A new operational scenario for criminal groups
CISA ‘s guidelines on protecting critical infrastructure from drone threats marks a strategic turning point. It is not merely a technical document, but a direct warning about how malicious actors are expanding their tactical reach beyond the digital perimeter.
The full guide can be found at “ CISA releases new guides to safeguard critical infrastructure from unmanned aircraft systems threats ” :
From a ransomware expert’s perspective, this report confirms a logical evolution: criminal groups—especially the most sophisticated ones—no longer rely solely on digital intrusions. Drones allow for physical reconnaissance, the study of operational patterns, and the detection of vulnerabilities that are then exploited in multi-vector attacks, as we have already seen in incidents of ransomware on airlines.
What really worries CISA
The hybridization of physical and digital threats
CISA guidelines do not simply list technical risks. They describe how unmanned aerial vehicles (UAVs) allow for the capture of critical operational information: the location of surveillance cameras, blind spots, internal routes, restricted access points, antenna deployment, and personnel behavior.
In the hands of a sophisticated ransomware group, each of these elements can become a link in a chain of attack. Actors already operating at a large scale—such as major ransomware groups targeting critical infrastructure—are increasingly combining physical and digital intelligence, something that has also been seen in cases of ransomware in the healthcare sector where operational pressure is a key factor in extortion.
How does CISA’s strategy connect with ransomware?
Defense in reconnaissance, not just intrusion
CISA proposes a defense framework based on three pillars:
- Identification of exposed assets from the air.
- Implementation of drone detection technologies.
- Coordinated response with security forces and agencies.
From a ransomware perspective, this has a clear interpretation: whoever controls aerial visibility controls the most critical reconnaissance phase of the attack. An organization that fails to detect a drone conducting surveillance will likely also fail to detect an advanced digital intrusion in time.
This pattern has been observed in complex incidents such as the ransomware attack on Puma, where internal reaction times made the difference between a serious incident and a major catastrophe.
Implications for modern corporate security
From digital extortion to hybrid attacks
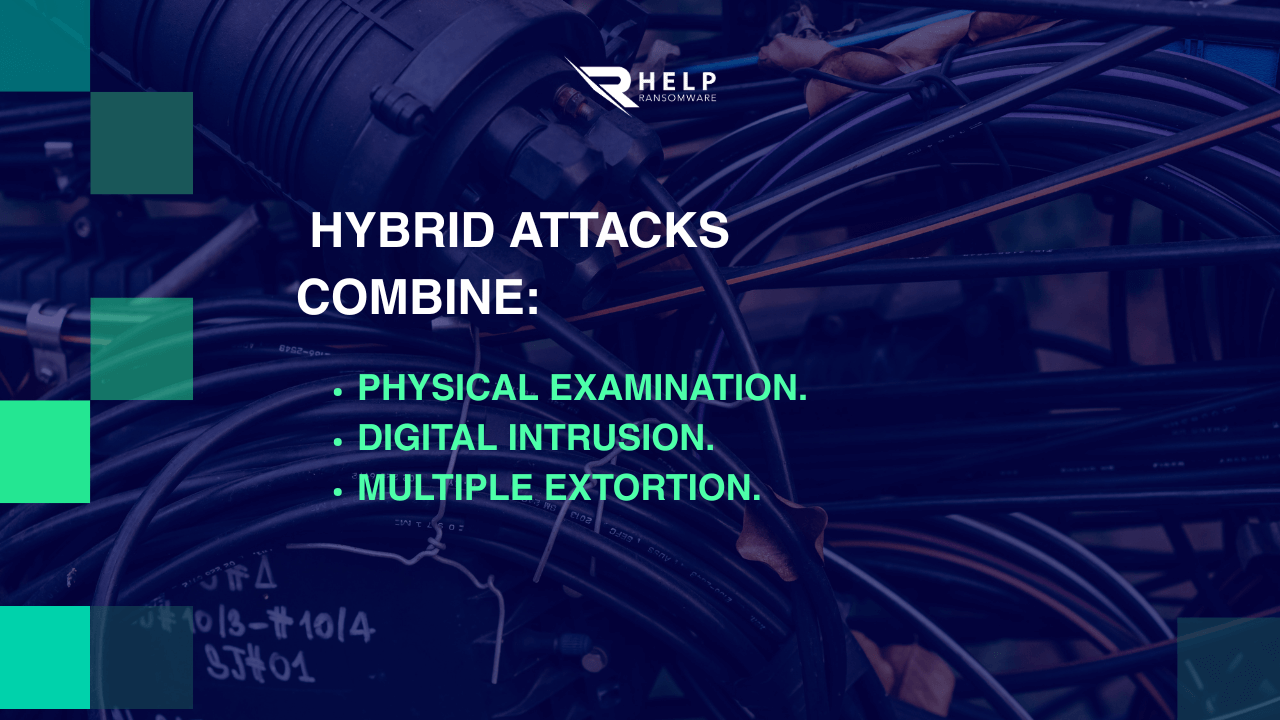
CISA’s recommendations should be read as a strategic warning: hybrid attacks are already a reality. A drone can map the physical layout of an industrial plant, identify poorly protected critical equipment, and observe staff routines. All that intelligence can fuel intrusion campaigns, lateral movement, and extortion.
This approach fits with what we are already seeing in campaigns of Sextortion and ransomware, where attackers combine different levels of pressure—psychological, operational, economic, and reputational—to force ransom payments. The drone becomes yet another tool in this chain of pressure.
Strategic recommendations from a ransomware perspective
What should organizations do now?
From a ransomware and cyber extortion perspective, organizations that manage critical infrastructure or sensitive services should:
- Conduct regular aerial and physical exposure audits to understand what a drone “sees” about your facilities.
- Integrate UAS (Unmanned Aircraft Systems) detection systems into your security operations centers, correlating physical and digital events.
- Include drone scenarios in your incident management plans and drills, just as you do with cyberattacks.
- Evaluate what information obtained from the air could facilitate intrusion, encryption, and extortion attacks.
- Adopt a defense-in-depth model, similar to that recommended for stopping advanced threats such as LockBit 3.0.
- Unifying physical and logical protection within comprehensive frameworks ransomware crisis, where the focus is on business continuity and resilience.
The underlying message is clear: the same adversaries who exploit vulnerabilities in VPNs, RDP, or exposed applications can use a drone to prepare the ground and increase their success rate.
Conclusion
The new CISA guidelines are not just another document, but a sign of how the cybercrime and ransomware ecosystem is evolving. Drones allow for an expanded attack surface, improved reconnaissance, and open the door to more coordinated and stealthy extortion operations.
For any organization that takes the ransomware threat seriously, ignoring this vector would be a strategic mistake. Integrating UAS defense into the overall cyber resilience strategy is no longer an advanced option: it’s a basic requirement.
HelpRansomware supports companies and institutions in adapting to this new scenario, helping them anticipate hybrid threats, strengthen their defenses, and reduce the impact of the most sophisticated attacks.



