For many years, companies considered data a secondary resource—information useful for improving processes, optimizing sales, or meeting legal requirements. Today, that view is completely outdated. In the current landscape, data no longer supports the business: it sustains it.
Customers, suppliers, operations, billing, logistics, innovation, reputation, and regulatory compliance depend directly on the information a company manages and protects. When that data is lost, leaked, or encrypted, the impact goes far beyond a technical failure: business continuity is put at risk.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
Ransomware attacks, information leaks, and cyber-crime have proven that a company can still have offices, employees, and systems… and yet become completely paralyzed if it loses control of its data. That is why discussing the importance of protecting data is directly discussing business survival.
Data as the Backbone of Modern Business
In the digital economy, data connects every area of an organization. It is the invisible thread that allows processes to function, decisions to be made effectively, and customers to trust the company. When that thread breaks, the impact is immediate and profound.
The dependency on systems and access to information
Today, even a partial interruption of access to information can halt a company’s activity for days. The reason is simple: data is the convergence point of all systems. It doesn’t matter how many servers a company owns if encrypted data prevents access to critical information.
Furthermore, data represents not only internal value but also external trust. Customers, partners, and investors evaluate companies based on their ability to protect the information they handle. A data breach is not perceived as a technical glitch—it is seen as a failure of responsibility.
Ransomware Has Turned Data Into a Weapon of Extortion
This strategy, known as double-extortion ransomware, has deeply transformed the dynamics of modern attacks. The FBI, through its Internet Crime Complaint Center (IC3) Annual Report 2024, warns that in an increasing number of incidents, attackers exfiltrate sensitive data before encrypting systems, later using that information as additional leverage.
The IC3 report highlights that even when organizations successfully restore operations or recover encrypted files, the risk persists if the data has been stolen, as it may be sold, leaked, or reused in future attacks. In this context, paying a ransom does not restore control over the information nor eliminate the threat—it becomes a high-risk decision that extends legal, operational, and reputational consequences.

What Data Cybercriminals Seek and Why It Is So Dangerous
Attackers do not act at random. They seek information that enables them to apply real pressure on the victim. Financial data enables fraud; personal data enables extortion; intellectual property destroys competitive advantage; and access credentials open the door to new attacks.
The chain reaction after a data breach
Once stolen, this data can be reused for months—or even years. In many cases, it fuels phishing campaigns and new ransomware attacks, expanding the impact of the initial incident and affecting customers, employees, and suppliers.
This chain reaction explains why a single breach can unleash a crisis far greater than initially anticipated.
When Data Is Lost, the Real Crisis Begins
Many organizations believe the problem ends when systems are restored. Experience shows the opposite. Data loss often marks the beginning of a prolonged crisis, not its end. From that point on, the company must face legal notifications, regulatory investigations, market distrust, and public exposure that may last for months.
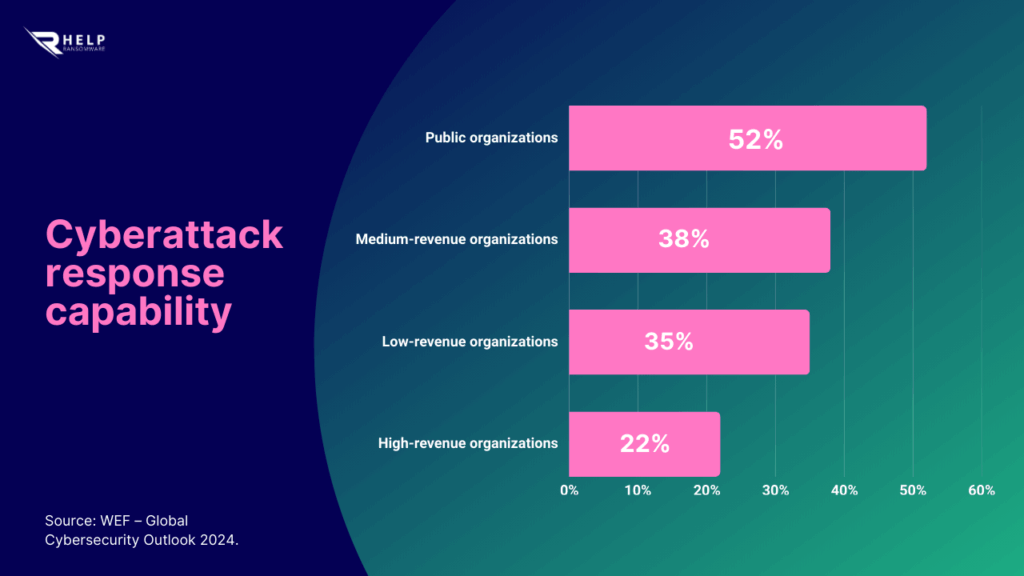
This reality is directly linked to the reputational impact of cyber-incidents. According to the World Economic Forum’s “Global Cybersecurity Outlook 2024”, more than half of surveyed organizations recognize that cybersecurity incidents directly and lastingly affect the trust of customers, partners, and investors—even after the technical issue is resolved.
The report emphasizes that operational recovery does not equal reputational recovery, and that damage to corporate credibility is often the most persistent consequence of a data breach.
Protecting Data Is No Longer Optional: It Is a Legal and Strategic Obligation
Modern regulations have elevated the level of requirements and transformed how companies must approach information protection. Frameworks such as GDPR and NIS2 no longer focus solely on reactive measures—they require organizations to identify, classify, and actively protect data as strategic business assets.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
Governance, risk, and organizational responsibility
The National Institute of Standards and Technology (NIST) states in its publication “Identifying and Protecting Assets and Data Against Cyber Threats” that most organizations lack precise knowledge of what critical data they hold, where it is stored, and what impact its loss would have—factors that exponentially increase the risk of targeted attacks.
