Current cybersecurity trends confirm a reality already familiar to technical teams: the most widely used and trusted technologies often become the most attractive targets for attackers. In recent days, several critical alerts have been published affecting both modern development frameworks and services monitored at the European institutional level.
React Server Components is a React technology designed to allow part of a web application’s functionality to run directly on the server, improving performance and user experience.
It is commonly used in digital platforms, enterprise applications, online services, and cloud environments, where efficiency and scalability are key. Because it operates on the server side and is connected to internal data, sessions, and integrations, any vulnerability in this component can significantly expand the attack surface.
Additionally, the European Union CERT‘s Security Advisory 2025-041 acts as an institutional alert aimed at public and private organizations, warning of risks affecting widely used critical services and dependencies, and underscoring the importance of reviewing configurations, updates, and security controls before these weaknesses can be exploited.
These warnings fit a recurring pattern: the exploitation of common components as an initial entry point into more complex campaigns, including current ones. Ransomware attacks that are defining the threat landscape in 2025.
Critical vulnerabilities in React Server Components: when the backend becomes the main risk vector
React published its first official advisory regarding a vulnerability that directly affects the execution of logic on the server, which could have a potential impact on sensitive data, active sessions, and internal integrations.
A few days later, the React team itself expanded the alert with a second statement, Denial of Service and source code exposure in React Server Components, which details additional risks such as denial of service and source code exposure in certain vulnerable configurations.
This chain of warnings reinforces a clear conclusion: problems in server-side components should not be considered isolated failures, but indicators of a wider attack surface.
Based on HelpRansomware’s experience, this type of vulnerability fits with the initial phases described in ransomware hacker tactics, where silent access and persistence precede the final impact.
Furthermore, when these applications rely on shared infrastructure or cloud services, the impact can be amplified rapidly, as seen in recent incidents such as the AWS global incident.

CERT-EU Advisory 2025-041: From technical vulnerability to European systemic risk
When a supranational CERT issues an alert of this level, it is usually because the conditions for exploitation already exist or could materialize rapidly. As digitalization progresses faster than hardening cycles, these advisories become an early indicator of large-scale incidents.
Why these warnings are especially critical in the European context
There is a sustained increase in Ransomware in the European Union is increasingly targeting essential services, public bodies, and strategic companies. In this context, CERT-EU warnings typically anticipate:
- Automated exploitation of reusable vulnerabilities
- Cross-cutting impact across different countries and sectors
- Regulatory and reputational risk
- Significant operational disruptions

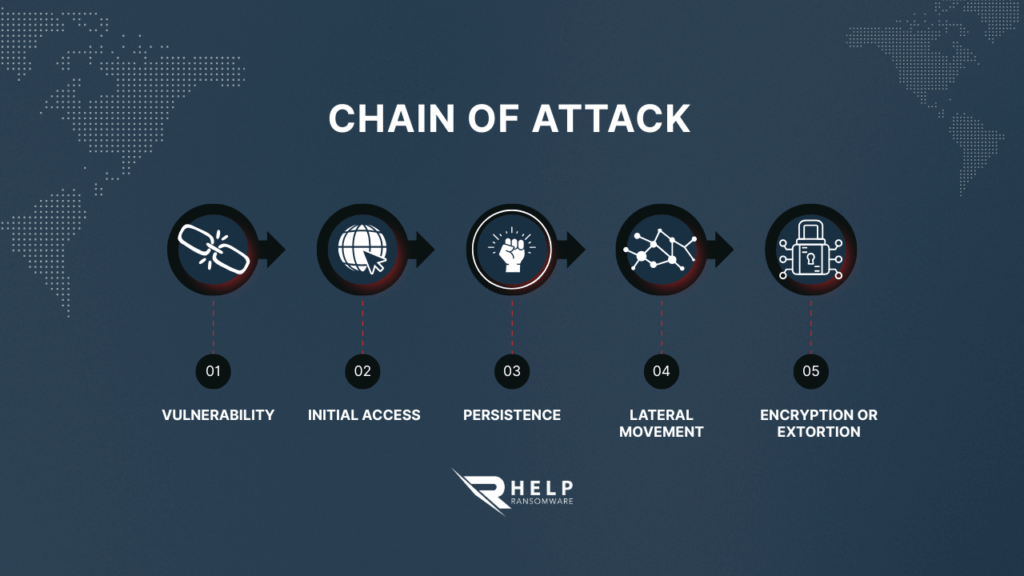
From technical failure to ransomware: how a modern attack chain is built
In most incidents analyzed by HelpRansomware, technical vulnerabilities are not the ultimate goal, but rather the first link in a progressive attack chain. From initial access, attackers seek persistence, privilege escalation, and lateral movement before executing the final attack.
This pattern has been observed in campaigns attributed to actors such as Qilin and other groups operating within a Global ransomware crisis. Exploiting critical frameworks and services allows attackers to prepare the environment before activating encryption or multiple extortion attempts.
Global impact and particularly exposed sectors
The impact of these vulnerabilities is not limited to a specific type of organization. When a widely used technology has security flaws, attackers exploit them as a repeatable entry point, combining them with human error, misconfigurations, or a lack of access control.
This pattern reinforces what was analyzed in Ransomware 2025: The Human Factor, where most incidents don’t begin with sophisticated techniques, but with everyday decisions that go unnoticed until the damage is already done.
Meanwhile, industrial systems continue to be a priority target for ransomware groups, especially when there is a connection between operating and technological systems. The difficulty of applying immediate patches and the need to maintain operations make cases like those analyzed in [reference missing] particularly prevalent. Siemens industrial safety reflects why this type of infrastructure requires a proactive and constant safety approach.
Urgent action: reduce exposure before it’s too late
Given this scenario, mitigation must be immediate and strategic. It is not enough to correct a single vulnerability; it is necessary to review the entire attack surface.
Priority actions:
- Verify the use of React Server Components and apply the official fixes published by React.
- Audit exposed dependencies, configurations, and services.
- Monitor for anomalous access and suspicious activity.
- Review response plans and backups.
- Take extra precautions during high-risk periods such as Black Friday.
Conclusion
The alerts published this week reinforce a clear conclusion: critical vulnerabilities in widely adopted technologies remain the most frequent entry point for advanced attacks. In an environment of high technological dependence, security must be addressed preventively, comprehensively, and continuously.
HelpRansomware, an INCIBE-approved company, reminds us that anticipation, visibility, and early detection remain the most effective defense against modern ransomware.



