A message lands in your inbox. It looks like it’s from your software provider, your bank, or your IT department. The subject line is urgent, the wording persuasive, and it includes a link or an attachment. You click.
Nothing seems to happen. The screen doesn’t freeze. No warnings appear. You continue working. But what you don’t see is that, in the background, someone has just entered.
That click was enough to let the attacker in. Silently, they begin exploring your network, harvesting credentials, identifying critical files, and disabling backups. Days later, when your systems are locked and your documents encrypted, it’s already too late.
Ransomware rarely barges in with force. It sneaks in, taking advantage of a moment’s distraction and a well-crafted message. Its most common entry point remains one of the oldest tricks in the book: phishing.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
Why Is Phishing Still So Effective?
Phishing works because it doesn’t target systems — it targets people. Unlike other threats, it doesn’t need complex technical vulnerabilities or advanced malware. It just needs someone to trust what they see.
Attackers design messages that closely mimic real communications — from banks, payment platforms, public institutions, or coworkers. They use logos, signatures, formal tone, and specific data that make them credible. Today, they also harness AI to craft highly personalized emails, with natural language and no obvious errors.
This mix of urgency and familiarity can deceive even experienced users. In 2024, Proofpoint’s Threat Report revealed that 71% of organizations worldwide reported at least one successful phishing attack, despite having filters and training programs in place.
The reason isn’t simple carelessness. Many phishing campaigns are timed to coincide with key moments — right before a payment, during internal transitions, or disguised as security alerts. In high-pressure work environments, one click can change everything.
According to the UK’s National Cyber Security Centre (NCSC), phishing remains the most common attack vector in critical incidents reported by companies and public institutions. That’s because no technical system can fully eliminate the human factor.

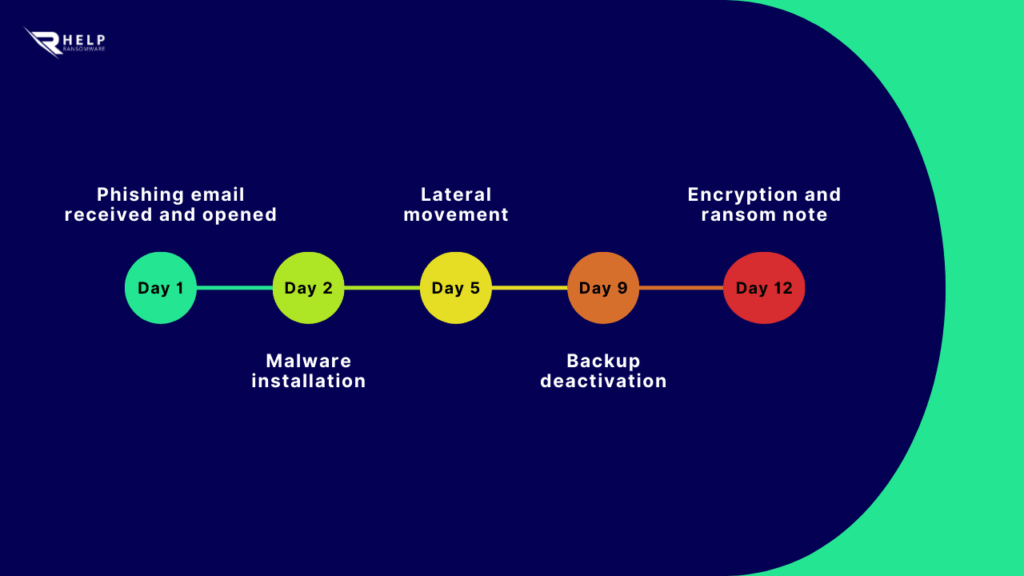
How the attack unfolds: from email to encryption
Phishing as a ransomware vector is as simple as it is effective. A single email, if well designed, can trigger a chain of actions that completely block access to your data. And the most dangerous part? It often happens without raising any red flags.
Typically, the attack follows this pattern:
- The attacker sends an email that mimics a legitimate message — an invoice, IT support note, or banking alert — often including a link or attachment.
- Upon clicking, a malicious file is installed, usually through a Word or Excel document with macros enabled or via a fake website that captures login credentials.
- Once access is gained, a dropper or backdoor is installed. This software allows the attacker to maintain undetected, persistent access.
- Over the next few days, the attacker moves through the network, identifies vulnerabilities, extracts sensitive data, and disables backups.
- Finally, the ransomware is deployed. Files become inaccessible, and a ransom note appears.
This process can unfold without detection by traditional security systems. According to the U.S. Cybersecurity and Infrastructure Security Agency (CISA), malware can remain hidden inside a network for 70 to 200 days before activating, using that time to maximize damage.
