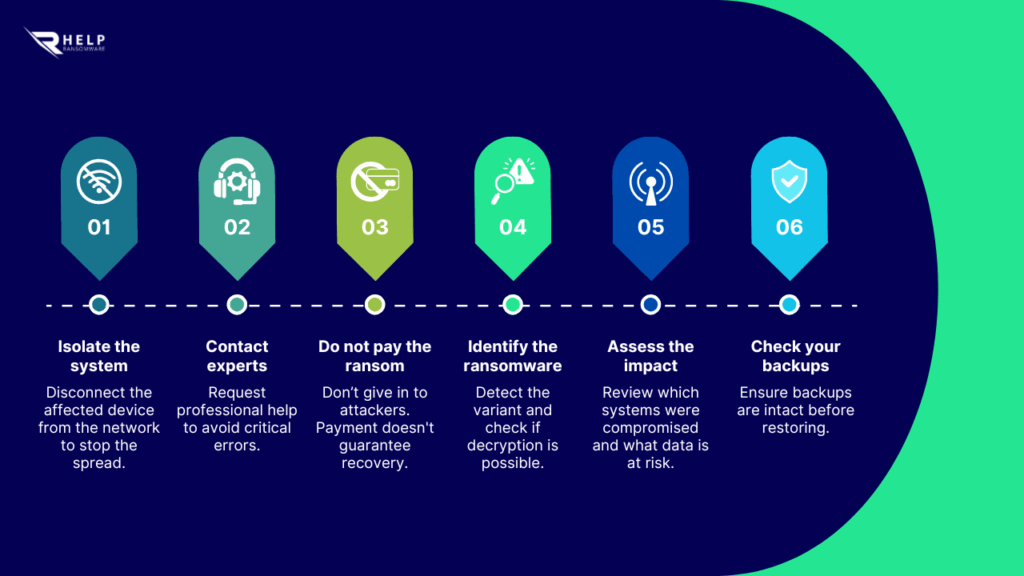
Being hit by a ransomware attack can completely paralyze your operations. Within minutes, your files are encrypted, your systems are locked, and a ransom note appears demanding payment. What should you do now? Acting quickly and strategically is key.
According to IBM Security, the average cost of a ransomware-related data breach reached $5.13 million in 2023—excluding any ransom payments. Long-term global ransomware losses could exceed $265 billion annually by 2031, according to estimates by Cybersecurity Ventures.
In many cases, a fast, well-guided response makes the difference between successful recovery and catastrophic losses.
This article provides an urgent checklist to follow if you’ve fallen victim to ransomware. It offers clear steps, practical tools, and links to expert resources. If you’re asking what to do after a ransomware attack, this guide will walk you through each phase—helping you contain the damage and recover your data safely.
1. Immediately Isolate the Infected System
The first step after detecting a ransomware attack is to stop its spread. Modern strains like LockBit or Ryuk can move across a network within minutes.
Why is isolation crucial?
Modern ransomware doesn’t just encrypt files on one device—it spreads using stolen credentials, shared access points, and active connections. The longer you wait to isolate the infected system, the more severe the damage: from critical database loss to full production system shutdowns.
Real case: In 2020, Sopra Steria suffered a Ryuk ransomware attack that disrupted operations for weeks, with losses estimated between €40–50 million. Even though they quickly contained the malware to part of their infrastructure, the incident shows how even a short delay in isolation can result in major economic and technical consequences.
What to do:
- Disconnect from the network: Turn off Wi-Fi or unplug the network cable from the infected machine. This can help prevent spread to servers, shared drives, and other devices.
- Block remote access: Disable tools like RDP (Remote Desktop Protocol) and terminate VPN sessions. Many ransomware strains exploit remote access vulnerabilities to propagate.
- Disconnect external and shared drives: Unplug hard drives, USBs, and shared folder connections. Ransomware typically encrypts anything connected or mounted.
- Avoid shutting down the system without expert guidance: Some strains like NotPetya delete decryption keys if a forced restart is detected. It’s safest to leave the device on, but fully isolated, for expert analysis.
Isolating the system promptly can be the difference between a contained incident and an operational disaster. This step must be done before any recovery or analysis attempt.
🔗 Learn more about how to manage a ransomware crisis.
2. Contact Ransomware Recovery Experts
After isolating the system, getting expert help is essential. Most companies are not equipped to handle ransomware attacks alone. Attempting to resolve the issue without technical knowledge can worsen the damage, erase key evidence, or permanently block your files.
What to do:
- Reach out to an expert recovery team: If your company lacks an internal protocol, it’s vital to contact professionals. HelpRansomware provides immediate assistance to analyze the attack, explore recovery options, and contain the damage—without paying the ransom.
- Avoid DIY actions without expert oversight: Don’t try to remove the ransomware, reboot the system, or manually restore files. Uninformed actions may complicate recovery or destroy forensic evidence.
