In 2025, a particularly disturbing threat emerged: Stealerium, an infostealer that doesn’t just steal credentials or banking data; its goal is to turn victims’ privacy into a tool for extortion. According to the academic database Malpedia, this malware is classified as win.stealerium and is characterized by stealing sensitive information and using it in digital sextortion campaigns.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
What is Stealerium and why is it alarming experts?
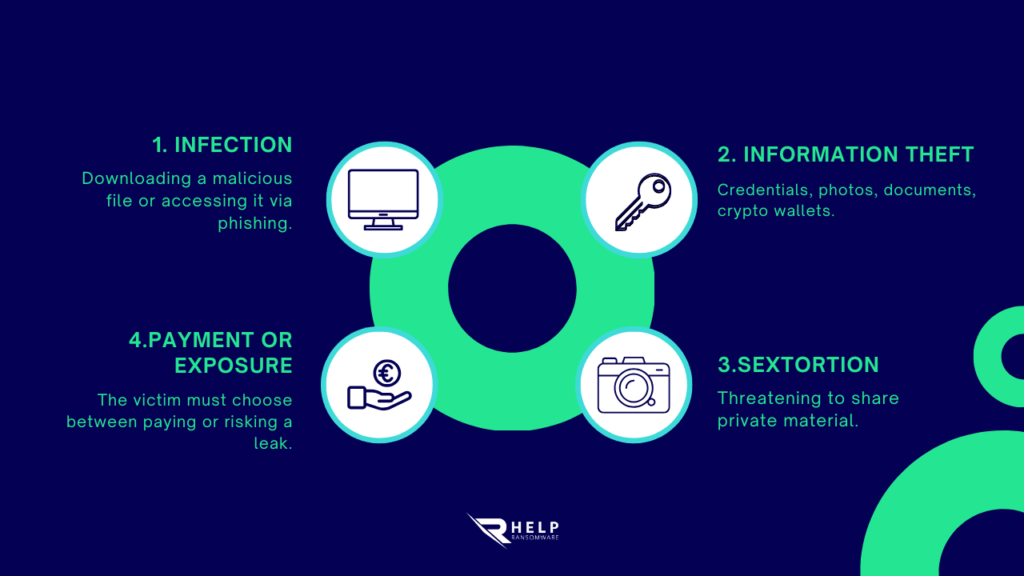
Stealerium belongs to the family of infostealers, programs designed to extract information from an infected device. However, what sets it apart—and makes it so dangerous—is its automated sextortion -oriented functionality :
- It detects browsing patterns (for example, on sites with adult content) and, without user intervention, can take screenshots and activate the webcam.
- It collects credentials, crypto wallet data, browsing history, and sensitive files.
- It centralizes that information and sends it to the attacker to use as blackmail : “Pay or I’ll publish these images and conversations.”
To put it in context, Stealerium is a type of Malware with typical infostealer features, but applied to emotional and reputational exploitation, not just traditional financial gain.
A scenario with real consequences: the law firm
Let’s imagine a medium-sized law firm: mobile staff, emails with sensitive documents, and access to confidential platforms. An employee unwittingly downloads a file that installs Stealerium. Within a few hours, the attacker has:
- Copies of internal emails and contracts.
- Photos and screenshots taken with the webcam during private sessions.
- Corporate services credentials.
The threat isn’t limited to data loss: blackmail aimed at exposing intimate material can lead to loss of customer trust, lawsuits for breaches of data protection regulations (GDPR), and reputational damage that takes years to heal.
This type of attack illustrates why it must be differentiated from the typical Ransomware: Here, emotional pressure is the attacker’s main tool.
How to respond and what measures to implement now
When dealing with Stealerium, an effective strategy combines technical controls, training, and clear response procedures. We recommend:
- Immediate forensic analysis and isolation of the device at the slightest suspicion.
- Eradicating the infostealer and blocking exfiltration channels.
- Review and rotation of credentials detected as compromised.
- Permission Policies : Restrict camera and microphone access by default.
- Training focused on delivery vectors such as phishing.
These measures are aligned with good practices for prevent a ransomware attack and also with recommendations for protect yourself from ransomware, as the entry mechanisms are often similar.
Expected results with an adequate response
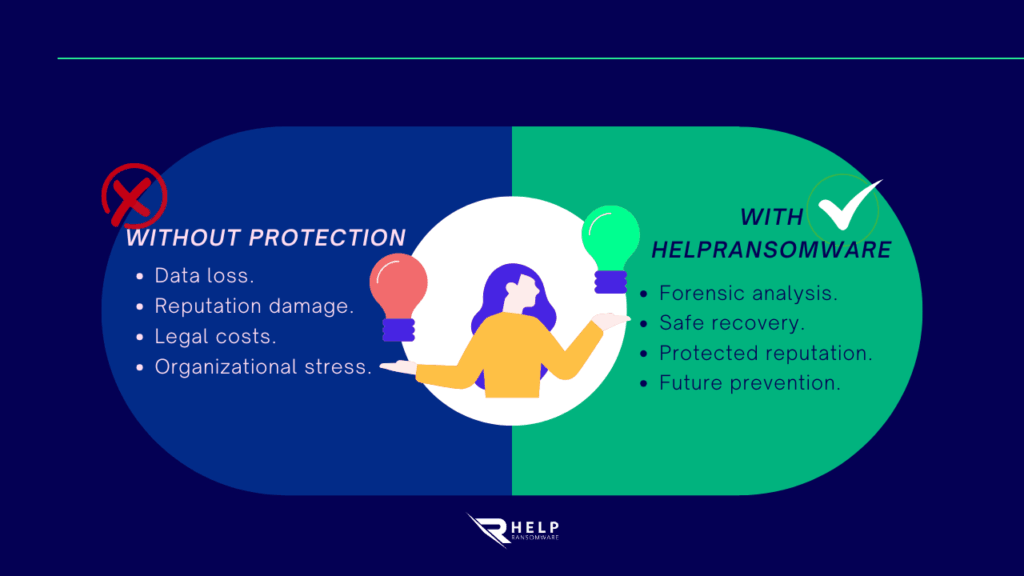
When detection and response are rapid and coordinated, the following are achieved:
- Contain exposure and minimize information that an attacker can exploit.
- Avoid payment and reduce the incentive for future blackmail.
- Mitigate reputational damage through appropriate crisis management.
- Strengthen organizational resilience through ongoing training and technical controls.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
In short: Prevention and immediate response make the difference between a one-time incident and a long-term crisis of confidence.
Final reflection
Stealerium confirms a clear trend: cybercrime explores emotional and reputational vectors in addition to economic ones. Protecting yourself today involves not only backups and antivirus software, but also strict privacy policies, hardware permission management, and awareness programs that reduce the likelihood of infection.



