Understanding how to identify a ransomware attack before encryption takes place has become a strategic capability for business continuity. This is not only about deploying technical tools, but about understanding attacker behavior, interpreting early warning signs, and acting while there is still room to respond. In this context, early detection is the difference between a manageable disruption and a full-scale operational, legal, and reputational crisis.
Many organizations still associate ransomware with visible symptoms such as locked screens or inaccessible files. In reality, by the time these indicators appear, the attack has already reached its final stage. The real challenge lies in recognizing the signals that emerge much earlier, when attackers are already inside the network but have not yet executed the final payload.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.
In recent years, ransomware has evolved from a sudden and visible event into a silent, prolonged, and highly structured operation, driven by different attack vectors and entry points, with phishing remaining one of the most common initial access methods. Far from the scenarios in which an organization suddenly wakes up to encrypted systems overnight, modern ransomware attacks unfold over time, progressively advancing inside the network without triggering obvious alerts until the damage becomes critical.
Why most ransomware attacks do not start with encryption
One of the most common mistakes in cyber-risk management is assuming that ransomware begins when systems stop working. In reality, that moment represents the end of a long intrusion chain that often started weeks or even months earlier. Encryption is merely the final step of a broader process designed to maximize impact and minimize the victim’s ability to react.
Modern attacks follow a well-defined sequence: initial access through phishing, stolen credentials, or exploited vulnerabilities; lateral movement to expand control within the network; privilege escalation; sensitive data exfiltration; environment preparation; and, ultimately, ransomware execution. Each of these phases leaves technical and operational traces that, while not immediately disrupting business operations, clearly indicate an active intrusion, as described in the Computer Security Incident Handling Guide published in 2025 by NIST, where ransomware is defined as the final outcome of incidents that evolve over time rather than as a sudden event.
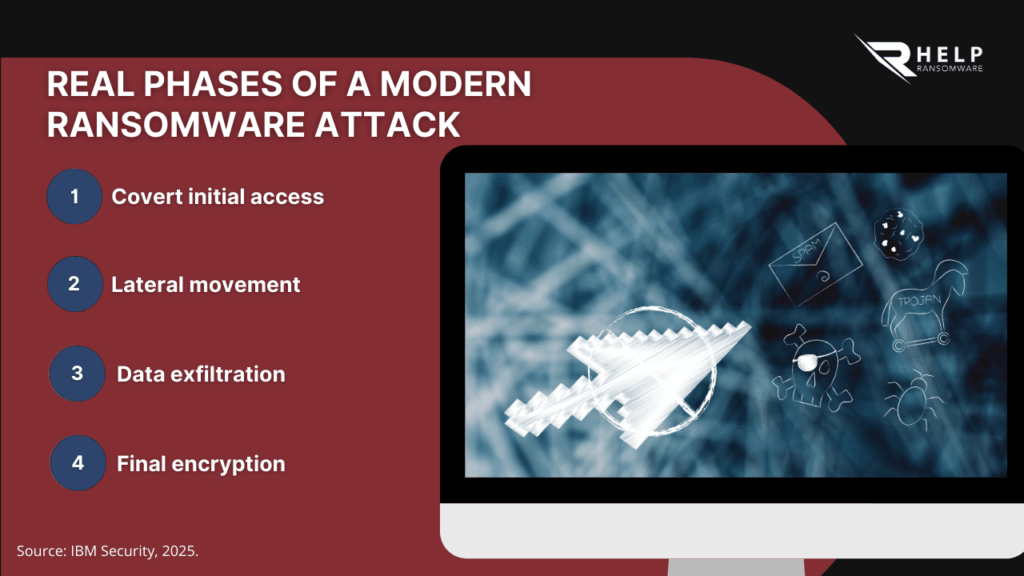
Early signs that ransomware is already inside your network
Identifying ransomware in its early stages requires a shift in perspective. Rather than looking for obvious incidents, organizations must monitor anomalous behaviors and persistent deviations from normal operations. When viewed in isolation, these signals may seem insignificant; when correlated, they reveal an ongoing intrusion.