- Request a professional diagnosis: HelpRansomware offers a free diagnosis service that evaluates your file status, identifies the ransomware strain, and explores possible decryption solutions.
3. Do NOT Pay the Ransom
When the ransom note demands cryptocurrency payment to restore your files, the pressure is intense. However, giving in to attackers is not a solution. HelpRansomware never recommends paying the ransom.
Why not pay?
- There’s no guarantee you’ll get your files back: Agencies like the FBI and Europol have warned that many victims never regain access to their data—even after payment. Cybercriminals are under no obligation to honor their word.
- It funds criminal networks: Ransom payments fuels organized criminal networks, including activities such as data trafficking, extortion, and new attacks on other victims.
- You could be breaking international laws: Some ransomware groups are linked to internationally sanctioned organizations. Making payments to these actors may constitute a violation of financial and security regulations, as warned by OFAC.
- It makes you a future target: Victims who pay are often attacked again, as they’re seen as likely to pay in future incidents.
What to do instead:
Request immediate support from a specialized team. HelpRansomware analyzes the type of ransomware, determines whether a decryption tool exists, and designs a secure strategy to recover your files without paying the ransom. If you don’t know how to respond to a ransomware attack, it’s important to have specialized technical support from the outset.
Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
4. Identify the Type of Ransomware
Before attempting any recovery, it’s essential to identify the ransomware variant that has affected your systems. Each ransomware family behaves in a specific way: some delete backups, others leak data before encrypting it, and many communicate with the attackers’ servers to receive instructions.
Why is this important?
Identifying the strain helps you:
- Determine if the case involves simple encryption or double extortion.
- Understand the full scope of the attack.
- Choose the right recovery approach.
📌 Some variants like STOP/Djvu, TeslaCrypt, or Shade have been partially neutralized by cybersecurity experts, and have public decryption keys.
What to do:
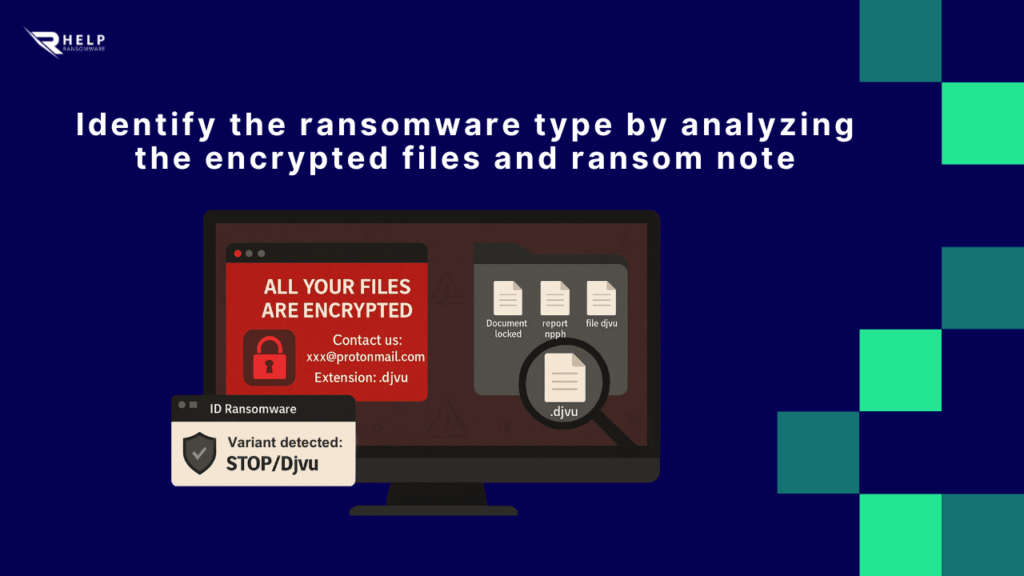
- Review the ransom note: This message often contains important clues, such as the name of the attacking group, email or TOR addresses, and payment instructions. Don’t respond or contact them directly, but save a copy for technical analysis.
- Note the extension of the encrypted files: Many variants change the extension of the affected files. For example, STOP/Djvu usually adds “.djvu” or “.rrcc,” while others such as LockBit or BlackCat use custom extensions.
- Consult with a specialized team: HelpRansomware analyzes samples from the infected system and tells you precisely which variant has attacked you, whether it’s known, or if it’s a more recent mutation.
- Avoid downloading tools from the Internet on your own: There are fraudulent sites that promise decryption solutions but actually distribute more malware. Only trust verified professionals.
🔗 See how HelpRansomware uses advanced ransomware decryption tools to classify and analyze attacks.
5. Assess the Scope of the Attack
Once the ransomware has been identified, you must determine the extent of the attack. This assessment allows you to know which systems have been compromised, what data is at risk, and how to organize an effective recovery without leaving the door open to new incidents.
