supported by updates.
The exploit used by WannaCry to infect systems was discovered two months before the attack and was corrected by Microsoft; however, the devices were not updated, so the attack spread quickly.
How can you stop the ransomware?
The best way companies have to stop ransomware attacks is to take a proactive approach to security and make sure they have effective protections before ransomware can infect systems.
For emergencies, also check out our guide to the 150 best ransomware decryption tools.
But since it’s always better to be safe than sorry, here are some tips to put in place to protect yourself from future ransomware attacks.
Reliable endpoint antivirus protection
One of the most efficient ways to stop ransomware is having a good endpoint security solution.
These ransomware solutions are installed on devices and prevent any malware from infecting systems.
They also give administrators the ability to see when devices have been compromised and ensure that security updates have been installed.
These solutions can help you to protect against malicious downloads and can alert users when they visit risky websites.
Of course, these systems are not guaranteed to be 100% effective as cybercriminals always try to create new malware that can bypass security tools, but it is still a crucial step for an effective protection against malware.
Security of inbound and outbound emails
Since ransomware is commonly sent via email, email security is critical to stopping ransomware.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
Email scanning technologies filter communications by activating defenses for URLs and using attachment sandboxing to identify threats and block their delivery to users.
This step can prevent ransomware from arriving on endpoint devices and prevent users from inadvertently installing the ransomware on their device.
Ransomware is also commonly distributed via phishing.
Email gateways can block phishing attacks, but there are also post-delivery protection technologies, which use automatic storage and artificial intelligence algorithms to detect phishing attacks and display warning banners within emails to notify you of suspicious content.
Web Filtering and Isolation Technologies
DNS Web filtering solutions prevent users from visiting dangerous websites and downloading malicious files.
Those help block downloads of viruses that spread ransomware, including Trojans, that mask malware as legitimate business software.
DNS filters can also block malicious third-party ads.
Web filters must be configured to aggressively block threats and prevent users from visiting dangerous or unknown domains.
Isolation can also be an important tool for blocking ransomware downloads: isolation technologies completely remove threats by isolating browsing activity on secure servers and showing users a secure rendering.
This way you can prevent ransomware because any malicious software runs in the protected space and does not reach the users.
The main benefit of isolation is that it does not affect the user experience in any way, offering high-security effectiveness with a seamless browsing experience.
Security Awareness Training
Your organization’s internal staff can be your worst security breach.
In recent years, there has been a huge growth of platforms that are concerned with creating awareness around the security problem, educating users about risks they run using the Internet at work and home.
Proper training helps to have users aware of the threats lurking within e-mails or the network in general.
As a result, they will be aware of the best security practices to follow to stop ransomware, such as making sure their endpoints are updated with the latest security software.
Security training courses typically also provide phishing simulation technologies.
This means that administrators can create custom simulated phishing emails and send them to employees to check how well they can detect attacks.
Phishing simulation is an ideal way to visualize the effectiveness of security throughout your organization and is a useful tool for identifying those employees who may need more training in the procedures that allow them to stop the spread of ransomware.
Data backup and restore
If the ransomware attack was successful and your data was compromised, the best way to proceed is to quickly restore the data you need and minimize downtime.
The best way to protect your data is to ensure that it is backed up to multiple locations, including the primary storage area, local disks, and a continuity cloud service.
In the event of a ransomware attack, a backup ensures you to mitigate the loss of any encrypted files and regain the functionality of your systems.
The best Cloud Data Backup and Recovery platforms allow companies to recover data in the event of a disaster, they’re available at any time and can be easily integrated with existing cloud applications and endpoint devices, creating a secure and stable global cloud infrastructure.
Backup and restoring data on the cloud are essential tools not so much to prevent ransomware as to fix the damage it causes.
Conclusion
Don’t let ransomware harm your organization.
By following the steps above, you can start protecting your business from malicious ransomware attacks.
If you need further help in finding out how to protect yourself from ransomware, please contact us.
Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.