One of the earliest indicators is often an increase in failed authentication attempts, especially outside business hours or from unusual geographic locations. This pattern is commonly associated with brute-force attempts or the use of previously compromised credentials. When such activity results in successful logins from unfamiliar devices, the level of risk increases significantly.
It is also common to detect misuse of legitimate credentials. Attackers prefer to move laterally using real user accounts to avoid triggering automated alerts. Administrative access from standard accounts, unjustified permission changes, or activities inconsistent with a user’s role are clear indicators of internal compromise.
At this stage, having dedicated ransomware solutions focused on behavioral monitoring and threat correlation becomes critical to distinguish isolated anomalies from a coordinated attack.
Anomalous activity as the first indicator of compromise
When ransomware infiltrates a network, its presence is rarely immediate or noisy. Instead, it typically manifests through progressive deviations in the normal behavior of systems and users. Unknown processes running with elevated privileges, scheduled tasks without operational justification, or simultaneous logins from different geographic locations are clear signs that the environment has been compromised.
These behaviors are particularly relevant when they affect peripheral systems or secondary servers, which often receive less attention than critical assets. However, it is precisely in these environments that attackers tend to establish persistence and prepare lateral movement toward more sensitive systems, as highlighted by the UK National Cyber Security Centre (NCSC) in its guidance updated in 2025 on detecting malicious activity prior to ransomware attacks.
Data exfiltration: the most overlooked signal of modern ransomware
One of the most significant changes in ransomware evolution is the widespread adoption of double extortion. Before encrypting systems, attackers steal sensitive data to increase pressure on the victim, even when backups are available. This phase often goes unnoticed because it does not immediately disrupt business operations.
Indicators of exfiltration include abnormal outbound traffic spikes, large-scale file compression on internal servers, and persistent encrypted connections to unfamiliar external destinations. When these signals appear, the attack has already progressed significantly and the potential impact increases exponentially.
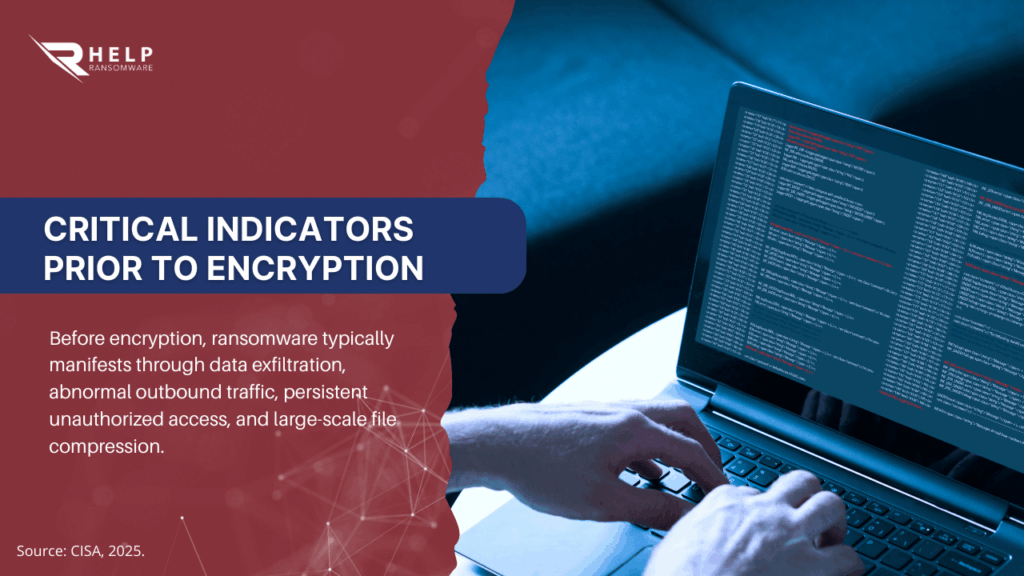
When the impact is no longer purely technical
Data exfiltration turns a technical incident into a business crisis. The loss of sensitive information undermines trust among customers, partners, and stakeholders, while exposing the organization to regulatory penalties and legal action. As a result, ransomware impact extends far beyond system recovery.
