When a company or public agency faces a locked screen and a Bitcoin ransom note, panic is the natural reaction. Operations stop, clients complain, reputation collapses — and a crucial question emerges: to pay or not to pay?
According to the IBM Cost of a Data Breach Report 2024, 37% of organizations hit by ransomware have paid at least once, yet only 45% fully recovered their data. In many cases, the decryption key didn’t work or caused new system failures.
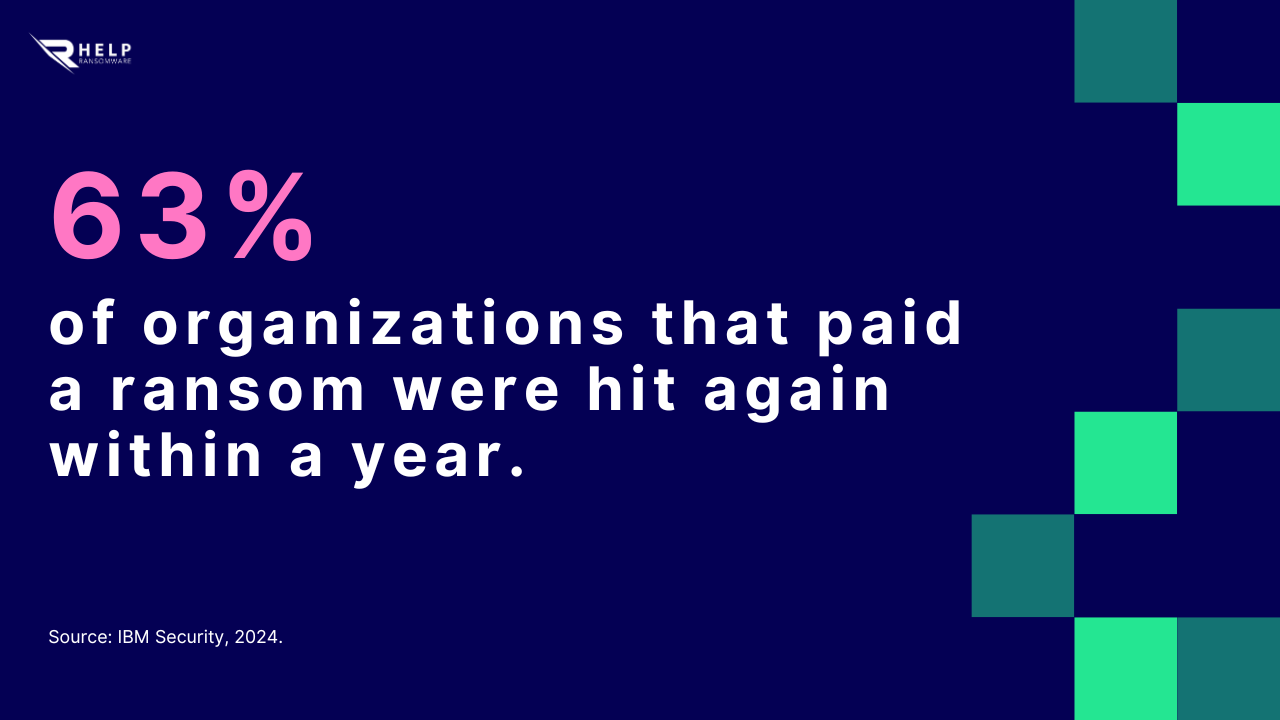
This dilemma is not merely technical. Paying or refusing involves cybersecurity, ethics, compliance, and reputation. Every minute of hesitation can cost millions.
What Is a Ransomware Ransom and How It Works
Every ransomware attack ends with a demand for money. Hackers request payment — often in cryptocurrency — in exchange for a decryption key or a promise not to leak stolen data. This is not random crime but a structured business model built on extortion.
The Ransomware-as-a-Service Economy
In recent years, Ransomware-as-a-Service (RaaS) has exploded. Malware creators lease their platforms to “affiliates” who carry out attacks and share profits. This structure has made ransomware accessible even to criminals with minimal technical skills.
According to Europol’s Internet Organised Crime Threat Assessment (IOCTA) 2025, ransomware now accounts for over 60% of all organized cybercrime operations worldwide. Behind each attack stands a network of developers, negotiators, money launderers, and risk analysts.