How to spot a phishing email
Detecting a phishing email isn’t always easy, especially when it’s well-crafted. However, there are warning signs that—if recognized and consistently practiced—can make the difference between a safe click and a critical breach.
Here are the key elements to watch out for:
Urgent or alarming subject lines
Phrases like “Final warning,” “Suspicious activity detected,” or “Your account will be suspended today” are designed to create psychological pressure. The more urgent the message, the more likely it’s a scam.
Senders impersonating real identities
Attackers often use domains that closely resemble those of legitimate companies (e.g., @micros0ft.com instead of @microsoft.com). They may also impersonate colleagues or supervisors using names found in past data leaks or professional networks.
Out-of-context attachments or links
If you receive a document you weren’t expecting, or a link that redirects you to a page asking you to log in again, be cautious. Many attacks begin with Word or Excel files that request enabling macros to “view the content.”
Links that don’t match the visible URL
Hover your cursor over the link (without clicking). If the actual destination doesn’t match what’s displayed, or it leads to unfamiliar domains or URL shorteners, it’s very likely a phishing attempt.
Subtle typos or formatting errors
Though less frequent today, spelling mistakes, awkward phrasing, or layout inconsistencies still serve as warning signs. AI-generated language may also sound unnatural or overly generic.

Effective strategies to protect against phishing
Avoiding phishing isn’t just about individual caution — it requires a comprehensive approach that combines technology, training, and organizational structure. The companies best equipped to withstand ransomware are those that act preventively, not reactively.
Here are the most effective measures:
1. Ongoing training with real simulations
Yearly training isn’t enough. Staff should regularly practice with realistic phishing simulations. These campaigns help assess organizational vulnerability and reinforce a culture of awareness.
According to KnowBe4’s Phishing by Industry Benchmarking Report 2025, organizations that implemented monthly training and weekly simulations reduced their vulnerability rate by 96% in one year.
🔗 Learn how to prepare your team with our cybersecurity training service.
2. Multi-Factor Authentication (MFA)
Even if an attacker steals passwords through phishing, they won’t be able to access systems without a second layer of verification. Enabling MFA on all accounts—especially email, VPNs, and admin panels—is a crucial barrier against intrusions.
Microsoft reports that MFA blocks over 99% of unauthorized login attempts on compromised accounts.
3. Advanced email filtering
Basic filters don’t catch today’s sophisticated phishing attempts. Modern solutions must use behavioral analysis, domain reputation, and machine learning to detect suspicious patterns. Filters should also scan attachments in sandbox environments before opening.
4. Access policies and network segmentation
Restricting user access to only the systems they need minimizes the attack surface. If an employee falls for a phishing attempt, the damage is contained if they don’t have elevated privileges or access to the entire network. Segmentation also prevents ransomware from easily spreading from one server to another.
5. Offline and tested backups
Having backups isn’t enough—they must be offline (air-gapped), regularly tested, and protected from automatic overwrites. Many modern ransomware variants search for and delete backups before encrypting files. Recovery is only possible if the backup is completely isolated.
Frequently Asked Questions (FAQ)
Not 100%, but the risk can be drastically reduced. Human behavior is unpredictable, but with continuous training, MFA, and advanced detection systems, most attempts can be stopped before they cause damage. The key is to combine technology with a strong security culture.
Some of the most common in recent phishing campaigns include LockBit, BlackCat (ALPHV), and Ragnar Locker. They all follow a dual logic: encrypting files and exfiltrating data to pressure victims into paying. These groups often tailor their campaigns to specific sectors and regions, using carefully personalized emails as their entry vector.
No. While it’s still useful as a basic layer of defense, antivirus software alone doesn’t detect sophisticated phishing emails or stop lateral movements within the network. Today, it’s essential to have complementary solutions like EDR, advanced email filters, and most importantly, a well-defined incident response strategy.
Yes. At HelpRansomware, we go beyond recovery. We design custom prevention plans, run phishing simulations for team training, and audit infrastructures to detect potential vulnerabilities before they’re exploited.
Conclusion: shut the door before they enter
No organization is completely safe from ransomware, but many can avoid becoming victims. The difference lies in whether action is taken before the first click or after the chaos.
Phishing operates on a simple logic: exploiting trust. It doesn’t require sophisticated technical vulnerabilities; it just needs someone to believe they’re doing the right thing. And that seemingly small opening is what allows ransomware to cause large-scale damage.
In this context, prevention isn’t optional—it’s strategic. Combining continuous education, access controls, alert systems, strong backups, and advanced security tools is what enables organizations to contain the threat from the start.
At HelpRansomware, we work to ensure that no company has to face these types of attacks alone. From preparation to recovery, our team provides targeted solutions against phishing, ransomware, and data loss.



