Over the past few years, cloud storage has become a cornerstone of digital transformation. Businesses of all sizes have migrated critical data, sensitive information, strategic assets, and personal data to cloud infrastructures, drawn by the promise of greater flexibility, scalability, and operational efficiency. However, this rapid adoption has been accompanied by a dangerous perception: the belief that the cloud is inherently secure.
The reality is more complex. The risks of cloud storage don’t disappear; they simply change in nature. Direct control diminishes, the attack surface expands, and responsibility is distributed between provider and customer in a way that many organizations don’t fully understand. In this context, blindly trusting the cloud can become one of the biggest strategic security mistakes.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
Talking about the risks of cloud storage is not questioning the technology, but understanding its real limitations and acknowledging that security remains an active responsibility of the company.
The myth of the cloud as an automatically secure environment
One of the most common mistakes is assuming that when migrating data to the cloud, security is completely delegated to the provider. Large cloud services have robust infrastructures, certifications, and high levels of availability, but this does not equate to automatic data protection.
Cloud security operates on a shared responsibility model. The provider protects the physical infrastructure and certain platform components, while the company remains responsible for configuration, access, identity management, and data protection. When this distinction is not clearly understood, the risk increases exponentially.
Many cloud data breaches are not due to advanced technological failures, but rather to basic configuration errors, excessive permissions, or compromised credentials. In these cases, the problem is not the cloud itself, but how it has been implemented and governed.
The false sense of security after migration
After migrating to the cloud, many organizations experience a sense of relief: automatic backups, high availability, and geographic redundancy. However, this perception can be misleading. A misconfigured cloud environment can expose critical data directly to the internet without the company noticing for months.
This false sense of security often becomes a key factor when ransomware occurs. By assuming that cloud infrastructure offers automatic protection, many organizations relax basic security controls, such as identity management, access segmentation, and backup protection. When an attacker exploits these weaknesses, the impact of the incident is rapidly amplified, affecting not only systems but also data integrity and the company’s ability to respond.
The real risks of cloud storage that few companies assess
When analyzing the risks of cloud storage from a realistic perspective, recurring patterns emerge in incidents across different sectors and regions. One of the most frequent is the unintentional exposure of data, caused by incorrect configurations of cloud services, unnecessary public permissions, or insecure integrations.
Another critical risk is poor identity and access management. In cloud environments, not only employees gain access, but also suppliers, applications, service accounts, and automated processes. Without a strict access control policy, this ecosystem becomes an ideal entry point for attackers.
This is compounded by operational dependence on the provider, both technically and contractually. A service interruption, human error, or a poor incident response can directly impact data availability and business continuity.
Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
Ransomware also exploits cloud environments
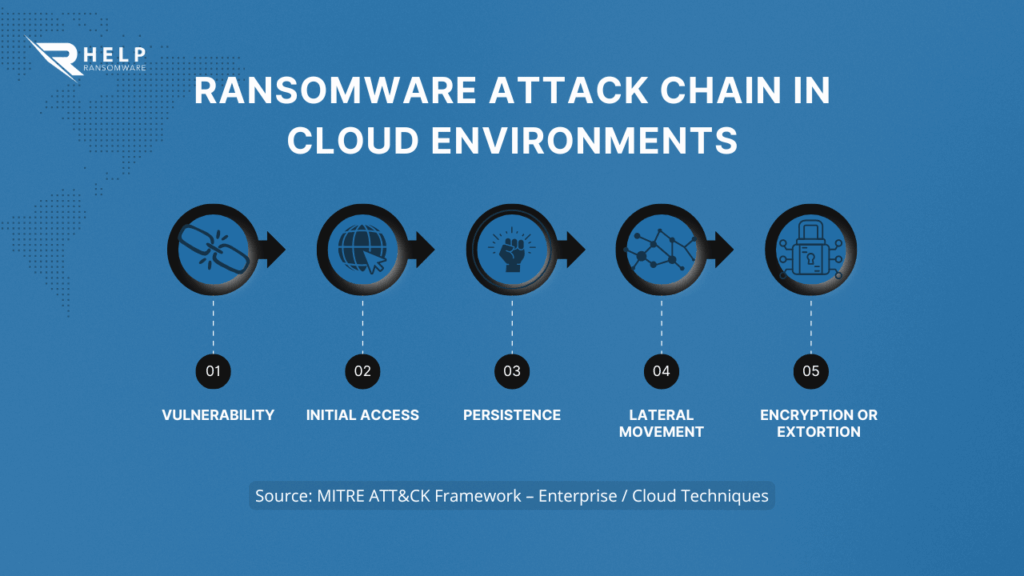
Modern ransomware is not limited to local servers or traditional infrastructure. Increasingly, attackers are designing their campaigns to exploit compromised cloud credentials, poorly secured automatic synchronizations, and excessive permissions in cloud storage environments. A single elevated access point can be enough to encrypt large volumes of data, delete snapshots, disable recovery mechanisms, and compromise backups that the organization considered secure.
In this context, a ransomware attack can escalate rapidly and affect multiple systems from a single point of entry.
In cloud environments, the impact of a ransomware attack can be amplified exponentially. The interconnection between services, automatic data replication, and reliance on centralized identities allow an attacker to move laterally quickly, affecting multiple systems in a very short time.
Furthermore, many organizations do not detect these intrusions immediately, as access occurs through valid credentials, which delays the response and significantly increases the extent of the damage.
The legal and regulatory impact of a cloud breach
A cloud data breach is not just a technical problem. It triggers immediate legal consequences that can last for years. Current regulations do not distinguish between data stored on-premises and data stored in the cloud: the responsibility still lies with the company.