Silent changes to systems and backups
Another particularly dangerous signal is the deliberate manipulation of backup systems. Before triggering encryption, many attackers attempt to disable recovery options by deleting backups, altering retention policies, or shutting down recovery services.
The #StopRansomware Guide published by CISA in 2025 emphasizes that protecting, segmenting, and continuously monitoring backups is one of the most effective ways to reduce the final impact of a ransomware incident.
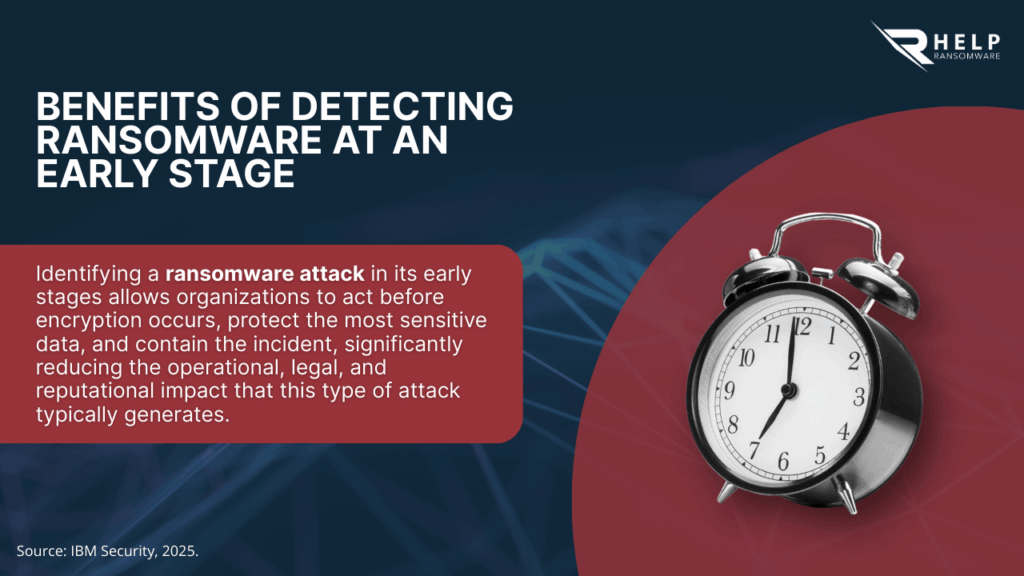
Why early detection completely changes the outcome
Detecting ransomware before encryption allows organizations to isolate compromised systems, revoke access, and activate incident response plans while containment is still possible. At this stage, ransomware data recovery strategies and forensic readiness play a decisive role in limiting damage and preserving business continuity.
Conclusion
Ransomware does not appear out of nowhere. It always leaves traces before encryption occurs. The real risk is not the absence of warning signs, but the failure to recognize them in time.Learning how to identify a ransomware attack means accepting that security begins long before systems fail. Organizations that understand this reality stop reacting too late and start anticipating threats, significantly reducing the impact of one of today’s most critical digital risks.
Frequently Asked Questions (FAQ)
Early signs are often subtle and include unusual access patterns, abnormal use of legitimate credentials, unauthorized configuration changes, and network traffic that deviates from normal behavior, even when systems appear to function correctly.
Yes. Most modern ransomware attacks exhibit detectable indicators prior to encryption. The challenge lies in having sufficient visibility and the ability to correlate events effectively.
Early indicators usually appear on peripheral systems, secondary servers, and authentication logs rather than on critical production systems.
Data exfiltration enables double extortion, increasing pressure even if the organization can restore systems from backups.
Not always. Many attacks involve disabling or destroying backups before encryption, making isolation and continuous monitoring essential.
Dwell time can range from days to several months, particularly in complex organizations where attackers aim to maximize impact.
It remains critical. Many attacks begin with social engineering, and trained staff can identify suspicious behavior before the attack escalates.
Yes. With basic controls, proper monitoring, and clear response procedures, SMBs can detect meaningful intrusion patterns.
Not always, but it significantly reduces operational, legal, and reputational impact.
Waiting for obvious signs such as file encryption. When those appear, the attack has already succeeded.



