Over the past decade, cybersecurity has evolved from a technical function into a strategic pillar of corporate governance. In 2026, this transformation will fully consolidate. Organizations no longer operate in isolated digital environments, but in interconnected ecosystems where suppliers, customers, cloud platforms, and critical infrastructure share complex dependencies.
Cybersecurity trends in 2026 do not simply indicate an increase in attacks. They signal a structural shift in the nature of risk. Offensive automation, generative artificial intelligence, and hyperconnectivity will redefine both the speed and scale of threats. Risk will no longer be a single disruptive event, but a continuous and adaptive phenomenon that evolves in real time.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
The Global Cybersecurity Outlook 2026 – World Economic Forum identifies offensive AI, advanced ransomware, and supply chain attacks as the primary areas of concern for business leaders and security executives.
Offensive artificial intelligence will become the most influential catalyst in 2026. Attackers will be able to generate highly personalized phishing campaigns in seconds, automatically analyze exposed infrastructures, and dynamically adjust tactics based on defensive responses. This significantly reduces detection windows and increases the probability of initial compromise.
In 2026, a ransomware incident will no longer be an isolated disruption. It will represent the final stage of a coordinated chain that includes reconnaissance, privilege escalation, and data exfiltration. Organizations must therefore move beyond reactive models and invest in structured ransomware defense strategies capable of containing incidents before escalation.
Speed as the New Critical Factor
The defining change in 2026 will be speed. Automation will compress the time between initial intrusion and final execution to minutes or hours. Organizations relying solely on manual review processes or reactive workflows will remain exposed in a threat environment that operates at machine scale.

Speed directly influences executive decision-making. When incidents unfold in minutes, leadership must act under pressure, often with incomplete information. The difference between containment and systemic crisis depends on predefined protocols, clear authority lines, and rehearsed escalation procedures.
The 2025 Cybersecurity Report by the Inter-American Development Bank and the OAS highlights persistent gaps in institutional maturity, increasing vulnerability to automated and coordinated attacks.
In environments where digital governance is not fully embedded in corporate strategy, attacker speed surpasses organizational response capacity.
Reaction Time vs. Impact Time
In 2026, detection alone will not be sufficient. What truly matters is effective reaction time. Identifying an intrusion does not guarantee containment if internal structures delay execution. Fragmented accountability, lack of crisis simulations, and undefined decision authority amplify damage.
Modern attacks combine automation, exfiltration, media pressure, and regulatory implications almost simultaneously. Without strong leadership alignment, the speed of the incident exceeds the speed of the organization. Preparation therefore means more than deploying technology. It means accelerating internal coordination, reducing operational friction, and strengthening cross-functional alignment between technical, legal, and executive teams.
The impact, moreover, will no longer be exclusively technical.
The regulatory environment will intensify. Accelerated reporting requirements and increased accountability will reshape executive priorities, forcing organizations to align cybersecurity governance with board-level oversight and compliance frameworks. Regulatory scrutiny will no longer be reactive but continuous, demanding greater transparency, documented risk management processes, and demonstrable incident readiness.
Digital reputation in 2026 will be as vulnerable as any IT system. A breach can erode stakeholder confidence within hours, impacting investors, customers, partners, and regulators simultaneously. In an era of instant information flow and amplified media exposure, the narrative surrounding an incident may spread faster than the technical containment itself. As a result, organizations must integrate reputation risk management, crisis communication strategies, and regulatory preparedness into their cybersecurity posture, recognizing that trust has become one of their most critical and fragile assets.
Governance, Leadership, and Resilience
Cybersecurity in 2026 will require direct executive involvement. Effective ransomware defense and structured ransomware recovery strategies can no longer remain purely technical responsibilities. Boards must integrate digital risk into strategic planning frameworks.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.
As Andrea Baggio, CEO of HelpRansomware, states:
“The difference in 2026 will not lie in who has more technology, but in who is prepared to act quickly and decisively when the attack is already underway.”
Resilience will become the new maturity benchmark. It will measure not only prevention capability, but the ability to adapt, contain, and recover rapidly while preserving operational continuity and stakeholder trust. Organizations will be evaluated on how effectively they respond under pressure, how quickly they restore critical systems, and how transparently they communicate during crises. In this evolving threat landscape, success will depend on early detection, coordinated response frameworks, and executive-level oversight rather than on perimeter defenses alone.
Cyber maturity will increasingly reflect an organization’s capacity to learn from incidents, strengthen internal controls, and transform disruption into long-term strategic improvement.