Andrea Baggio, CEO of HelpRansomware, explains:
“Paying the ransom never solves the problem. It fuels a sophisticated criminal industry that reinvests every euro received into new, more targeted attacks.”
The Digital Extortion Cycle
The process follows a precise sequence: infiltration, data exfiltration, encryption, and ransom demand. The goal is not just to block files but to psychologically control the victim. Hackers use countdown timers, public threats, and intimidation to create urgency and force rapid payments.
According to the Verizon Data Breach Investigations Report 2025, ransomware is among the fastest-moving forms of attack: ransom demands are typically issued within days of infiltration, but the real cost is measured in years of lost trust, fines, and reputational damage.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
The Consequences of Paying the Ransom
Paying a ransom rarely guarantees data recovery — but it always funds future attacks. Each payment validates the attackers’ business model and perpetuates the criminal economy.
Legal and Geopolitical Risks
Many ransomware groups are linked to sanctioned entities. Paying them can violate international regulations such as the U.S. OFAC Advisory on Ransomware Payments or EU Regulation 2020/1998. Doing so may constitute an act of illicit financing and expose executives to criminal prosecution.
The Europol IOCTA 2024 confirms that a significant portion of ransomware proceeds flows into transnational money-laundering circuits through unregulated cryptocurrency wallets and exchange services — directly linking ransomware profits to organized crime networks.
The Illusion of Safety
Even when payment is made, there is no guarantee that the data will be restored or that stolen information will not be sold on the dark web.

In addition, paying often places victims on secret “cooperative lists” shared among cybercriminal gangs, making them more likely to be targeted again.
Alternatives to Payment: Prevention, Response, and Resilience
The best defense against ransomware is never needing to choose between paying and losing everything. Prevention and preparedness reduce the impact of any attack.
Building a Solid Response Strategy
After an attack, the first step is not to pay but to react strategically: isolate infected systems, notify authorities, and activate the incident response plan. Organizations must know in advance who to call and how to communicate.
Juan Ricardo Palacio, CoFounder & CEO America of HelpRansomware, stresses:
“Paying is the shortcut of desperation. A prepared company never has to choose between surrendering or failing — it knows how to react, recover, and continue operating.”
Regularly tested offline backups remain the most effective defense. According to the World Economic Forum’s Global Cybersecurity Outlook 2024, companies that conduct regular response drills reduce recovery time by up to 60%.
Training and Security Culture
Technology alone is not enough. Human error triggers 91% of ransomware incidents — a careless click or a weak password is often all it takes. Continuous training, phishing simulations, and multi-factor authentication are vital to building a truly resilient organization.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
Negotiation and Forensic Analysis
Many organizations, in panic, try to negotiate directly with attackers — a serious mistake. Hackers exploit emotional vulnerability to increase the ransom amount. Any negotiation should be handled by experienced legal and cybersecurity professionals who understand criminal behavior and regulatory limits.
After an incident, digital forensic analysis is essential to identify the entry point, assess the extent of damage, and prevent recurrence. HelpRansomware supports organizations in forensic investigation, data recovery, malware eradication, and secure reconstruction of IT infrastructure.

Toward a Culture of Digital Resilience
Paying a ransom is a reactive choice; building resilience is a strategy. Organizations must move from defense to proactive security, combining prevention, detection, and response.
The World Economic Forum’s Global Cybersecurity Outlook 2024 shows that companies with mature security cultures and regularly tested plans recover faster and sustain less financial loss.
Conclusion: Paying Is Never the Solution
Every payment strengthens the network that caused the attack. Paying might look like a shortcut, but it leaves deep scars in trust, legality, and reputation. HelpRansomware helps companies and institutions worldwide to break the ransomware cycle — from prevention and recovery to training and continuous response. Cybersecurity is not a cost: it is the foundation of digital freedom.
Frequently Asked Questions (F.A.Q.)
No. Attackers often fail to deliver valid decryption keys or retain stolen data for future extortion.
In many jurisdictions, no — paying sanctioned entities can amount to financing organized crime.
You may lose some data, but you maintain legal compliance and avoid funding further attacks.
Offline backups, tested response plans, multi-factor authentication, and 24/7 network monitoring.
Fear of reputation loss and operational paralysis — but statistics show paying only worsens the long-term risk.
Through immediate technical response, forensic analysis, secure data recovery, and long-term resilience strategies.



