Ransomware is no longer a sudden threat: it has become an industrialized criminal process, managed by structured groups that behave like actual companies.
In 2025, ransomware attacks no longer arise from a simple infected attachment, but from a complex chain of coordinated actions: identity theft, supplier compromise, psychological manipulation of employees, and automated attacks powered by artificial intelligence.
These groups—LockBit, BlackCat/ALPHV, Cl0p, Akira, and many others—operate as global networks with distinct roles: malware developers, access brokers, and affiliate groups that rent infrastructure.
This decentralized model increases the speed of attacks and reduces visibility into operations, while the final stage of the process (extortion) is just the tip of the iceberg.
According to Black Kite’s Global Ransomware Report 2025, over 70% of modern ransomware attacks begin with an entry point tied to digital identities or cloud services.
“Heavy” malware is no longer necessary: a compromised credential, an OAuth token, or a third-party account is enough to grant access to entire infrastructures.
The consequence? Hackers no longer aim to simply “crash” your systems, but to compromise the very trust your company relies on: customers, data, reputation, and business continuity. In other words, ransomware is now a business threat, not just an IT threat.
In this scenario, companies must update their defenses: antivirus or backup isn’t enough. Visibility, resilience, and a coordinated response are essential.
So let’s look at the 5 real, documented, covert tactics hackers are using in 2025 to target the most sophisticated businesses, and how you can neutralize them before it’s too late.

Exfiltration-based extortion: “without/before encryption”
Traditionally, ransomware aimed to encrypt systems and demand a ransom. Today, however, the prevalent approach is to steal data, threaten to publish it, and sometimes encrypt it. This approach is faster, quieter, and leverages your company’s image and reputation.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
Why it works
The logic behind extortion based on exfiltration is simple and brutal: stealing and threatening to publish sensitive information gives attackers an immediate lever over a company’s reputation, often far more effective (and quicker) than full system encryption.
Criminal actors have realized that it is not necessary to paralyze an infrastructure to achieve their goal — it is enough to appropriate valuable data (contracts, executive emails, customer records) and use it as a tool for public pressure or as merchandise to sell on the dark web.
This tactic is also effective because it drastically reduces operational “noise”: well-planned exfiltration can happen stealthily, whereas large-scale encryption tends to trigger immediate alerts and rapid SOC responses.
As a result, the so-called dwell time — the interval between initial compromise and the extortion action — has shortened significantly; in some documented cases attackers moved from compromise to extortion demand within hours, not days or weeks.
This compressed rhythm leaves less room for detection and traditional containment processes.
Finally, the variety of exfiltration channels (cloud, external repositories, file-transfer services, third-party accounts) and the spread of public leak sites make data extortion a fast, repeatable option for criminal groups: a single spectacular “big hit” is no longer required; instead, attackers can run a systematic collection-and-exploitation strategy across many victims.

Practical countermeasures
- Monitor and block exfiltration activity: large uploads to external clouds, endpoints that begin transferring large amounts of unusual data.
- Segmentation of sensitive data: limited access, separate logs, “zero-trust” for critical repositories.
- Verified and isolated backups: have air-gapped copies, periodically tested, with versioning and integrity checking.
- Incident response plan that includes the risk of “data publication” (not just “system recovery”).
Automation and AI at the Attacker’s Service: Spear-phishing 2.0 and Advanced Social Engineering
Attackers are evolving rapidly. They’re no longer limited to sending generic mass emails: thanks to artificial intelligence (AI), generative models, deep-fake audio/video, and automation tools, phishing and social engineering campaigns are becoming more targeted, credible, and difficult to detect.
ENISA-2025 report indicates that AI-assisted phishing campaigns account for over 80% of observed social engineering activities.
According to data from the Anti-Phishing Working Group (APWG), in the first quarter of 2025 the number of registered phishing attacks exceeded one million cases, confirming a strong growth in the number and sophistication of tools.