Why is this step crucial?
Not all attacks have the same impact. Some encrypt only local files, while others affect multiple devices, critical servers, or even exfiltrate data before locking it. Without a proper assessment, you risk underestimating the impact and taking ineffective actions.
What to do:
- Make an inventory of compromised systems: Check which computers, servers, and devices have encrypted files or are exhibiting abnormal behavior. Include local computers, cloud servers, and shared network drives.
- Check if confidential information has been accessed or leaked: Many ransomware groups use double extortion tactics, threatening to publish stolen information if the ransom is not paid. Check logs, network traffic, or suspicious folders that indicate information extraction.
- Document the types of encrypted files: Identify whether the affected files include databases, accounting records, emails, customer files, among others. This classification is key to defining recovery priorities.
- Request a professional forensic analysis: HelpRansomware offers detailed analyses to assess the scope of the attack, detect malware persistence, and establish a customized response plan without compromising further assets.
🔗 Learn how to implement effective business data protection strategies to safeguard your most critical information.
6. Review and Protect Your Backups
Backups are your best defense against ransomware, but only if they have been managed correctly. Many criminal groups design their attacks to detect, encrypt, or delete backups before launching mass encryption, especially if they are stored on the same network or without isolation.
Why not restore backups immediately?
Many ransomware groups deliberately attack backups: they encrypt them, delete them, or leave infected files that can reactivate the malware after restoration. Some variants even remain dormant to run again when they detect a mass restoration.
What to do:
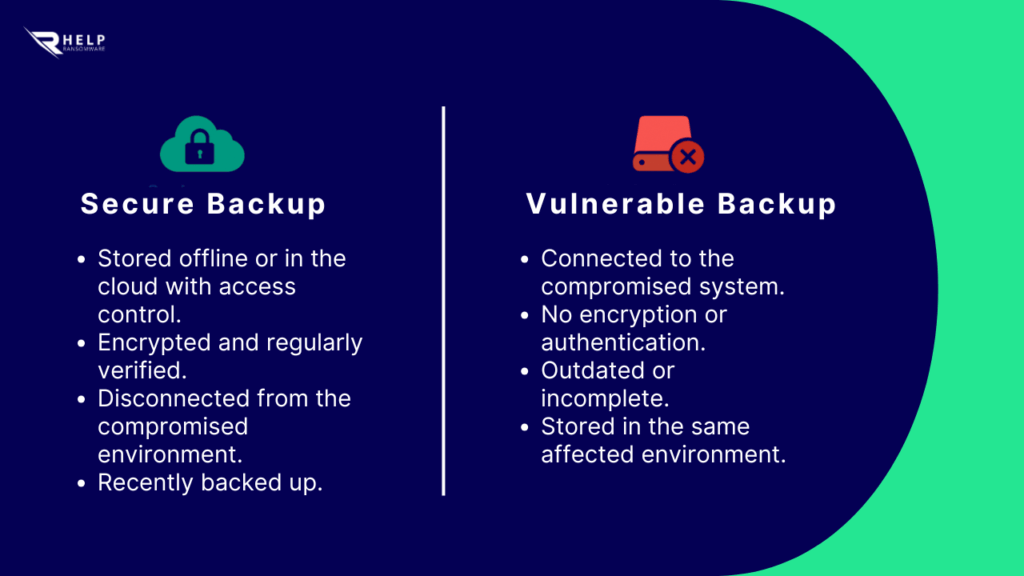
- Verify that your backups are intact: Check that the copies have not been encrypted by ransomware and that they are not connected to compromised systems. Pay special attention to backups stored on NAS servers, connected disks, or network folders.
- Check the date and integrity of the backup: Make sure the copy was created before the attack and that it includes all the critical information needed to resume operations. An outdated backup can delay recovery by weeks.
- Don’t restore directly to the compromised environment: The system must be analyzed and cleaned before any restoration is performed. Restoring to a contaminated environment will only perpetuate the threat.
- Consult with experts before restoring: HelpRansomware can validate the integrity of your copies and help you restore them safely, ensuring that the environment is free of persistent threats.
🔗 Discover how HelpRansomware helps you recover encrypted files.
Conclusion
A ransomware attack may seem like the end of your digital infrastructure, but with a quick and well-guided response, it’s possible to contain the damage and regain control without giving in to blackmail.
These six steps—from isolating the system to reviewing backups—should be followed in order, with professional support. At HelpRansomware, we’ve helped companies of all sizes recover files, protect systems, and avoid ransom payments—always legally and safely.
If you’ve been hit by ransomware or suspect your systems have been compromised, don’t wait. Every minute matters when it comes to limiting impact, safeguarding data, and avoiding operational collapse.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.