The document stresses that you cannot protect what you have not identified, and that effective data protection must be approached as a continuous process involving asset inventory, access controls, risk management, and organizational governance.
Failing to meet these obligations results not only in financial penalties but also in a loss of credibility that may directly affect business viability.
The Human Factor: The Silent Origin of Most Breaches
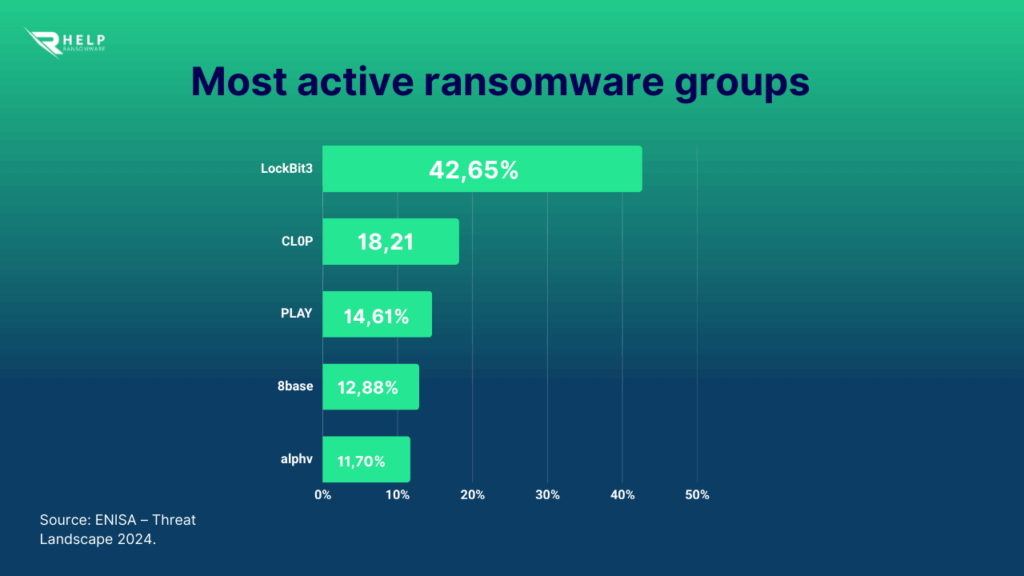
Despite technological advances, human error continues to be one of the main entry points for ransomware attacks—even in organizations with advanced infrastructures. The most active global ransomware groups target sectors such as industry, manufacturing, retail, and digital service providers, where operational complexity and pressure to maintain continuity make a single human mistake highly consequential.
Phishing emails, malicious links, and poor security practices remain common triggers that escalate into system encryption and data exfiltration. In this context, technology alone is not enough: without continuous training and a strong culture of cybersecurity awareness, organizations become vulnerable targets.
Employee training has therefore become a fundamental pillar to reduce attack effectiveness and protect critical business data.
Data Protection as a Strategy for Business Survival
Discussing the importance of data protection is discussing business continuity. Companies that adopt a preventive approach do not eliminate risk, but they drastically reduce its impact when an incident occurs.
This requires identifying critical information, limiting access, applying appropriate encryption, and having a clear cyber-incident response plan. The goal is not to prevent every attack, but to ensure that the business does not collapse when one occurs.
Conclusion: Protecting Data Is Protecting the Company’s Future
Data is now the asset that sustains a company’s operations, reputation, and viability. When it is lost or compromised, the damage rarely remains confined to the technical domain.
Organizations that understand this do not wait for an incident to act. They invest in prevention, training, and response strategies, knowing that the cost of not protecting data is always higher than the cost of doing it right. In a landscape where ransomware and digital extortion continue to rise, protecting data is not a competitive advantage—it is a basic condition for survival.
Frequently Asked Questions (FAQ)
Data protection is no longer a purely technical issue delegated to IT. Today, data carries financial, reputational, and legal value, and its loss directly affects business continuity and leadership accountability.
Boards and executive committees now understand that a data incident can lead to customer loss, brand erosion, regulatory sanctions, and litigation. Therefore, data protection is a strategic governance decision, not just a cybersecurity measure.
Losing systems is usually temporary: they can be restored, replaced, or rebuilt. Losing data is permanent—once information leaves the company’s control, there is no real way to “recover exclusivity” over it. In modern ransomware attacks, even when systems are restored, stolen data may continue circulating, being sold or used for further extortion.
Modern ransomware does not rely solely on encrypting files. Its true power lies in the prior exfiltration of data and the threat of publicly releasing it. Even if a company restores its systems, the damage remains if sensitive data has been stolen. This is why authorities strongly discourage ransom payment—it does not eliminate the risk.
The most impactful data includes personal information, financial data, health information, contractual documentation, and intellectual property. Exposure triggers legal obligations and leads to immediate loss of trust, often exceeding the direct financial impact.
Backups are essential, but they do not prevent data theft. In advanced attacks, data is copied before encryption, meaning backups only restore operations—they do not prevent leaks. Many ransomware variants also encrypt or delete connected backups, creating a false sense of security if relying on backups alone.
Human error remains the main cause of data breaches. Phishing, weak passwords, and configuration mistakes allow attackers easy access without exploiting complex vulnerabilities. Therefore, data protection must include training, awareness, and a strong security culture, not just technology.
Business continuity depends on data availability, integrity, and confidentiality. When data is compromised, the company loses operational capacity, market credibility, and crisis-response capability. Protecting data ensures that the organization can keep operating even during an attack.

Expert Ransomware Removal
Our certified professionals have over 25 years of experience in ransomware removal, data recovery, and computer security.