Immediate Ransomware Help
Don’t let ransomware hold your business hostage. Our experts are ready to recover your data and secure your systems.
Digital Identities and Credential Theft—The New Attack Perimeter
Identity as a weapon
Today, attackers aim to impersonate legitimate users. They steal session cookies, OAuth tokens, and API keys to gain seamless and invisible access. As the NIST Zero Trust Maturity Model indicates, identity management is now the first line of defense.
Effective prevention
Reducing privileges according to the principle of least privilege, monitoring tokens and sessions, implementing strong MFA, and disabling static credentials are essential steps. Privileged access should be temporary ( just-in-time ) and tracked. CISA guidelines recommend ongoing audits of external identities and vendors.
Supply chain and third parties — the indirect attack
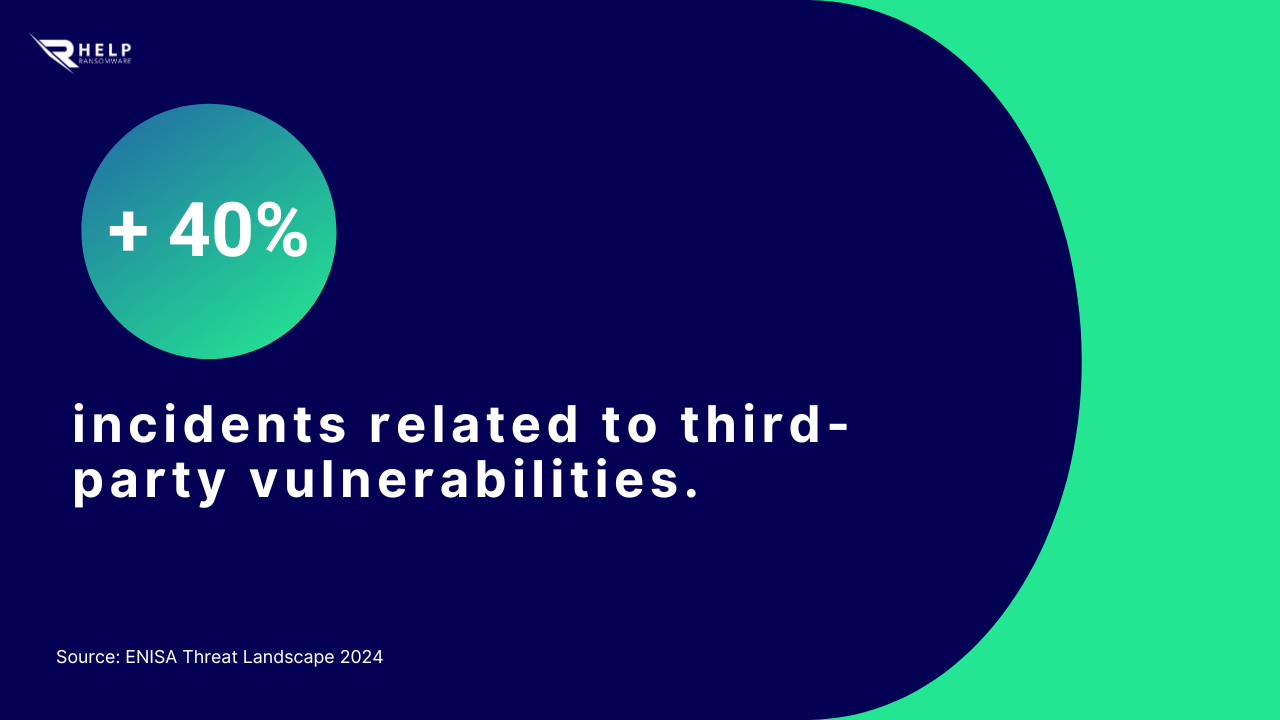
An underestimated risk
Most companies work with a network of digital providers: management systems, cloud platforms, IT services. A single compromised partner can become the entry point for the entire chain.
Defense strategies
Zero Trust model, with continuous authentication and network segmentation, is now essential.
Each vendor must meet security SLAs, patch management, and MFA. As recommended by Europol IOCTA 2024, simulated compromise tests ( supply chain red teaming ) must be integrated to evaluate the effectiveness of shared defenses.
Legitimate Tools and Infostealers — The “Living-off-the-Land” Tactic
An invisible threat
Modern hackers use legitimate tools already present in systems (PowerShell, RDP, WMI) to operate undetected.
Added to this are infostealers, software capable of stealing passwords and cookies to log in with authentic identities.
ENISA classifies this type of attack as among the most difficult to detect, because the actions appear perfectly legitimate.
Defense and Response
Implementing EDR solutions with behavioral analysis, limiting the use of administrative tools on clients, and segregating critical access are key measures.
The Carnegie Mellon SEI highlights that the ability to recognize behavioral deviations is now more useful than simply detecting malware signatures.
How HelpRansomware helps businesses fight these threats
Addressing these five tactics requires a multi-level strategy: technology, processes, and training.
This is where HelpRansomware services makes the difference.
We help businesses build truly operational security that goes beyond simple prevention.
From ransomware protection with ransomware consulting to cybersecurity training with advanced phishing simulations, every intervention is designed to reduce the human factor as an entry point.
HelpRansomware also assists with backup management and data recovery after an attack, ensuring business continuity, and provides 24/7 monitoring and incident response services thanks to its SOC experts and analysts.
Each intervention is personalized, with the aim of preventing, containing, and neutralizing attacks before they cause irreversible damage.
Conclusion
The ransomware of 2025 is no longer measured in encrypted gigabytes, but in compromised trust.
Attacks are intelligent, rapid, and invisible. Modern defense isn’t just technological: it’s cultural, strategic, and requires reliable partners.
With integrated prevention, monitoring and response solutions — and a security-focused corporate culture — every enterprise can turn the ransomware threat into an opportunity to strengthen its digital resilience.
Frequently Asked Questions (F.A.Q.)
No. But it can be drastically reduced with ongoing training, MFA, and verification procedures. Structured programs reduce the risk by up to 80% within six months.
LockBit, BlackCat/ALPHV, and Akira remain among the most aggressive, but new groups specializing in unencrypted extortion are emerging. (Sources: Europol IOCTA 2024 | ENISA TL 2024)
No. Antivirus is just one layer of defense. You need EDR, strong authentication, verified backups, and tested response plans.