
During the summer, many organizations operate with reduced staff, slower response times, and a reduced focus on cybersecurity. This combination is perfect for ransomware groups to launch highly effective, targeted attacks. In fact, the months of June through August account for a significant portion of global incidents, according to European and US organizations.
Cybercriminals don’t rest. On the contrary, they analyze the corporate calendar to detect breaches: an unapplied patch, a misconfigured VPN, or a weak password can be enough to encrypt all of a company’s critical information. With fewer technical staff available and a delayed response time, the damage escalates rapidly.
📌 An official document from ENISA—the European Union Agency for Cybersecurity—identifies summer holidays and long weekends as periods of increased digital risk. This is the National Cybersecurity Strategy 2020–2025, which recommends intensifying prevention measures during these periods.
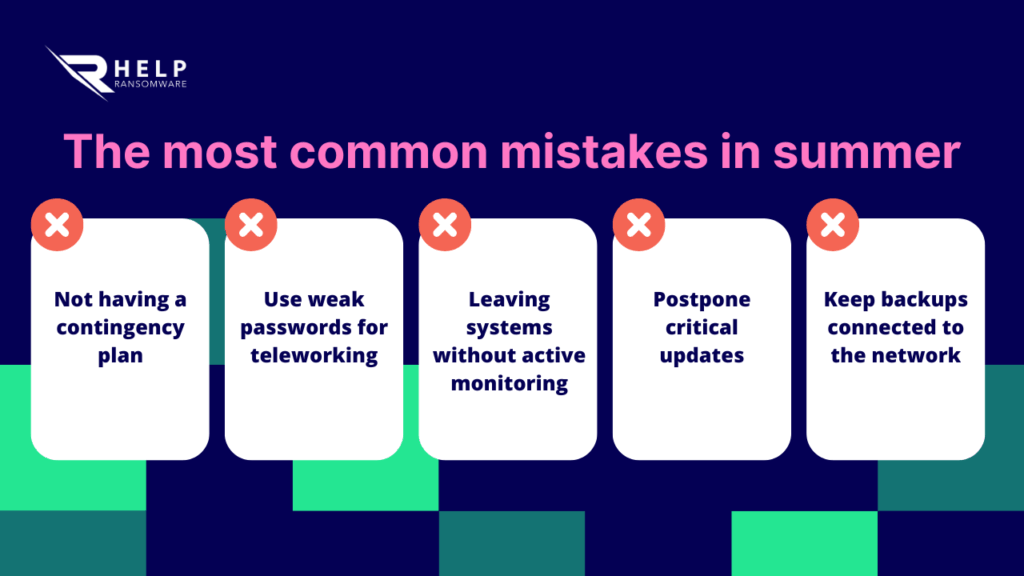
❌ The most common mistakes in the summer season

1. Not having a contingency plan for cyberattacks
Many companies don’t have a defined protocol in the event of an incident. This means that, in the event of a ransomware infection, employees don’t know who to contact, how to proceed, or which systems to isolate. Improvisation creates critical delays and often exacerbates the initial impact.
If you don’t have a documented and accessible plan, we recommend starting by defining your response path defense against ransomware.
2. Use weak passwords for teleworking
Teleworking increases during the summer, but so does insecure access. Many platforms are used with generic, repeated passwords, or passwords leaked in previous breaches. Brute-force attacks or credential stuffing exploit this oversight.
👉 Strengthen your environment by enabling multi-factor authentication and updating passwords before the holidays.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
3. Leaving systems without active monitoring
Some companies don’t assign personnel or external monitoring services during the summer. This means that an attack can be activated on a Friday afternoon and not be detected until the following Monday.
A silent attack can encrypt servers, databases, and even the network-attached backup files.
4. Not updating systems and software before the end of the cycle
Security updates are often postponed over the summer to avoid breaking anything. But cybercriminals know exactly which versions are vulnerable and where to look.
👉 Automate patches and review publicly available tools before the end of the quarter.
5. Store backups connected to the network
One of the most serious—and common—mistakes is leaving backups accessible from the internal network. Many ransomware attacks are designed to locate and encrypt these copies before displaying the ransom note.
A complete guide is recommended open encrypted files or contact an expert team in encrypted file recovery.
🧩 Conclusion: Summer should not be synonymous with vulnerability
The summer season represents a chance for relaxation for many people, but it’s also a time of peak activity for cybercriminals. The combination of less vigilance, human error, and outdated systems creates the perfect environment for ransomware to spread unchecked.
Companies that underestimate this risk expose themselves to serious consequences: data loss, operational disruption, reputational damage, and legal penalties, especially if they affect personal data or critical sectors.
The good news is that preventing a ransomware attack in the summer is possible. It just requires planning, automation, and conscious decisions. Don’t wait until you’re a victim to act.
🔐 If your organization doesn’t yet have an active prevention and response plan, now is the time.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.