Digital supply chains remain a structural vulnerability. A compromised provider can create simultaneous disruption across multiple entities. Technological interdependence amplifies systemic exposure. Investing solely in ransomware recovery will not be sufficient without segmentation, third-party auditing, and regular crisis simulations.
Executive Accountability and a Culture of Anticipation
Leadership engagement must go beyond oversight. Boards should regularly assess digital exposure, review resilience metrics, and demand realistic scenario testing. Resilience combines technical preparedness, strategic clarity, and organizational training. Advanced tools alone are insufficient if crisis response has never been rehearsed.
As interdependence grows, broader visibility into third-party ecosystems becomes essential. Effective access segmentation and supplier monitoring reduce propagation risk. In an environment where digital trust can erode rapidly, strong governance becomes the primary stabilizing force.
Conclusion
Cybersecurity trends in 2026 point to a year defined by offensive automation, evolving ransomware, and regulatory acceleration. Risk will shift toward speed, governance, and organizational resilience. Strategic anticipation will be the key differentiator. Organizations that embed cybersecurity into their business model will be better positioned to operate in a landscape where threats not only grow — they learn and adapt.
Frequently Asked Questions (FAQ)
They are characterized by offensive automation, evolving ransomware models, AI-driven attack capabilities, and increasing regulatory and geopolitical pressure shaping organizational risk.
AI enables attackers to automate reconnaissance, personalize phishing campaigns, and scale operations rapidly, dramatically reducing detection windows and increasing efficiency.
Yes. Ransomware will continue evolving into hybrid models combining encryption, data exfiltration, reputational leverage, and regulatory pressure.
Speed is critical. The gap between intrusion and impact is shrinking, meaning executive-level decisions must occur within minutes rather than days.
Because effective cybersecurity in 2026 requires board-level accountability, structured decision authority, and integration of digital risk into overall corporate strategy.
Yes. Increased technological interdependence means a compromised vendor can impact multiple organizations simultaneously.
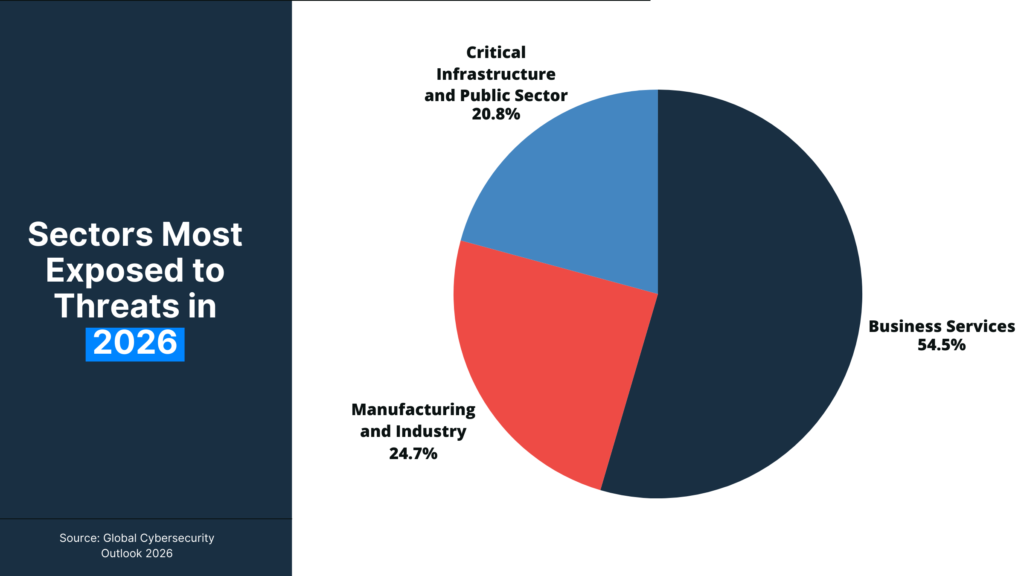
Business services, manufacturing, and critical infrastructure show the highest exposure due to digital dependency and operational criticality.
No. However, risk can be significantly reduced through proactive governance, resilience planning, and structured ransomware defense and recovery frameworks.
Recovery must be complemented by prevention, segmentation, third-party oversight, and crisis simulations to avoid systemic escalation.
They should strengthen governance structures, rehearse crisis scenarios, enhance detection speed, and integrate cybersecurity into strategic decision-making.

Fast & Guaranteed Recovery
HelpRansomware provides a 100% guaranteed ransomware removal and data recovery service, with 24/7 worldwide assistance.