In Europe, the GDPR establishes clear obligations in the event of security breaches: notification to authorities, communication with those affected, and detailed documentation of the incident. These processes are usually accompanied by audits, regulatory investigations, and ongoing public scrutiny.
This approach is supported by international standards such as those defined by the National Institute of Standards and Technology (NIST), which underline the need to identify, classify, and protect data regardless of its location.
The cloud as an amplifier of reputational risk
When a breach occurs in the cloud, the exposure is typically greater. Systems are interconnected, and the impact can quickly spread to customers and third parties. This transforms the incident into a matter of trust, reputation, and business continuity, not just regulatory compliance.
Corporate data protection strategy becomes essential to limit reputational damage and preserve the trust of customers and partners. It’s not just about regulatory compliance, but about demonstrating responsible information management, with clear controls over access, data classification, and incident response capabilities.
Organizations that integrate data protection into their business strategy are better prepared to contain the damage and prevent a one-off breach from turning into a prolonged crisis.

When technical recovery does not restore confidence
One of the most common mistakes is assuming the crisis ends when systems are back up and running. In reality, that moment often marks the beginning of the most complex phase of the incident. Even if operations are restored, the company must face legal notifications, audits, regulatory investigations, and media pressure.
Technical recovery is usually measured in days or weeks. Reputational recovery can take years. Customers who don’t renew contracts, partners who tighten terms, or investors who lose confidence are common consequences of a poorly managed cloud breach. This time lag explains why many organizations underestimate the true impact of the incident: by the time systems are back up and running, the damage to credibility has only just begun, affecting market relations and the company’s long-term image.
The digital record of the incident
In a digital environment where information remains permanently accessible, a cloud security incident can continue to influence brand perception long after systems have been restored. Archived articles, public reports, regulatory communications, and mentions in the media or on social networks ensure that the incident doesn’t disappear but rather remains latent over time.
Each new reference to the incident, whether in an online search, a due diligence process, or a business conversation, reignites feelings of vulnerability and distrust. For clients and partners, the memory of the attack often outweighs subsequent technical explanations. In this context, digital memory transforms a single event into a recurring reputational factor, capable of influencing hiring, investment, or collaboration decisions for years to come.
For this reason, incident management doesn’t end with technical recovery, but rather with the organization’s ability to reconstruct a coherent narrative, demonstrate real improvements in its security posture, and sustain communication over time that reinforces trust. Without an active strategy to address this digital memory, even a seemingly resolved incident can continue to erode the company’s reputation silently but steadily.
How to realistically reduce the risks of cloud storage
Reducing the risks of cloud storage doesn’t mean avoiding it, but rather governing it properly. The first step is knowing what data is stored, where it is located, and who has access to it. Without visibility, there is no security.
It is essential to implement strict access controls, multi-factor authentication, regular permission reviews, and continuous monitoring. These principles are outlined in specific standards such as ISO/IEC 27017, which defines security controls for cloud services.
Staff training remains crucial. Many incidents begin with phishing or human error, demonstrating that technology alone is insufficient without awareness.
Conclusion:
Storing data in the cloud is neither inherently secure nor insecure. Security depends on how risks are managed. Ignoring real-world vulnerabilities in cloud storage is one of the fastest ways to expose yourself to breaches, penalties, and reputational damage.The cloud doesn’t forgive improvisation. In an environment where data is the most valuable asset, protecting it is protecting the future of the business.
Frequently Asked Questions (FAQ)
Yes, but only when security is actively and continuously managed. The cloud offers robust infrastructure, but it doesn’t automatically protect data. Security depends on how the organization configures access, manages identities, applies encryption, and monitors the environment. Without proper governance, the risk can be even greater than in traditional environments.
Ultimate responsibility always rests with the company that owns the data. Even if the cloud provider protects the underlying infrastructure, the organization is responsible for the configuration, access, and use of the information. From a legal and reputational standpoint, a cloud breach does not absolve the company of its obligations or consequences.
Yes, and with increasing frequency. Many current attacks are specifically designed to exploit compromised cloud credentials, automatic synchronizations, and excessive permissions. Once inside, attackers can encrypt data, delete backups, and spread rapidly across interconnected services.
Not necessarily. Backups are a key measure, but they’re not a guarantee of security. If backups are connected to the primary environment or misconfigured, they can be encrypted or deleted during an attack. To be effective, they must be isolated, protected, and tested regularly.
Regulations such as GDPR apply regardless of where the data is stored. Using the cloud does not reduce legal obligations. Companies must report breaches, document incidents, and demonstrate adequate safeguards, even when data is hosted on third-party infrastructure.
The key is preparedness. Having strict access controls, continuous monitoring, staff training, and a well-defined response plan allows you to detect incidents earlier, contain them more quickly, and reduce both the operational and reputational impact.
Because cloud environments are highly flexible and complex. A seemingly minor error, such as an exposed bucket or an incorrectly assigned permission, can leave critical data publicly accessible. Many breaches are not due to sophisticated attacks, but to basic configuration errors that go unnoticed for months.
It’s one of the fundamental pillars. The cloud isn’t just accessed by employees, but also by applications, suppliers, and automated processes. Without a clear policy of least privilege, multi-factor authentication, and regular access reviews, credentials become the primary entry point for attackers.
Does the cloud increase reputational risk after a data breach?
Yes. Due to the interconnectedness of systems and the speed at which incidents spread, a cloud breach typically has greater visibility and reach. This can translate into a loss of trust, media pressure, and a more lasting reputational impact than in isolated environments.
Understanding that the cloud doesn’t eliminate responsibility. Cloud security requires governance, data visibility, robust technical controls, and a security culture. Organizations that treat the cloud as a strategic asset, not just a technology provider, are better prepared to prevent breaches and manage incidents when they occur.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.




